KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The previously shutdown Phorpiex botnet has re-emerged with new peer-to-peer command and control infrastructure, making the malware more difficult to disrupt.
The botnet first launched in 2016 and quickly accumulated a massive army of over 1 million devices over the years.
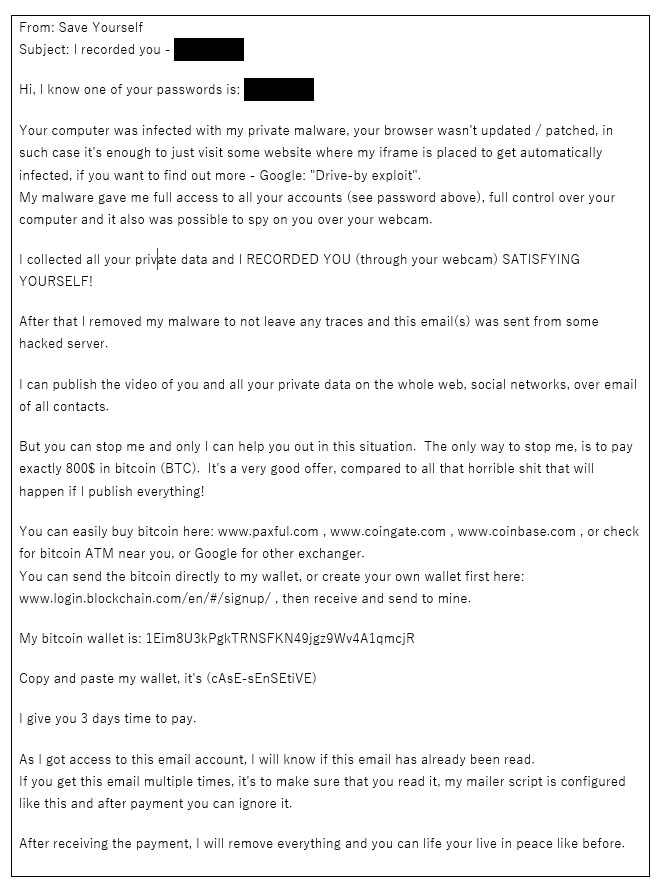
The malware generates revenue for its developers by swapping cryptocurrency addresses copied to the Windows clipboard with addresses under their control or by spamming sextortion emails to scare people into paying an extortion demand.
However, after over five years of development, the Phorpiex operators shut down their infrastructure and tried to sell the botnet’s source code on a hacking forum.
Also Read: How to Register Data Protection Officer (DPO) in ACRA Bizfile+
While it is unknown if the threat actors could sell their malware, researchers from Check Point saw that the infrastructure had turned back on in September, less than two weeks after their “for sale” post.
This time, though, the command and control servers distributed a new botnet variant that included some new tricks to make it harder to find the operators or take down infrastructure.
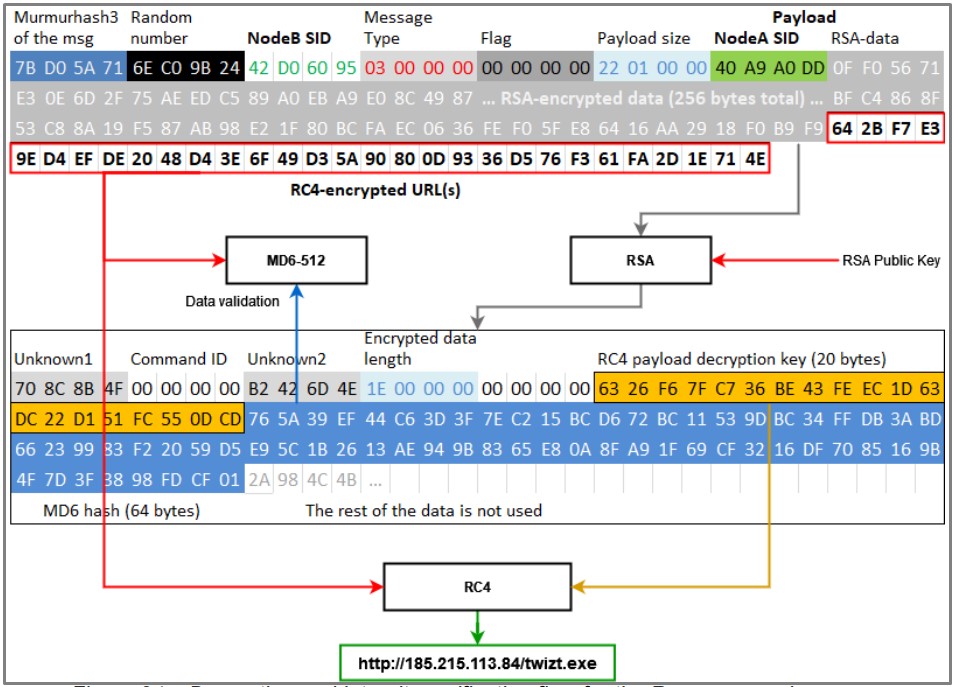
When Phorpiex relaunched in September, Check Point saw it distributing a new malware variant called “Twizt” that allows the botnet to operate without centralized command and control servers.
