KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







This week a report has revealed details on two Android spyware strains leveraged by state-sponsored threat actors during the India-Pakistan conflict.
The malware strains named Hornbill and SunBird have been delivered as fake Android apps (APKs) by the Confucius advanced persistent threat group (APT), a pro-India state-sponsored operation known to spy on Pakistani and South Asian targets, since at least 2013.
Although Confucius has created Windows malware in the past, the group has extended its capabilities to mobile malware since 2017 when the spying app ChatSpy came into existence.
The apps used by the group contain advanced capabilities including taking photos from the camera, requesting elevated privileges, scraping WhatsApp messages, and uploading all this information to the servers of the APT group.
A report from California-based cybersecurity firm Lookout has revealed counterfeit Android apps laden with malware that was used by pro-India actors to spy on Pakistan’s military and nuclear authorities, in addition to Kashmir’s election officials.
Counterfeit Android apps published by the group include “Google Security Framework,” and apps with a regional significance such as, “Kashmir News”, “Falconry Connect”, “Mania Soccer” and “Quran Majeed” as a part of this espionage operation.
According to Lookout researchers Apurva Kumar and Kristin Del Rosso, the apps associated with SunBird have a more extensive set of capabilities than Hornbill and keep running their data exfiltration sequence at regular intervals.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
