





QNAP warns customers of ongoing attacks targeting QNAP NAS (network-attached storage) devices and urges them to enhance their security as soon as possible.
In these attacks, the threat actors use automated tools to login into Internet-exposed NAS devices using passwords generated on the spot or from lists of previously compromised credentials.
“Recently QNAP has received multiple user reports of hackers attempting to log in to QNAP devices using brute-force attacks – where hackers would try every possible password combination of a QNAP device user account,” the company warned.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
“If a simple, weak, or predictable password is used (such as ‘password’ or ‘12345’) hackers can easily gain access to the device, breaching security, privacy, and confidentiality.”
After guessing the right combination, they get full access to the targeted device, allowing them to gain access to and steal sensitive documents or deploy malware.
If the attackers fail to brute-force their way in, the NAS devices’ system logs will record the attempts and log them with “Failed to login” warning messages.
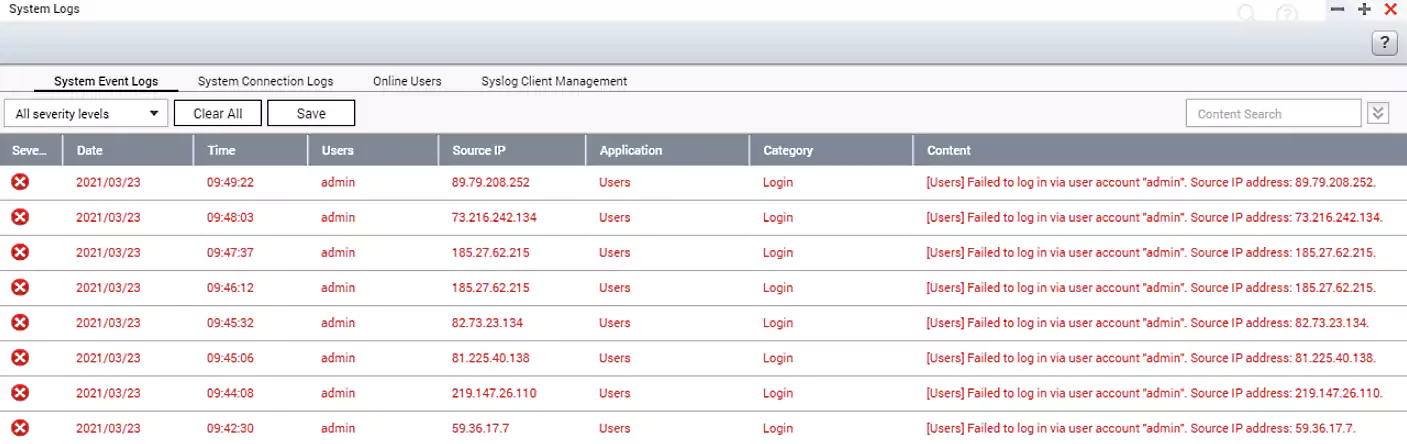
QNAP advises customers to secure their NAS devices by changing the default access port number, using strong passwords for their accounts, enabling password policies, and disabling the admin account targeted in these ongoing attacks.
Before disabling the admin account, you will first have to create a new system administrator account by going into Control Panel > Users.
You will then be able to disable the default ‘admin’ administrator account on QNAP NAS devices running QTS 4.1.2 or later versions, using the following steps:
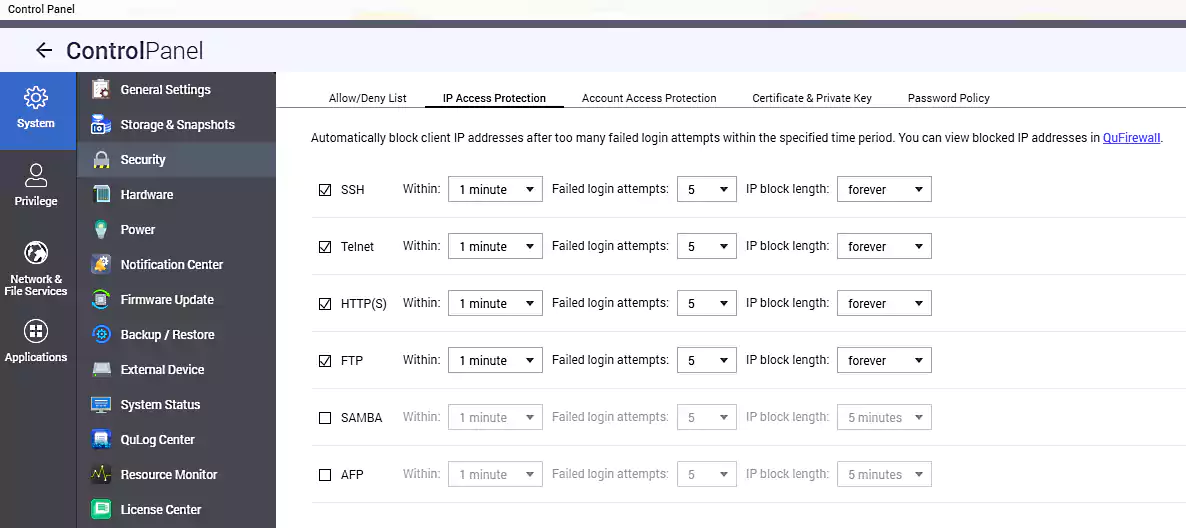
Furthermore, you can also configure the NAS device to automatically block IP addresses behind multiple numbers of ailed login attempts.
You can do this by customizing the device’s security settings from the NAS Control Panel > System > Security > IP’ Access Protection’ tab.
QNAP NAS owners should also go through the following checklist to secure their NAS devices and check for malware:
Threat actors regularly target NAS devices to steal sensitive documents or deploy info-stealing malware since they are usually used to backup and share sensitive files.
In June 2019, an eCh0raix Ransomware (aka QNAPCrypt) campaign also targeted QNAP NAS devices with weak passwords in brute-force attacks.
eCh0raix returned one year later, once again attempting to gain access to publicly-exposed QNAP devices by brute-forcing accounts with weak passwords or exploiting known vulnerabilities.
While a decryptor was released to decrypt files encrypted by some eCh0raix versions for free, the ransomware’s developer has since fixed the code weakness.
Also Read: Data Protection Officer Singapore | 10 FAQs
At the moment, there is no way to recover files for free unless you have enabled QNAP’s Snapshot service.