KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Ragnar Locker ransomware group is warning that they will leak stolen data from victims that contact law enforcement authorities, like the FBI.
Ragnar Locker has previously hit prominent companies with ransomware attacks, demanding millions of dollars in ransom payments.
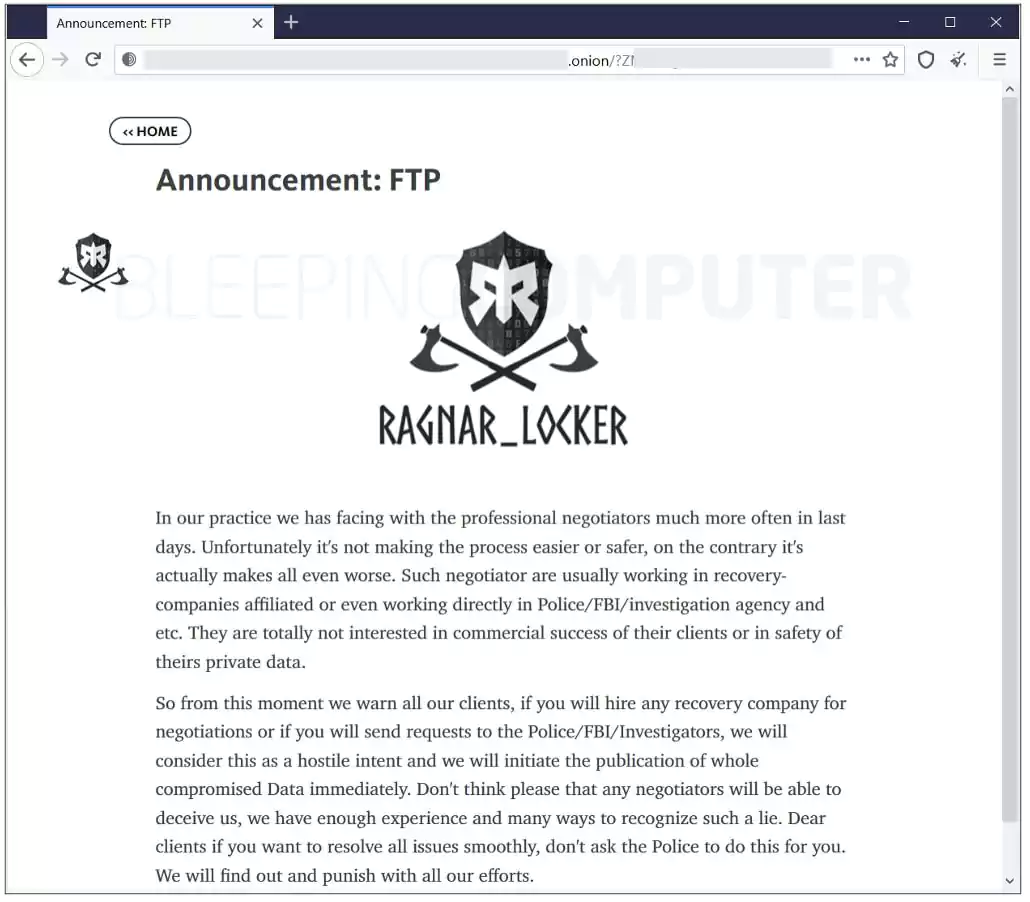
In an announcement published on Ragnar Locker’s darknet leak site this week, the group is threatening to publish full data of victims who seek the help of law enforcement and investigative agencies following a ransomware attack.
The threat also applies to victims contacting data recovery experts to attempt decryption and conduct the negotiation process.
In any such event, the group will publish the victim’s full data on their .onion site.
The ransomware operator states that victim organizations who hire “professional negotiators” are only making the recovery process worse. That’s because such negotiators are often working with data recovery companies affiliated with the FBI and similar authorities.
Also Read: Data Centre Regulations Singapore: Does It Help To Progress?
“So from this moment we warn all our clients, if you will hire any recovery company for negotiations or if you will send requests to the police/FBI/investigators, we will consider this as a hostile intent and we will initiate the publication of whole compromised data immediately,” reads the note seen by BleepingComputer on the group’s data leak site:
Ragnar Locker actors are known for manually deploying the ransomware payloads to encrypted the victims’ systems. They spend time conducting reconnaissance to discover network resources, company backups, and other sensitive files they can steal before the data encryption stage.
As reported by BleepingComputer, Ragnar Locker’s past victims have included Japanese game maker Capcom, computer chip manufacturer ADATA, and aviation giant Dassault Falcon.
In Capcom’s case, the group had reportedly encrypted 2,000 devices on the organization’s network and demanded an $11,000,000 ransom in exchange for a decryptor.
The latest announcement by Ragnar Locker puts additional strain on victims, considering in the current environment of growing cyber-attacks, governments worldwide have strongly advised against paying ransoms.
“Government has a strong position against paying ransoms to criminals, including when targeted by ransomware. Paying a ransom in response to ransomware does not guarantee a successful outcome,” said the British Home Secretary, Priti Patel in May this year.
The FBI does not support paying ransoms either as doing so is not guaranteed to protect networks from data leaks or future attacks. Ransomware victims are instead encouraged to contact the local FBI field office.
Also Read: What Is A Governance Framework? The Importance And How It Works
Paying ransom amounts motivates criminals to target even more victims and incentivize other cybercrime groups to follow their lead in conducting illegal activities.