“Locally on the infected device, the data is collected in SQLite databases which are then compressed into ZIP files as they are uploaded to C2 infrastructure,” state the researchers.
The following kinds of data is gathered by SunBird and sent to the threat actors.
Apps powered by SunBird can also perform the following actions:
The researchers analyzed over 18 GB of exfiltrated data obtained from six or more publicly exposed C2 servers.
This leaked data revealed the nation-state actors’ targets included potential candidates for Pakistan Atomic Energy Commission, individuals with close links to Pakistan Air Force (PAF), and the election officers who oversee the electoral process within the Pulwama district of Kashmir.
BleepingComputer was able to obtain and analyze a copy of one such SunBird Android app called Falconry Connect.
We noticed the malicious class files existed within the APK at a mysterious location (namespace) called com.falconry.sun.SunServices.
The use of “sun” in both namespace and directory names with these code files is misleading: to ward off an analyst who may initially think these folders are associated with Sun Microsystems, creator of the Java programming language.
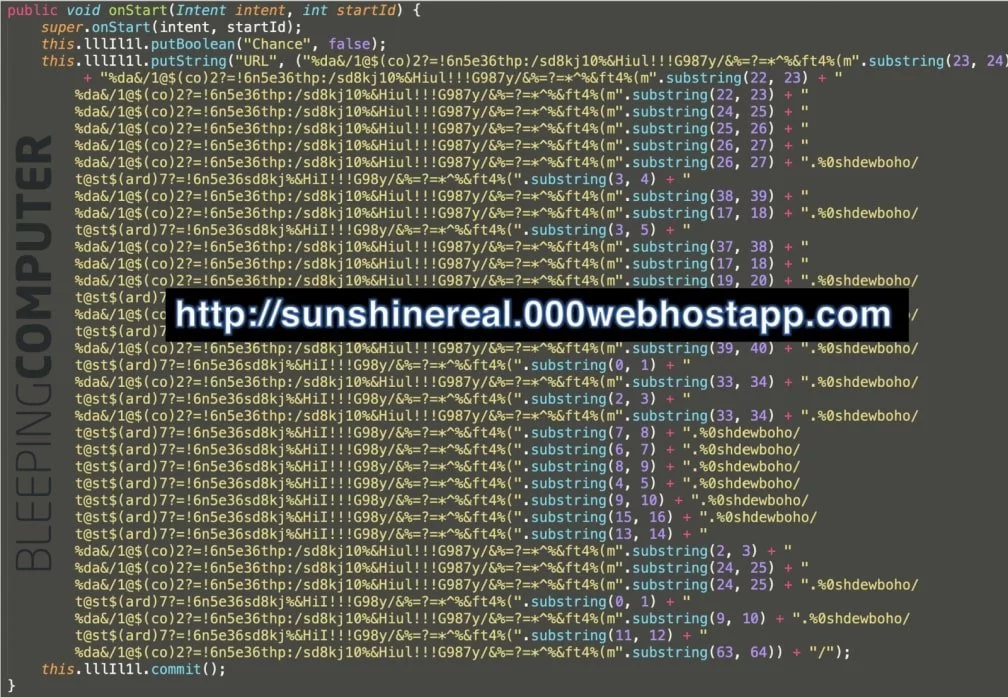
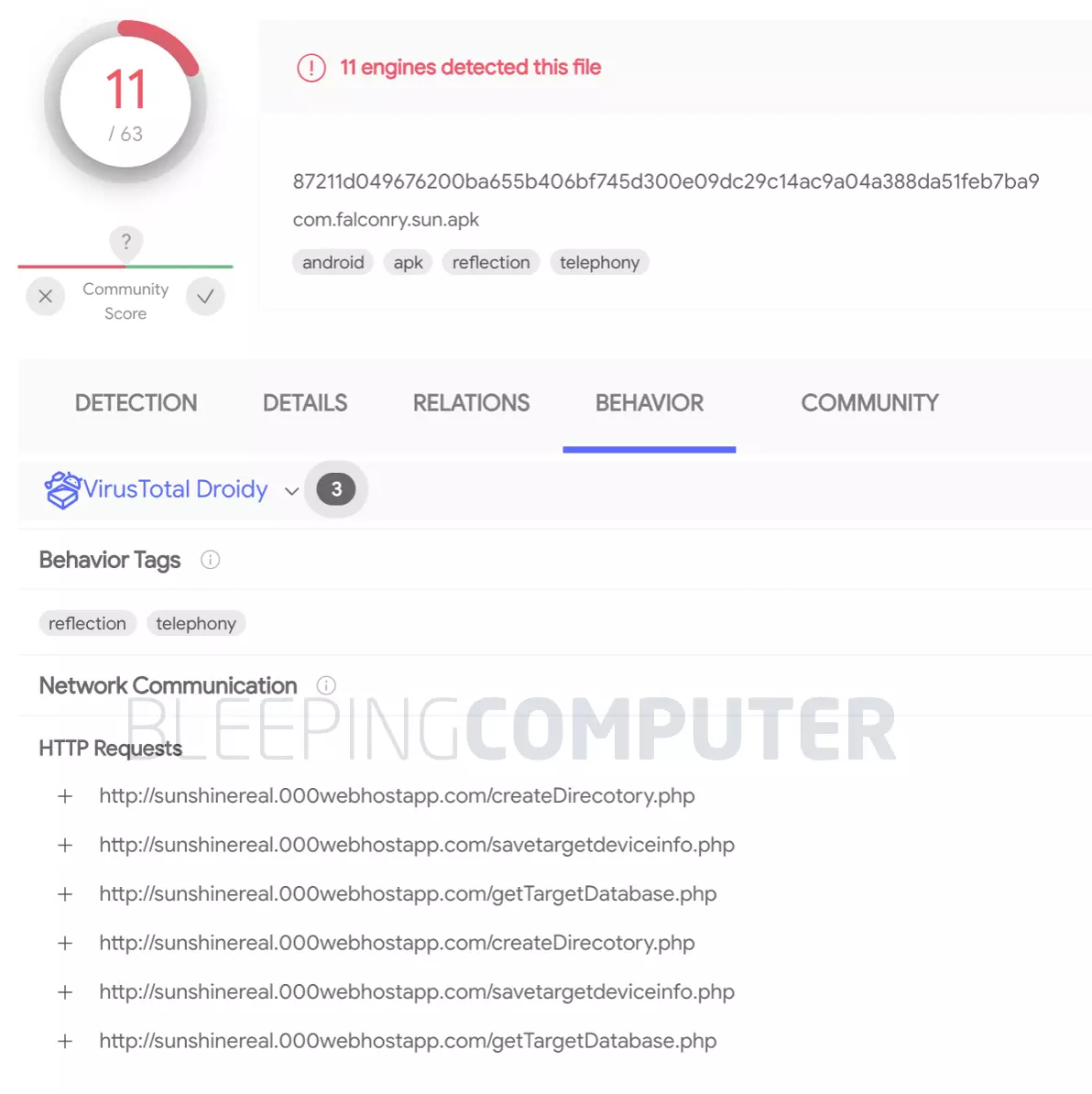
This particular app exfiltrates user data to the command-and-control (C2) server sunshinereal.000webhostapp[.]com domain, and making periodic calls to the PHP pages listed on the sample’s VirusTotal page and shown below.
