KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A large-scale malware campaign on Huawei’s AppGallery has led to approximately 9,300,000 installs of Android trojans masquerading as over 190 different apps.
The trojan is detected by Dr.Web as ‘Android.Cynos.7.origin’ and is a modified version of the Cynos malware designed to collect sensitive user data.
The discovery and report come from researchers at Dr. Web AV, who notified Huawei and helped them remove the identified apps from their store.
However, those who installed the apps on their devices will still have to remove them from their Android devices manually.
Also Read: What Is Data Sovereignty and How Does It Apply To Your Business?
The threat actors hid their malware in Android apps pretending to be simulators, platformers, arcades, RTS strategy, and shooting games for Russian-speaking, Chinese, or international (English) users.
As they all offered the advertised functionality, users were unlikely to remove them if they enjoyed the game.
The list of the Cynos malware apps is too extensive to share here, but some notable examples that stand out due to having a large number of installations are listed below:
Since it’s impractical to compare your list of installed apps to the full list of 190 malicious apps, the more straightforward solution would be to run an AV tool that can detect Cynos trojans and their variants.
The functionality of this Cynos trojan variant can perform various malicious activities, including spying on SMS texts and downloading and installing other payloads.
“The Android.Cynos.7.origin is one of the modifications of the Cynos program module. This module can be integrated into Android apps to monetize them. This platform has been known since at least 2014,” explained Doctor Web malware analysts in their report.
“Some of its versions have quite aggressive functionality: they send premium SMS, intercept incoming SMS, download and launch extra modules, and download and install other apps.”
“The main functionality of the version discovered by our malware analysts is collecting the information about users and their devices and displaying ads.”
The aggressive nature of the trojan becomes apparent right from the installation phase when it asks for permission to perform activities that are not generally associated with a game, such as making phone calls or detecting users’ locations.
Also Read: What a Vulnerability Assessment Shows and How It Can Save You Money
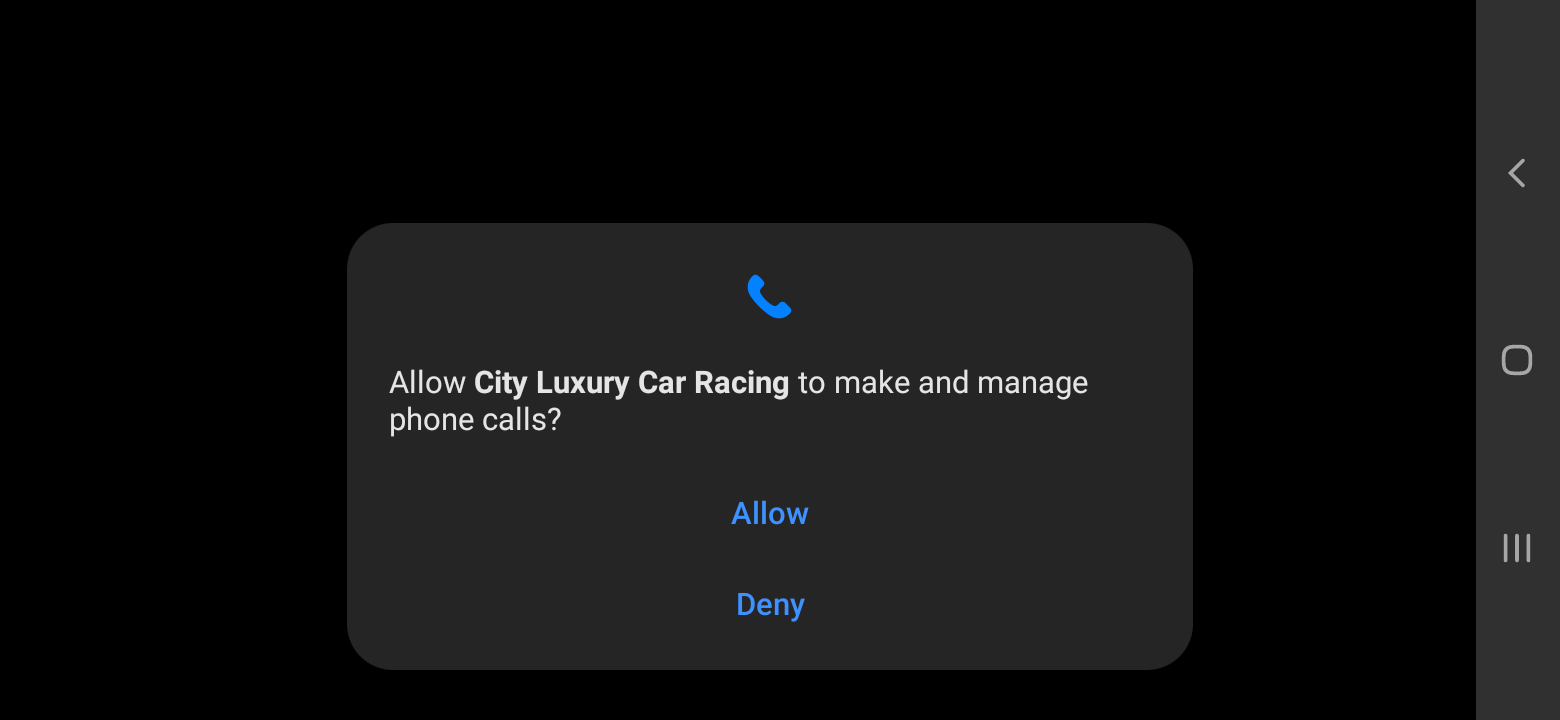
If the user grants the permission requests, the malware can exfiltrate the following data to a remote server:
In addition to the above, Cynos trojans can potentially download and install extra modules or apps, send premium service SMS, and intercept incoming SMS.
As such, these apps can lead to unexpected charges from subscribing to premium services, and they can also drop even stealthier spyware payloads.