KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Ransomware gangs increasingly purchase access to a victim’s network on dark web marketplaces and from other threat actors. Analyzing their want ads makes it possible to get an inside look at the types of companies ransomware operations are targeting for attacks.
When conducting a cyberattack, ransomware gangs must first gain access to a corporate network to deploy their ransomware.
With the massive profits being generated in attacks, instead of finding and breaching targets themselves, ransomware gangs are commonly purchasing initial access to high-value targets through initial access brokers (IABs).
IABs are other threat actors who breach a network, whether through brute-forcing passwords, exploits, or phishing campaigns and then sell that access to other cybercriminals.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
After examining ransomware gang’s “want ads,” cybersecurity intelligence company KELA has compiled a list of criteria that the larger enterprise-targeting operations look for in a company for their attacks.
KELA analyzed 48 forum posts creates in July where threat actors are looking to purchase access to a network. The researchers state that 40% of these ads are created by people working with ransomware gangs.
These want ads list the company requirements that ransomware actors are looking for, such as the country a company is located, what industry they are in, and how much they are looking to spend.
For example, in a want ad from the BlackMatter ransomware gang, the threat actors are looking for targets specifically in the USA, Canada, Australia, and Great Britain with revenue of $100 million or more. For this access, they are willing to pay $3,000 to $100,000, as shown in the want ad below.
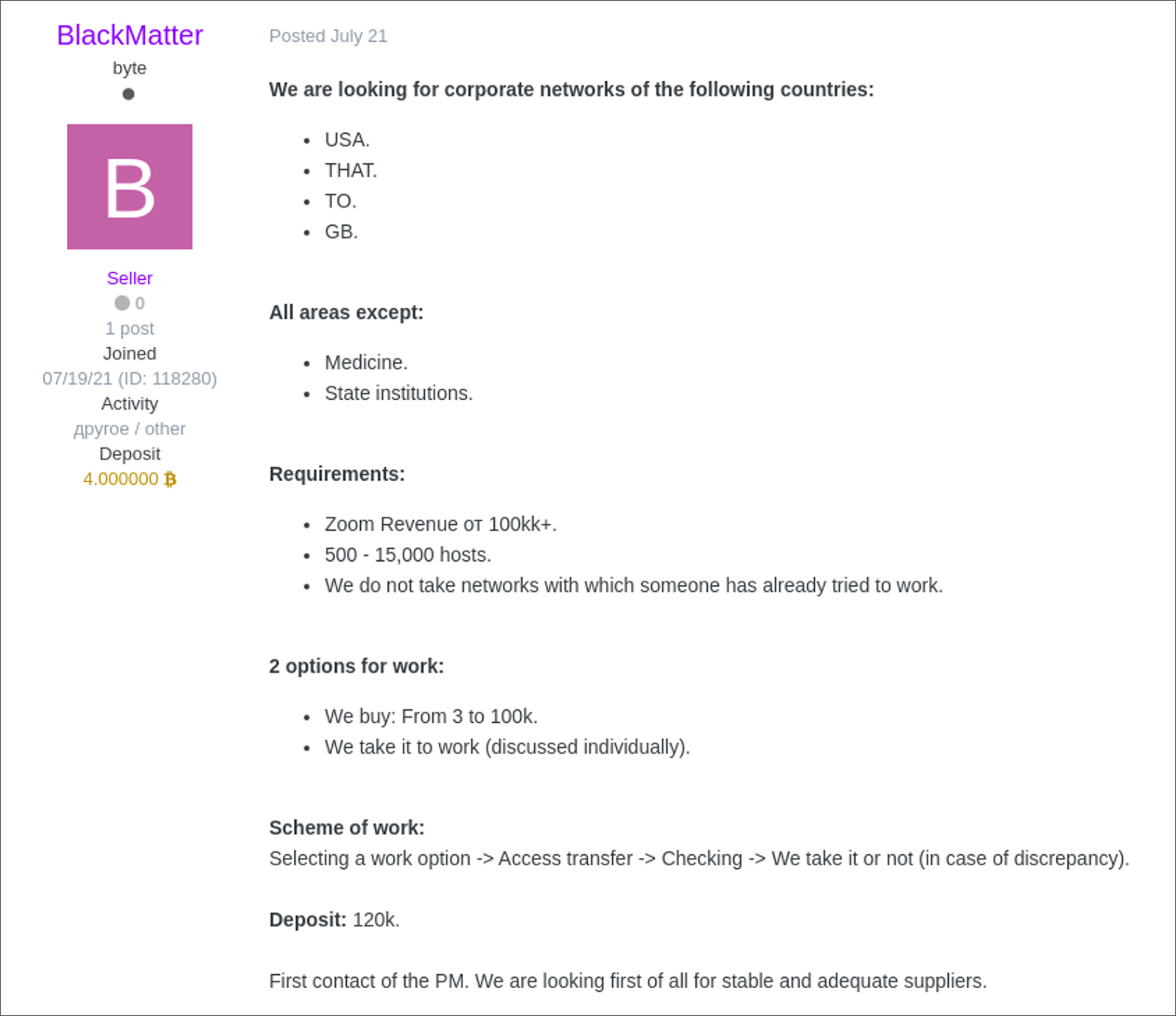
By analyzing the want ads from close to twenty posts created by threat actors related to ransomware gangs, the KELA researchers were able to come up with the following company characteristics that are being targeted:
Unfortunately, even if a company does not meet the above criteria, it does not mean that they are safe.
Many ransomware gangs, such as Dharma, STOP, Globe, and others, are less picky, and you can wind up being targeted by a ransomware operation.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
Furthermore, even though these gangs prefer victims with these characteristics, it does not necessarily mean they won’t breach a network independently.
BleepingComputer has commonly seen ransomware gangs, such as DarkSide, REvil, BlackMatter, and LockBit, target smaller companies and demand much smaller ransoms.