As seen by BleepingComputer, the C2 domain isn’t spelled out clearly within the code but is rather constructed from multiple gibberish strings by taking small chunks (substrings) from them over and over and concatenating them.
Even today, VirusTotal detection rate for the Falconry Connect app is low, meaning over 80% of antivirus software couldn’t detect it.
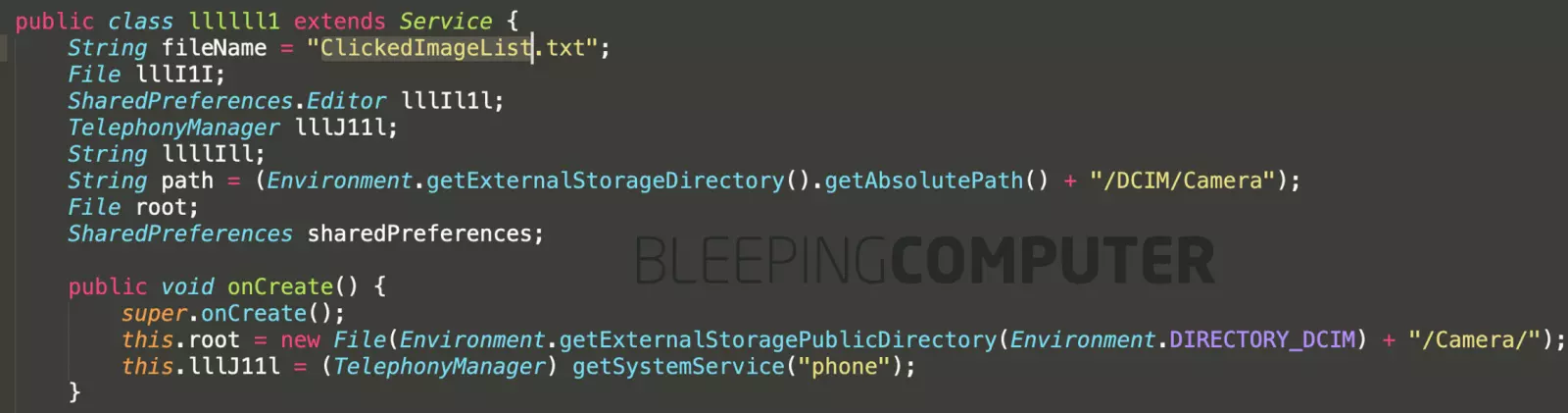
As shown in the screenshot below, BleepingComputer further noticed the source code had references to accessing the “/DCIM/Camera” folder containing the camera photos taken by the user, among other sensitive locations.
Also Read: The 3 Main Benefits Of PDPA For Your Business
The report by Lookout states, apps containing the Hornbill strain are more passive in nature and used as recon tools, consuming minimal resources and battery power.
However, the researchers explain that Hornbill actors are more interested in monitoring the user’s WhatsApp activity.
“In addition to exfiltrating message content and sender information of messages, Hornbill records WhatsApp calls by detecting an active call by abusing Android’s accessibility services.”
“The exploitation of Android’s accessibility services in this manner is a trend we are observing frequently in Android surveillanceware. This enables the threat actor to avoid the need for privilege escalation on a device,” states the report released by Lookout.
Lookout Threat Intelligence team is confident that the same actor is behind both SunBird and Hornbill using it for different surveillance purposes.
The researchers stress that none of these apps were distributed via Google Play or any authorized app store.
Mobile users are advised to download apps only from the official app stores and avoid risky websites providing bootleg Android APKs and iOS APPs.