



Today, the OpenSSL project has issued an advisory for two high-severity vulnerabilities CVE-2021-3449 and CVE-2021-3450 lurking in OpenSSL products.
OpenSSL is a commonly used software library for building networking applications and servers that need to establish secure communications.
These flaws include:
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
The DoS vulnerability (CVE-2021-3449) in OpenSSL TLS server can cause the server to crash if during the course of renegotiation the client sends a malicious ClientHello message.
“If a TLSv1.2 renegotiation ClientHello omits the signature_algorithms extension (where it was present in the initial ClientHello), but includes a signature_algorithms_cert extension then a NULL pointer dereference will result, leading to a crash and a denial of service attack,” states the advisory.
The vulnerability only impacts OpenSSL servers running versions between 1.1.1 and 1.1.1j (both inclusive)that have both TLSv1.2 and renegotiation enabled.
However, because this is the default configuration on these OpenSSL server versions, many of the active servers could be potentially vulnerable. OpenSSL clients are not impacted.
Fortunately, all it took to fix this DoS bug was a one-liner fix, which comprised setting the peer_sigalgslen to zero.
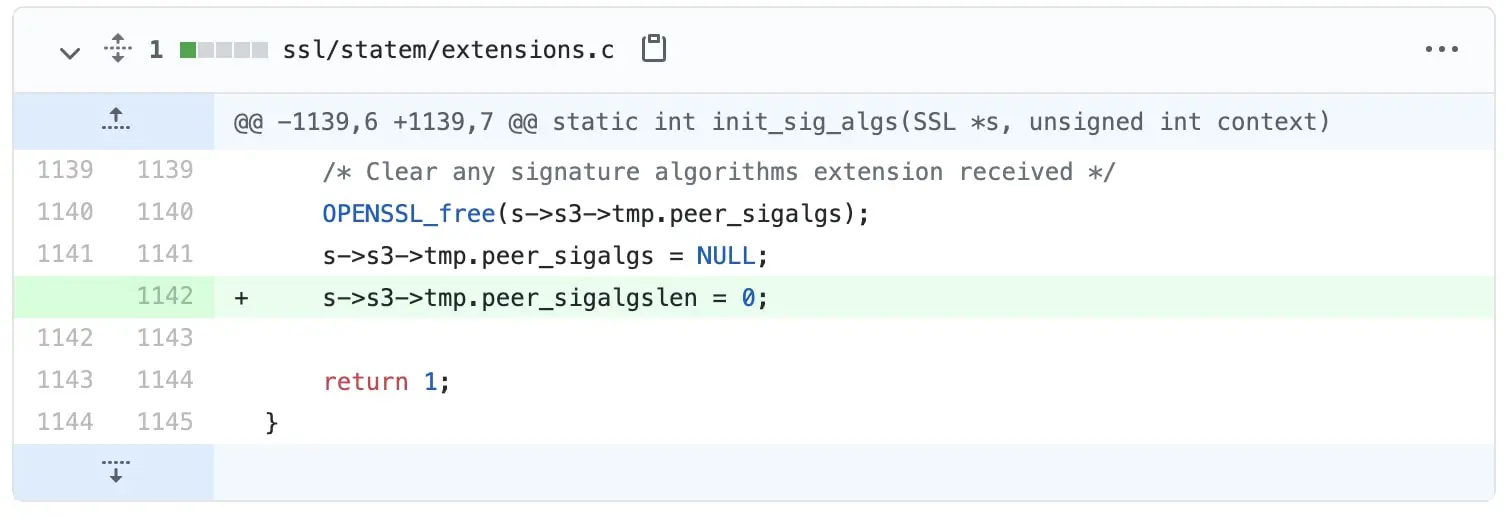
The vulnerability was discovered by engineers Peter Kästle and Samuel Sapalski of Nokia, who also offered the fix shown above.
The Certificate Authority (CA) certificate validation bypass vulnerability, CVE-2021-3450, has to do with the X509_V_FLAG_X509_STRICT flag.
This flag is used by OpenSSL to disallow use of workarounds for broken certificates and strictly requires that certificates be verified against X509 rules.
However, due to a regression bug, OpenSSL versions 1.1.1h and above (but excluding the fixed release 1.1.1k) are impacted by this vulnerability, as this flag is not set by default in these versions.
“Starting from OpenSSL version 1.1.1h a check to disallow certificates in the chain that have explicitly encoded elliptic curve parameters was added as an additional strict check.”
“An error in the implementation of this check meant that the result of a previous check to confirm that certificates in the chain are valid CA certificates was overwritten,” states the advisory.
In effect, this means OpenSSL instances fail to check that non-CA certificates must not be the issuers of other certificates, therefore opening up the possibilities for attackers to exploit this miss.
On March 18th, 2021, Benjamin Kaduk from Akamai reported this flaw to the OpenSSL project.
The vulnerability was discovered by Xiang Ding and others at Akamai, with a fix having been developed by Tomáš Mráz.
Neither vulnerabilities impact OpenSSL 1.0.2.
Both vulnerabilites are fixed in OpenSSL 1.1.1k and users are advised to upgrade to this version to protect their instances.
Also Read: The DNC Singapore: Looking At 2 Sides Better
As reported by BleepingComputer, DHS-CISA had urged system administrators in December 2020 to patch another OpenSSL DoS vulnerability.
Users should therefore protect themselves from security flaws like these by applying timely updates.