





QNAP warns customers of an actively exploited Roon Server zero-day bug and eCh0raix ransomware attacks targeting their Network Attached Storage (NAS) devices.
This warning comes only two weeks after QNAP users were alerted of an ongoing AgeLocker ransomware outbreak.
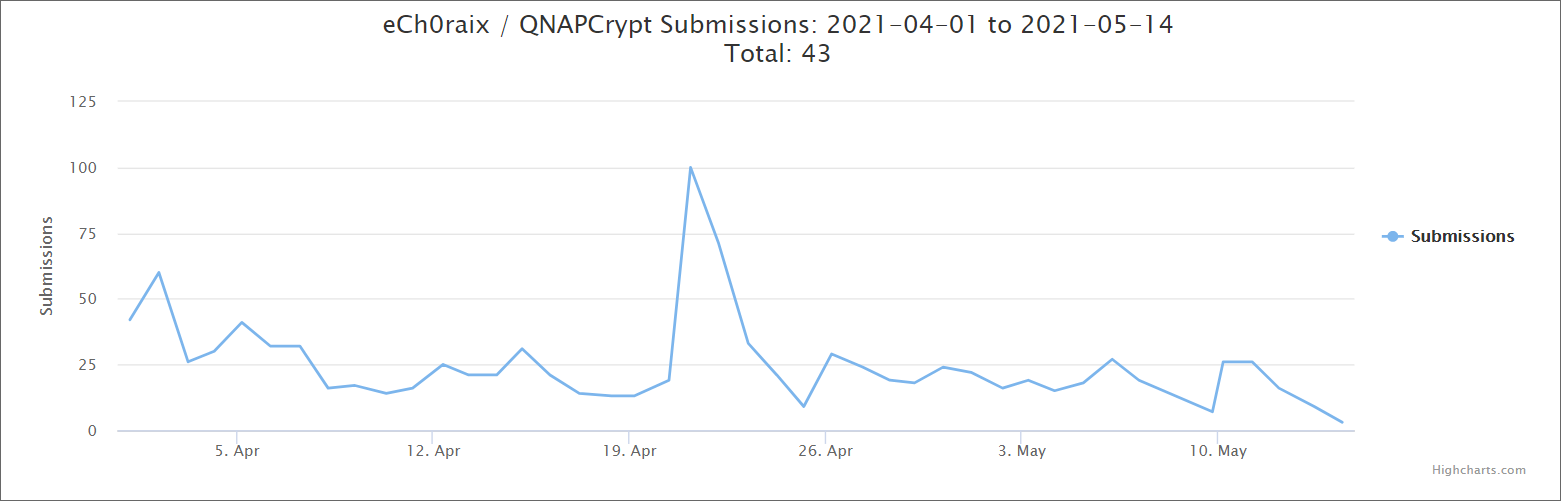
The Taiwan-based NAS appliance maker says that it has received reports of devices impacted by eCh0raix ransomware in a security advisory published today.
“The eCh0raix ransomware has been reported to affect QNAP NAS devices,” the company said. “Devices using weak passwords may be susceptible to attack.
QNAP urged customers to “act immediately” to protect their data from potential eCh0raix attacks by:
Detailed step-by-step instructions on changing your NAS password, enabling IP Access Protection, and changing the system port number are available in the security advisory.
While QNAP doesn’t mention how many reports it received from users directly affected by eCh0raix ransomware in the last weeks, BleepingComputer has seen an uptick in attack reports on the highly active eCh0raix support topic.
Also Read: The DNC Singapore: Looking At 2 Sides Better
Today, although not making a direct connection with the eCh0raix attacks, QNAP also warned of an actively exploited zero-day vulnerability impacting Roon Labs’ Roon Server 2021-02-01 and earlier versions.
The company recommends disabling the Roon Server music server and not exposing the NAS on the Internet to protect it from these active attacks until Roon Labs provides a security update.
To disable Roon Server on your NAS, you have to follow this procedure:
QNAP also fixed a command injection vulnerability in the Malware Remover app on Thursday.
This security flaw would allow remote attackers to execute arbitrary commands on devices running vulnerable app versions.
QNAP devices were previously targeted by eCh0raix ransomware (also known as QNAPCrypt) in June 2019 and June 2020.
A massive Qlocker ransomware campaign also hit QNAP devices starting mid-April, with the threat actors behind the attacks making $260,000 in just five days by remotely encrypting data using the 7zip archive program.
Additionally, QNAP removed a backdoor account (aka hardcoded credentials) in the HBS 3 Hybrid Backup Sync backup and disaster recovery app.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
It was later confirmed that Qlocker ransomware operators used the removed backdoor account to hack into some QNAP customers’ NAS devices and encrypt their files.
As mentioned in the beginning, AgeLocker ransomware also hit QNAP customers two weeks ago and in another campaign targeting publicly exposed NAS devices exploiting vulnerable Photo Station versions during September 2020.