KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







QNAP force-updated customer’s Network Attached Storage (NAS) devices with firmware containing the latest security updates to protect against the DeadBolt ransomware, which has already encrypted over 3,600 devices.
On Tuesday, BleepingComputer reported on a new ransomware operation named DeadBolt that was encrypting Internet-exposed QNAP NAS devices worldwide.
The threat actor claims to be using a zero-day vulnerability to hack QNAP devices and encrypt files using the DeadBolt ransomware, which appends the .deadbolt extension to file names.
The ransomware will also replace the regular HTML login page with a ransom note demanding 0.03 bitcoins, worth approximately $1,100, to receive a decryption key and recover data.
Also Read: Letter of Consent MOM: Getting the Details Right
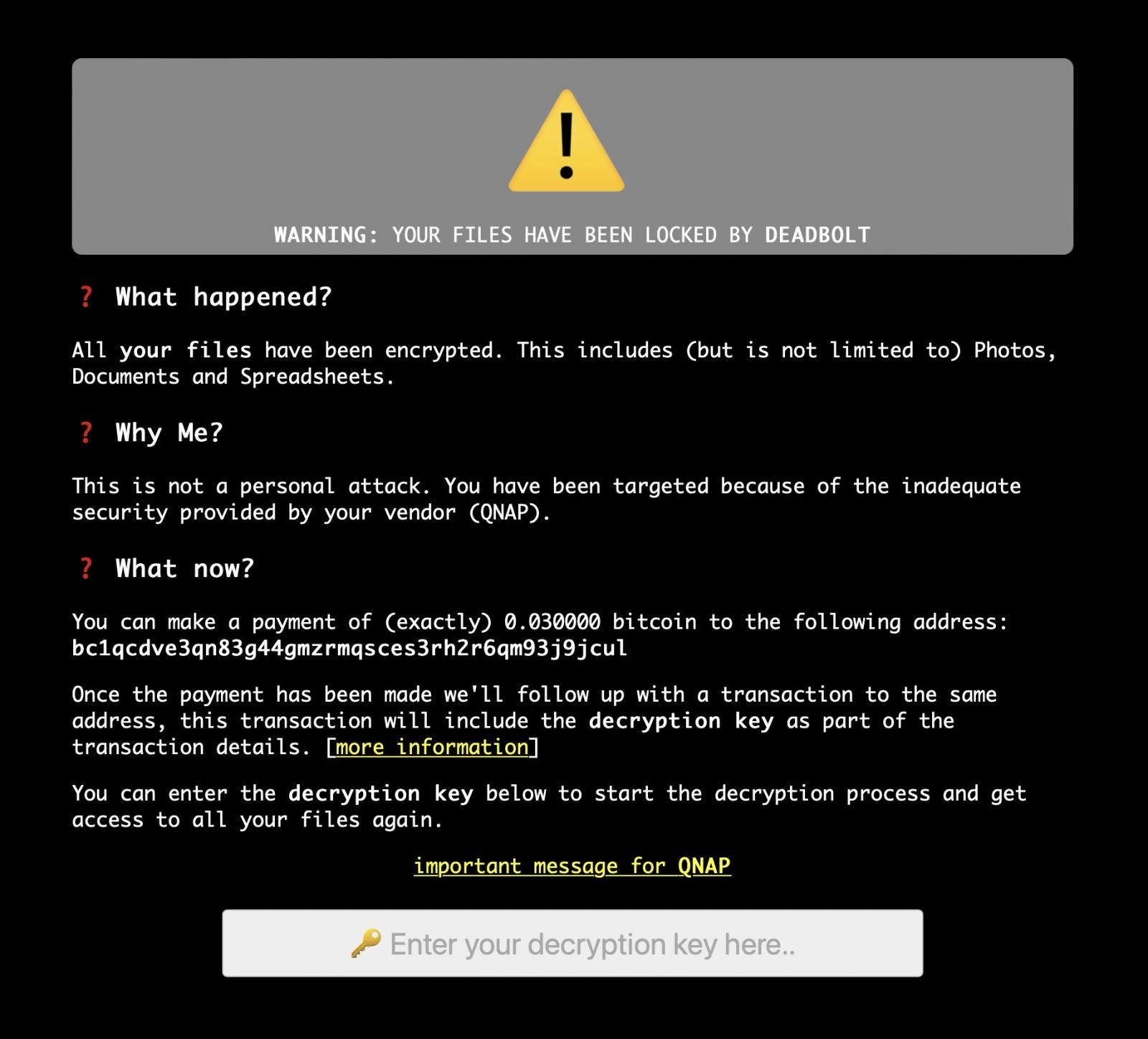
The DeadBolt ransomware gang is also trying to sell the full details of the alleged zero-day vulnerability to QNAP for 5 Bitcoins, worth $185,000.
