KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A user enumeration technique discovered by security researcher Carlo Di Dato demonstrates how Gravatar can be abused for mass data collection of its profiles by web crawlers and bots.
Gravatar is an online avatar service that lets users set and use a profile picture (avatar) across multiple websites that support Gravatar.
The most recognizable use cases of Gravatar are perhaps WordPress websites integrated with the service and GitHub.
While data provided by Gravatar users on their profiles is already public, the easy user enumeration aspect of the service with virtually no rate limiting raises concerns with regards to the mass collection of user data.
In our demonstration of this bug, we will use the profile “beau” that is mentioned in Gravatar’s docs. This profile belongs to Beau Lebens, Head of Product Engineering for WooCommerce at Automattic.
According to Gravatar’s official documentation, the URL structure of a Gravatar profile consists of either a username or an MD5 hash of the email address associated with that profile.
This means a profile with a username “beau” can be accessed at https://en.gravatar.com/beau or by navigating to https://www.gravatar.com/205e460b479e2e5b48aec07710c08d50 which will ultimately redirect a visitor to the user’s public Gravatar page.
This is no problem: in either of these cases, Beau’s Gravatar username or MD5 parameters could not be easily predicted by a visitor and had to be known beforehand.
However, an additional method of accessing user data not disclosed in the docs includes simply using a numeric ID associated with each profile to fetch data.
Italian security researcher Carlo Di Dato on discovering this possibility reached out to BleepingComputer this week after failing to get concrete action from Gravatar.
As can be observed in Beau’s example profile above, clicking on the “JSON” link on the page, leads to http://en.gravatar.com/beau.json returning JSON representation of profile data.
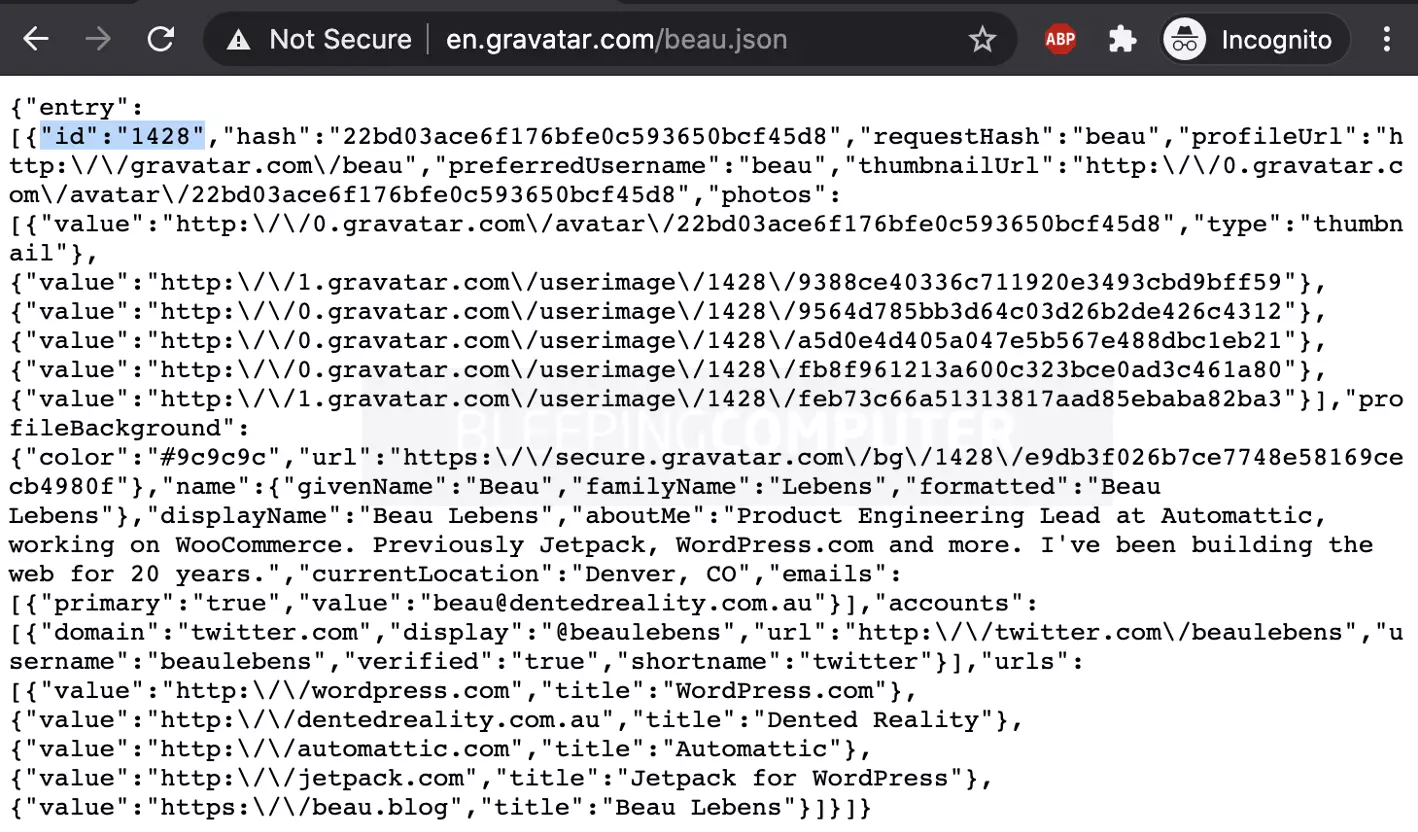
The field “id” in the JSON blob immediately caught Di Dato’s attention.
