KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Network-attached storage device maker QNAP warns customers that some NAS storage devices running vulnerable versions of the QTS operating system are exposed to attacks attempting to exploit the critical Windows ZeroLogon (CVE-2020-1472) vulnerability.
“If exploited, this elevation of privilege vulnerability allows remote attackers to bypass security measures via a compromised QTS device on the network,” QNAP explains in a security advisory published on Monday.
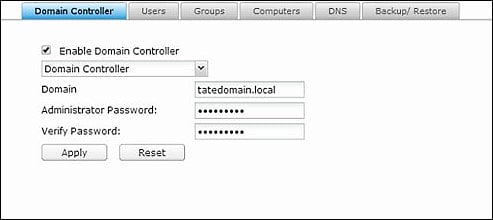
“The NAS may be exposed to this vulnerability if users have configured the device as a domain controller in Control Panel > Network & File Services > Win/Mac/NFS > Microsoft Networking.”
While NAS devices aren’t commonly used as a Windows domain controller, some organizations might want to use this feature to allow IT admins to use some NAS models to manage user accounts, authentication, and enforce domain security.
Given that NAS devices can’t be set up as domain controllers if an LDAP server is already running, NAS LDAP servers are by default secured from attacks using ZeroLogon exploits.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business
The company ‘strongly’ recommends QNAP customers to update the QTS operating system on their NAS devices together with all installed apps to defend against Zerologon attacks.
QNAP says that QTS 2.x and QES are not affected by the CVE-2020-1472 vulnerability and that it has already fixed the issue in these QTS versions:
To install the latest QTS update users have to go manually update the OS by downloading the update from QNAP’s Download Center or automatically by following this procedure:
To update all installed applications on their NAS, users have to go through the steps detailed in the advisory.
QNAP recently addressed two critical bugs in the Helpdesk app that could allow attackers to take over unpatched NAS devices and issued another security advisory warning of a recent surge in ransomware attacks targeting publicly exposed NAS devices.
Also Read: Intrusion Into Privacy All About Law And Legal Definition
ZeroLogon is a critical Windows vulnerability that allows attackers to gain domain administrator privileges and to take control over the entire domain.
Earlier this month, Microsoft has warned that both nation state-backed hackers and financially motivated cybercriminals have already started to use ZeroLogon exploits in their attacks.
Microsoft first alerted customers of ZeroLogon being actively exploited in attacks on September 23.
The Iranian-backed MuddyWater cyber-espionage group (also tracked as MERCURY and SeedWorm) also started abusing the flaw beginning with the second half of September.
TA505 (aka Chimborazo), a threat group known for distributing the Dridex banking trojan since 2014 and for being a conduit for the deployment of Clop ransomware in later stages of their attacks, was also spotted by Microsoft exploiting the ZeroLogon vulnerability.
On September 18, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) demanded the Federal Civilian Executive Branch to treat fixing the ZeroLogon flaw as “”an immediate and emergency action.”