





Babuk Locker ransomware operators have leaked personal files belonging to police officers from the Metropolitan Police Department (also known as MPD or DC Police) after negotiations went stale.
The documents published on Babuk Locker’s dark web leak portal include 150 MB worth of data from DC Police officers’ personal files.
“The negotiations reached a dead end, the amount we were offered does not suit us, we are posting 20 more personal files on officers, you can download this archive, the password will be released tomorrow,” Babuk Locker said.
The ransomware gang claims the data was leaked because the amount of money the DC Police was willing to pay did not match Babuk Locker’s ransom demands.https://www.ad-sandbox.com/static/html/sandbox.html
Babuk Locker added that all the data would be leaked if the DC Police is unwilling to match their demands. “If during tomorrow they do not raise the price, we will release all the data,” the ransomware operators said.
BleepingComputer has not been able to independently verify if the ransomware gang’s claims are true or if the DC Police offered to pay any ransom.

Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
“At the request of the Metropolitan Police Department, the FBI is assisting with its investigation,” DC Police spokesperson told BleepingComputer earlier today.
“The FBI routinely supports our law enforcement partners by providing investigative support and specialized resources when requested. All further questions should be directed to DC government.”
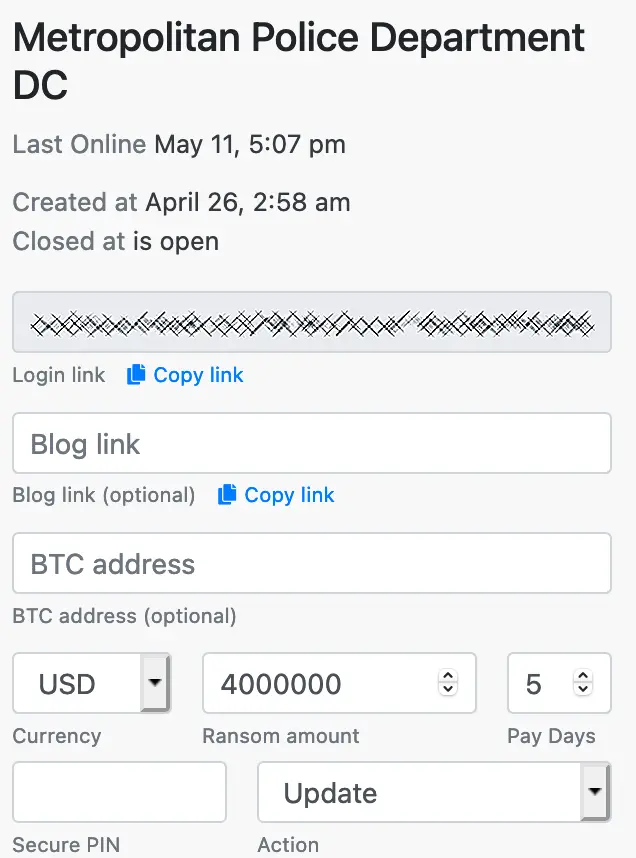
In an update to the Babuk data leak site leaking a second set of password-protected files, the threat actors released screenshots that they claim were from negotiations between them and the DC Police.
These chat screens show that the ransomware gang demanded $4 million from the MPD, who counter-offered with $100,000.
Based on the statement provided by the MPD, it may have been the FBI performing the negotiation or a third-party ransomware negotiation service.
Last month, when MPD confirmed the attack, Babuk Locker said they had compromised the DC Police’s networks and stolen 250 GB of unencrypted files.
At the time, the ransomware gang also posted screenshots of folders containing data allegedly stole during the breach.
The folders’ names point to internal files related to police operations, investigation reports, disciplinary records, as well as files related to gang members and ‘crews’ operating in DC.
DC Police told BleepingComputer the breach is under investigation to determine the full impact. The police department has also engaged the FBI to help them investigate the incident.
Last month, Babuk Locker also breached the NBA’s Houston Rockets network, which was transparent about the ransomware attack.
Surprisingly, the ransomware gang suddenly took down stolen Houston Rockets data from their site after leaking it.
After disclosing their attack on DC Police’s network, Babuk Locker operators posted and deleted two announcements about plans to shut down operations and open-source the ransomware.
One day later, the ransomware gang said that they would instead close their affiliate program and move to an extortion-only model which does not rely on encrypting victims’ systems after stealing sensitive data.
This move might have also been prompter by bugs affecting Babuk Locker’s decryptor discovered by cybersecurity firm Emsisoft, bugs that could destroy the victims’ files while they were being decrypted and, potentially, lead to revenue losses for the gang in the future if victims’ would’ve refused to pay ransoms.
Babuk Locker started operating in January when they also began leaking data stolen from their targets on hacker forums and later on their data leak portal.
Also Read: Data Protection Officer Singapore | 10 FAQs
Since then, the ransomware gang has slowly expanded its operations as they recruited more affiliates to compromise even more enterprise networks.
Update: Added DC Police statement.
Update 2: Added info on negotiation screenshots leaked by Babuk.