Instead, the new Twizt Phorpiex variant added a peer-to-peer command and control system that allows the various infected devices to relay commands to each other if the static command and control servers were offline.
“Simultaneously, the C&C servers started distributing a bot that had never seen before. It was called “Twizt” and enables the botnet to operate successfully without active C&C servers, since it can operate in peer-to-peer mode.,” explained the new report by Check Point.
Also Read: Cost of GDPR Compliance for Singapore Companies
“This means that each of the infected computers can act as a server and send commands to other bots in a chain.”
This new P2P infrastructure also allows the operators to change the IP address of the main C2 servers as necessary while remaining hidden within a swarm of infected Windows machines.
The new features included in the Twizt variant include:
Twizt can also download additional payloads through a list of hard-coded base URLs and paths or after receiving the corresponding command from the C2 server.
Phorpiex was previously known for delivering large-scale sextortion spam campaigns, allowing the threat actors to spam over 30,000 sextortion emails per hour.
The operators made roughly $100k per month by tricking people into sending them crypto and did so relatively effortlessly.
The botnet also uses crypto-clipping, or a clipboard hijacker, that replaces cryptocurrency wallet addresses copied to the Windows clipboard with those controlled by the threat actors. So now when a person attempts to send cryptocurrency to another address, it is sent to the ones under the threat actor’s control instead.
As cryptocurrency addresses are hard to remember, people will likely not realize that their cryptocurrency was stolen until they notice it went to the wrong address.
Due to the botnet’s capability to run without a C2 or any central management, even if its operators are arrested, and the infrastructure is taken down, infected machines will still direct transactions to the wrong wallets.
CheckPoint has identified 60 unique Bitcoin and 37 unique Ethereum wallets used for this purpose and said that Dogecoin, Dash, Monero, and Zilliqa are also targeted.
As for the wallets supported by the clipper of the latest Phorpiex version, these are:
LISK, POLKADOT, BITCOIN, WAVES, DASH, DOGECOIN, ETHEREUM, LITECOIN, RIPPLE, BITTORRENT, ZCASH, TEZOS, ICON, QTUM, RAVENCOIN, NEM, NEO, SMARTCASH, ZILLIQA, ZCASH PRIVATE, YCASH, BITCOIN CASH, COSMOS, MONERO, CARDANO, GROESTLCOIN, STELLAR, BITCOIN GOLD, BAND PROTOCOL, PERFECT MONEY USD, PERFECT MONEY EURO, PERFECT MONEY BTC.
In the past twelve months, Phorpiex has hijacked 969 transactions using its crypto-clipping component, stealing 3.64 Bitcoin ($172,300), 55.87 Ether ($216,000), and $55,000 worth of ERC20 tokens.
With the Phorpiex botnet evolving its code to use new peer-to-peer command and control features, it shows that the malware is still under active development.
“The emergence of such features suggests that the botnet may become even more stable and therefore, more dangerous,” warns Check Point.
To protect yourself against threats like Phorpiex, Check Point offers the following tips:
Finally, cryptocurrency transactions cannot be reversed, and retrieving lost amounts can only happen if law enforcement gains access to a threat actor’s wallet.
While law enforcement operations have been able to recover ransom payments in the past, it is seldom the case, so don’t count on it.