





Users worldwide cannot connect to Pulse Secure VPN devices after a code signing certificate used to digitally sign and verify software components has expired.
As employees return from the weekend, network admins have been reporting [1, 2, 3, 4] that users cannot connect to Pulse Secure VPN devices and access internal company resources.
“As of today, staff are no longer accessing our system from home. Normally, they log on to Pulse Secure via the web interface and then select their PC, which is then forwarded via the terminal server service,” a customer reported on the Pulse Secure forums.
This issue affects users who attempt to connect to company resources through their browser, where they are greeted with an error stating, “An unexpected error has occurred,” followed by another error saying, “Detected an internal error. Please retry. If the issue persists, contact your administrator.”
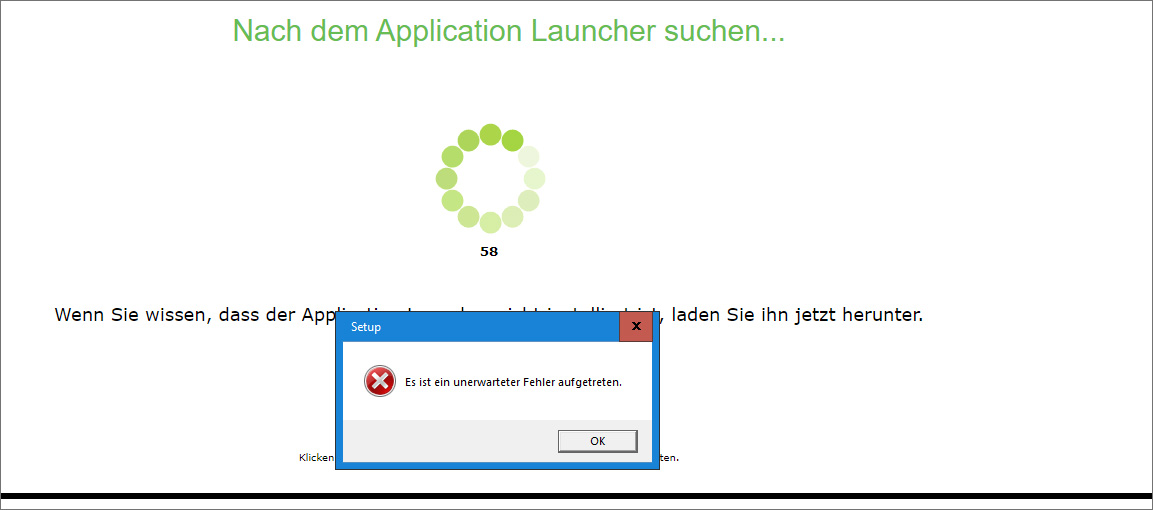
This issue affects users globally and is caused by an expired code-signing certificate and a bug in the Pulse Secure software that is not properly verifying that executables are signed.
Also Read: Compliance Course Singapore: Spotlight On The 3 Offerings
A code-signing certificate allows developers to digitally sign program’s executables so that Windows and end-users can verify that they have not been tampered with by a third party. If a signed executable or DLL is modified somehow, the operating system will no longer consider the program signed and result in warnings or other errors.
When signing an executable, developers can use an optional time-stamping server that adds an authoritative timestamp to a signature, proving when a file was signed by the certificate.
The benefit to timestamps is that it proves that an executable was signed before a certificate expired or revoked. Thus, it allows Windows to consider a file signed even after a certificate becomes invalid.
In a new support bulletin released today, Pulse Secure explains that “multiple functionalities/features fail for End-Users with a Certificate error.”
Pulse Secure says that the issue is caused by a bug not correctly verifying that Pule Secure components are signed as it is checking the certificate’s expiration date rather than the timestamp on a digitally signed file.
As the code-signing certificate used to sign the file has expired today, the bug prevents the software from operating correctly, and users are unable to login to VPN devices.
“The Code sign verification on the Client-Side components fails because the Certificate expiry time is checked as opposed to the timestamp of the Code signing,” a new Pulse Secure bulletin explains.
This bug is affecting users of Pulse Connect Secure (PCC) and Pulse Policy Secure (PPS) products listed below:
3. This impacts only Windows End-Points.
4. The following features are impacted:
The bug is not affecting users utilizing the Pulse Desktop Client directly, macOS or Linux users, and versions before 9.1R8.x.
Pule Secure says they are working on a fix based on version 9.1R11.x of the client software and hope to have it released by the end of the day. For now, it is recommended that users utilize the Pulse Desktop Client instead of connecting via the browser.
Also Read: Considering Enterprise Risk Management Certification Singapore? Here Are 7 Best Outcomes
Pulse Secure admins have also discovered that they can resolve the issue by switching to HTML5 Access profiles for their end-users. Users are also able to connect to RDP via the Pulse Secure VPN Tunneling feature.
BleepingComputer has reached out to Pule Secure with additional questions but has not heard back at this time.