KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







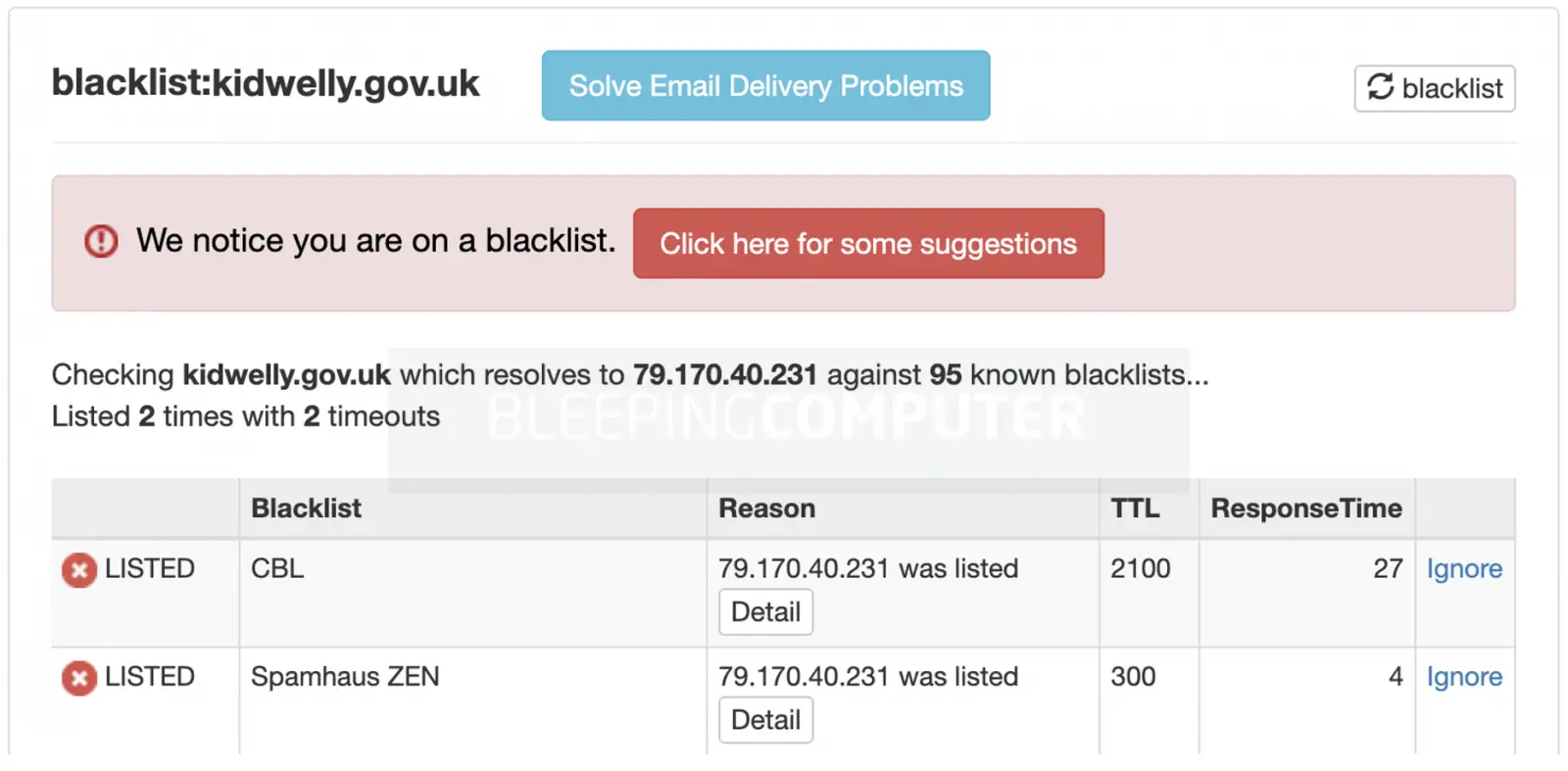
Hundreds of domains managed by the U.K. government are on DNS-based blacklists creating email communication problems.
Multiple government agencies, councils, and public welfare agencies rely on GOV.UK domain infrastructure to provide online services to Britain’s residents.
Being on an automated IP blacklist usually signifies a problem with your mail infrastructure: most likely either your server has been sending spam, or was compromised at some point.
The Domain Name System-based Blackhole List (DNSBL) is a decentralized system with different servers around the world keeping tabs on IPs spamming email users.
These lists can then be surveyed via simple DNS lookup queries by mail servers to determine the probability of an incoming email message being spam.
This week, GitHub user tg12 compiled a list of 8,481 GOV.UK domains and found that 450 of them were on one or more DNSBLs. BleepingComputer verified the IP addresses for a large number of the listed domains and their email server and found them present on a spam list.
However, the list provided by tg12 might need a review.
While most of the 450 domains listed are on one or more spam lists, some are false positives.
Reddit user wobblecapsule implied this, referring to the bristol-city.gov.uk domain, and BleepingComputer can confirm it was not present on a DNSBL at the time of testing.
Another user KernelDecker said in the same thread, “To be fair, Microsoft can’t keep its office 365 and Hotmail IPs off some blacklists either,” which goes to the fact how difficult it can be keeping IPs off of DNSBLs.
Also read: 7 Simple Tips On How To Create A Good Business Card Data
Having a domain on a DNSBL is problematic for an organization, all the more for government agencies, as this may prevent legitimate emails from being delivered correctly.
For example, the recipient’s mail provider may lookup a DNSBL and move your sent mail to the recipient’s spam folder.
If your organization uses shared hosting providers, this would very likely mean multiple clients are sharing the same IP address for their email and hosting needs.
Problems arise when even one offending user abuses the shared services for spamming users. Being on the same server, this would impact all other clients sharing that IP, should the IP now be added to a blacklist.
Ultimately, this can impact an organization’s reputation in addition to causing problems with email delivery.
As an organization, while telling your users to “also check the junk folder for emails,” is sound advice, it is prudent to regularly audit the DNSBLs for your mail server IPs, and preferably use a dedicated hosting to minimize the chances of being added to a spam list.
Also read: EU GDPR Articles: Key For Business Security And Success