They are also willing to sell QNAP the master decryption key that can decrypt all affected victims and provide information on the alleged zero-day for 50 bitcoins, or approximately $1.85 million.
While it is unlikely that QNAP will give into the extortion demand, numerous users in our DeadBolt support forum topic have reported successfully paying the ransomware to recover their files.
The next day, QNAP began warning customers to secure their Internet-exposed NAS devices against DeadBolt by updating to the latest QTS software version, disabling UPnP, and disabling port forwarding.
Later that night, QNAP took more drastic action and force-updated the firmware for all customers’ NAS devices to version 5.0.0.1891, the latest universal firmware released on December 23rd, 2021.
This update also included numerous security fixes, but almost all of them are related to Samba, which is unlikely associated with this attack.
QNAP owners and IT admins told BleepingComputer that QNAP forced this firmware update on devices even if automatic updates were disabled.
However, this update did not go off without a hitch, as some owners found that their iSCSI connections to the devices no longer worked after the update.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
“Just thought I would give everyone a heads-up. A couple of our QNAPS lost ISCSI connection last night. After a day of tinkering and pulling our hair out we finally found it was because of the update. It has not done it for all of the QNAPs we manage but we finally found the resolution,” a QNAP owner said on Reddit.
“In “Storage & Snapshots > ISCSI & Fiber Channel” right-click on your Alias (IQN) select “Modify > Network Portal” and select the adapter you utilize for ISCSI.”
Other users who had purchased the decryption key, and were in the process of decrypting, found that the firmware update also removed the ransomware executable and ransom screen used to initiate decryption. This prevented them from continuing the decryption process once the device finished updating.
“It usually asks me if I want to update, but now it didn’t ask me. I was just standing idle while the decryption was in progress and then I heard a beep from the NAS, and when I looked in the menu, it was asking me if I want to restart now for the update to finalize,” an upset owner posted in BleepingComputer’s DeadBolt support topic.
“I pressed NO but it ignored me and started to close down all the apps in order to restart.”
In response to numerous complaints about QNAP forcing a firmware update, a QNAP support representative replied, stating it was to protect users from the ongoing DeadBolt ransomware attacks.
“We are trying to increase protection against deadbolt. If recommended update is enabled under auto-update, then as soon as we have a security patch, it can be applied right away.
Back in the time of Qlocker, many people got infected after we had patched the vulnerability. In fact, that whole outbreak was after the patch was released. But many people don’t apply a security patch on the same day or even the same week it is released. And that makes it much harder to stop a ransomware campaign. We will work on patches/security enhancements against deadbolt and we hope they get applied right away.
I know there are arguments both ways as to whether or not we should do this. It is a hard decision to make. But it is because of deadbolt and our desire to stop this attack as soon as possible that we did this.” – QNAP support rep.
What is unclear is why a forced update to the latest firmware would protect a device from the DeadBolt ransomware when QNAP initially said that reducing devices’ exposure on the Internet would mitigate the attacks.
One possibility is that an older vulnerability in QTS is being abused to breach QNAP devices and install DeadBolt and that upgrading to this firmware patches the vulnerabilities.
Unfortunately, QNAP’s move may have come too late as CronUP security researcher and Curated Intel member Germán Fernández discovered that DeadBolt had already encrypted thousands of QNAP devices.
Internet device search engine Shodan reports that 1,160 QNAP NAS devices are encrypted by DeadBolt. Censys, though, paints a far grimmer picture, finding 3,687 devices already encrypted at the time of this writing.
Both Shodan and Censys show that the top countries affected by this attack are the United States, France, Taiwan, the United Kingdom, and Italy.
To make matters worse, QNAP NAS owners are already targeted by other ransomware operations named Qlocker and eCh0raix, who constantly scan for new devices to encrypt.
BleepingComputer has asked QNAP further questions about the forced update and DeadBolt attacks.