KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Business jet maker Bombardier is the latest company to suffer a data breach by the Clop ransomware gang after attackers exploited a zero-day vulnerability to steal company data.
Bombardier is one of the worlds leading manufacturers of business jets that employs 16,000 people and generated $6.5 billion in revenue for 2020.
This week the Clop ransomware operation posted files stolen from Bombardier on their data leak site. This data includes design airplane and parts schematics and flight test reports.
Soon after BleepingComputer contacted the company about the data leak, Bombardier issued a press release stating that they suffered a breach after hackers stole data from their “file-transfer application.”
“An initial investigation revealed that an unauthorized party accessed and extracted data by exploiting a vulnerability affecting a third-party file-transfer application, which was running on purpose-built servers isolated from the main Bombardier IT network,” Bombardier disclosed.
In a subsequent email with Bombardier, the aviation company confirmed to BleepingComputer that the file-transfer application they reference is Accellion FTA. This secure file sharing application has been involved in a series of data breaches since December 2020.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
As part of this attack, Bombardier states that the attackers stole the personal and confidential data for employees, customers, and suppliers.
“Forensic analysis revealed that personal and other confidential information relating to employees, customers and suppliers was compromised. Approximately 130 employees located in Costa Rica were impacted. Bombardier has been proactively contacting customers and other external stakeholders whose data was potentially compromised,” says Bombardier in a cybersecurity breach advisory.
The company stresses that the Accellion FTA servers are isolated from the rest of the network and that the attackers did not gain access to any other systems.
Accellion FTA is a legacy, 20-years old file transfer service used by organizations to share sensitive files with people outside of their organization securely.
In December, a threat actor began exploiting a zero-day vulnerability in the Accellion FTA devices that allowed them to steal data stored on the servers.
When Accellion learned of the attackers, they released a security update on Christmas Day, but at that point, the threat actors had already compromised many organizations’ servers and stolen data.
Starting in February, the Clop ransomware gang began publishing data for victims whose Accellion FTA devices were breached. The companies leaked on Clop’s data leak site include Singtel, Jones Day, Fugro, Danaher, and ABS Group.
Other companies are known to have been breached but have not had their data leaked. These companies include supermarket giant Kroger, the QIMR Berghofer Medical Research Institute, Reserve Bank of New Zealand, the Australian Securities and Investments Commission (ASIC), and the Office of the Washington State Auditor (“SAO”).
Since the attacks on Accellion FTA devices started in December, BleepingComputer has been researching the data breaches and has been told by companies that they received ransom notes from the Clop ransomware gang.
These ransom notes were not left behind on systems like a ransomware attack but were sent instead via email to company employees.
Earlier this week, a report by incident response company Mandiant confirmed our suspicions that threat actors affiliated with the Clop ransomware gang were responsible for the attacks on the Accellion FTA devices.
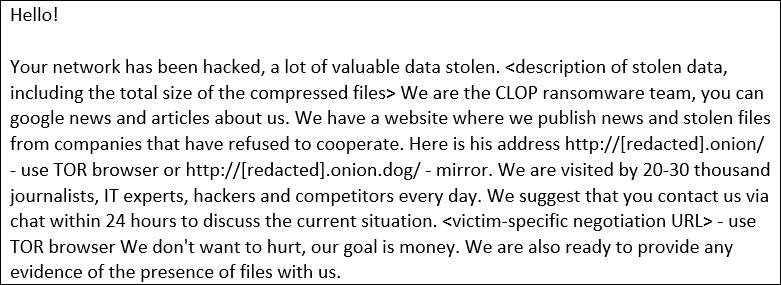
It is not clear if the Clop ransomware gang performed the attack themselves or if another hacking group partnered with them to use their data leak site.
BleepingComputer can confirm, though, that we were contacted earlier this month directly by the Clop ransomware gang to alert us to the posting of these breaches on their site.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
We should expect to see more Accellion FTA data breaches disclosed as the Clop ransomware gang post further stolen data to their website.