A hidden API route in the service enables anyone to obtain the user’s JSON data by simply using the profile “id” field.
“I spotted an interesting field named ‘id’ (it’s an integer value). The next step was to test if my profile was accessible using the ‘id’,” the researcher told BleepingComputer.
“So I browsed to http://en.gravatar.com/ID.json and it worked. Now that I know I can access [the user’s JSON data] using an integer value, the next logical step was to check if I can perform a user enumeration,” he continued.
By writing a simple test script that sequentially visits profile URLs from IDs 1 to 5000 (as shown below), Di Dato was able to collect JSON data of the first 5000 Gravatar users with no issues.
Also Read: 7 Simple Tips On How To Create A Good Business Card Data
“If you take a look at the JSON file, you will find a lot of interesting information. The danger of this kind of issue is that a malicious user could download a huge amount of data and perform any kind of social engineering attack against legit users,” said Di Dato.
In our tests, BleepingComputer could confirm certain user profiles had more public data than the others, for example, BitCoin wallet addresses, phone numbers, location, etc.
The users who create public profiles on Gravatar consent to making this data publicly available, so this is not a data leak or a privacy issue in that regard.
“Of course, Mr. Stephen knows that registering on Gravatar, his data will be publicly accessible. What I’m almost sure he doesn’t know, is that I was able to retrieve this data querying Gravatar in a way which should not be possible,” stated Di Dato.
He continued, “As Gravatar states in its guides, I should have Mr. Stephen’s email address or his Gravatar user name to perform the query. Without this information, it should have been almost impossible for me to get Mr. Stephen’s data, right?”
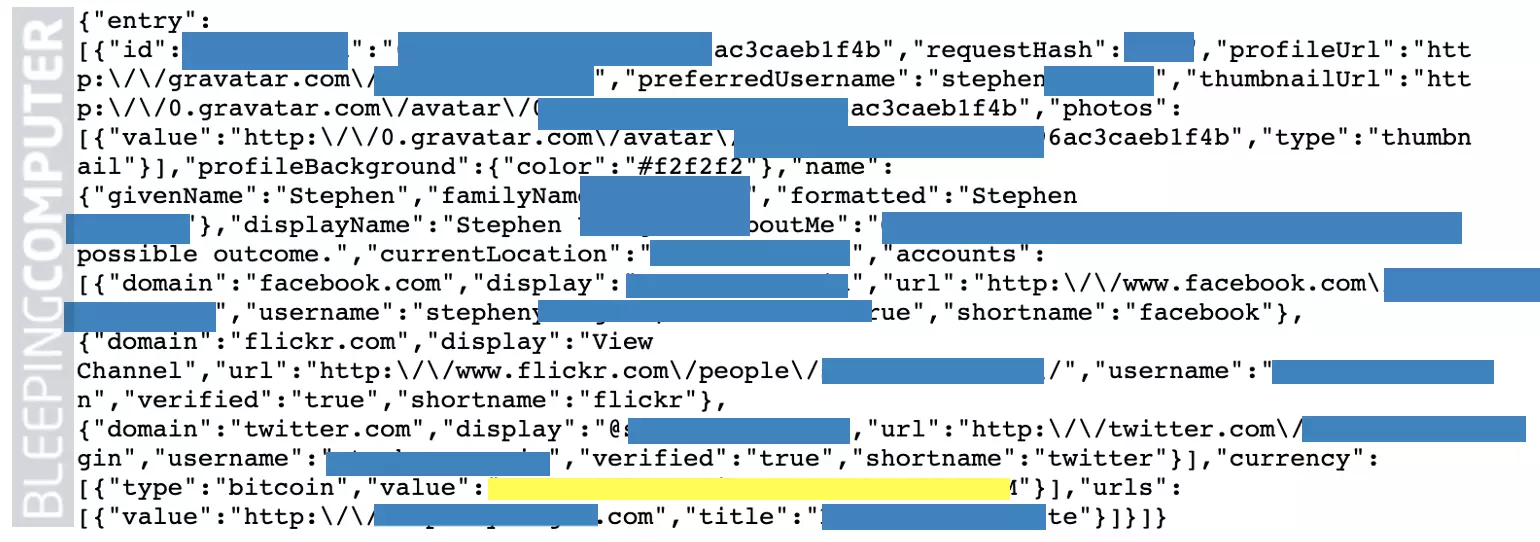
An issue like this becomes problematic because any web crawler or bot can now sequentially query virtually the entire Gravatar database, and harvest public user data very easily thanks to this little known but effective technique.
In the past, criminals have scraped Facebook profile data in bulk using its APIs and sold the dumps on the dark web for profit.
BleepingComputer emailed Gravatar for comment but we have not yet received a response from them.
Also Read: How To Send Mass Email Without Showing Addresses: 2 Great Workarounds