KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The PYSA ransomware gang has been using a remote access Trojan (RAT) dubbed ChaChi to backdoor the systems of healthcare and education organizations and steal data that later gets leveraged in double extortion ransom schemes.
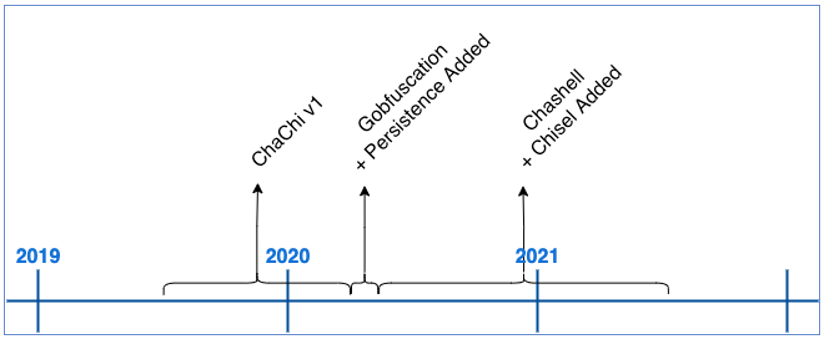
ChaChi is a custom Golang-based RAT malware developed in early 2020 deployed by PYSA operators to access and control infected systems.
The RAT was first observed in the wild as a tool lacking obfuscation, port-forwarding, and DNS tunneling capabilities. However, its creators upgraded it to include all these features as observed when analyzing samples detected in subsequent attacks.
“After initial sightings in attacks during the first quarter of 2020, ChaChi’s code was altered to include obfuscation and persistence in late March or early April,” the BlackBerry Threat Research and Intelligence Team says in a report shared in advance with BleepingComputer.
“Very soon after that, we started seeing ChaChi variants with the added DNS tunnelling and Port-Forwarding/Proxy functionality.”
One of the earliest ChaChi samples was deployed on the networks of French local government authorities in March 2020. The ransomware gang later used an upgraded version to target various industry verticals from healthcare to private companies.
Also Read: The 5 Phases of Penetration Testing You Should Know
These attacks culminated with an escalation of PYSA ransomware activity targeting educational institutions from the UK and 12 US states, according to an FBI flash alert issued in March 2021.
“Since March 2020, the FBI has become aware of PYSA ransomware attacks against US and foreign government entities, educational institutions, private companies, and the healthcare sector by unidentified cyber actors,” the FBI said.
“FBI reporting has indicated a recent increase in PYSA ransomware targeting education institutions in 12 US states and the United Kingdom. The unidentified cyber actors have specifically targeted higher education, K-12 schools, and seminaries.”
The fact that healthcare and education orgs are regularly working with vast amounts of sensitive personal and health information makes them the perfect victims for ransomware gangs like PYSA, who also steal data before encrypting victims’ networks.
Hospitals and schools with no data backups that also use legacy and seldomly patched systems are an even easier target for ransomware attackers as they can be more easily persuaded to pay ransoms to restore systems and get their stolen data back.
PYSA ransomware was first spotted in October 2019 when reports of companies hit by new ransomware started surfacing.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
This ransomware gang is known for exfiltrating a wide range of sensitive data from their victims’ servers, including personally identifiable information (PII), payroll tax information, and other data types.
Technical information on the ChaChi RAT, as well as indicators of compromise and YARA rules, can be found in BlackBerry threat researchers’ report.