KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An advisory from the U.S. National Security Agency provides Microsoft Azure administrators guidance to detect and protect against threat actors looking to access resources in the cloud by forging authentication information.
The document considers an adversary that already breached the local network and has privileged access to the on-premise authentication mechanisms for the cloud infrastructure.
NSA released the guidance “in response to ongoing cybersecurity events,” referring to SolarWinds supply-chain attack that targeted private and government organizations in at least seven countries by Microsoft’s count.
Among the victims are multiple departments of the U.S. Government, including Treasury, Commerce, Energy, Homeland Security, the National Institutes of Health, and the National Nuclear Security Administration (NNSA).
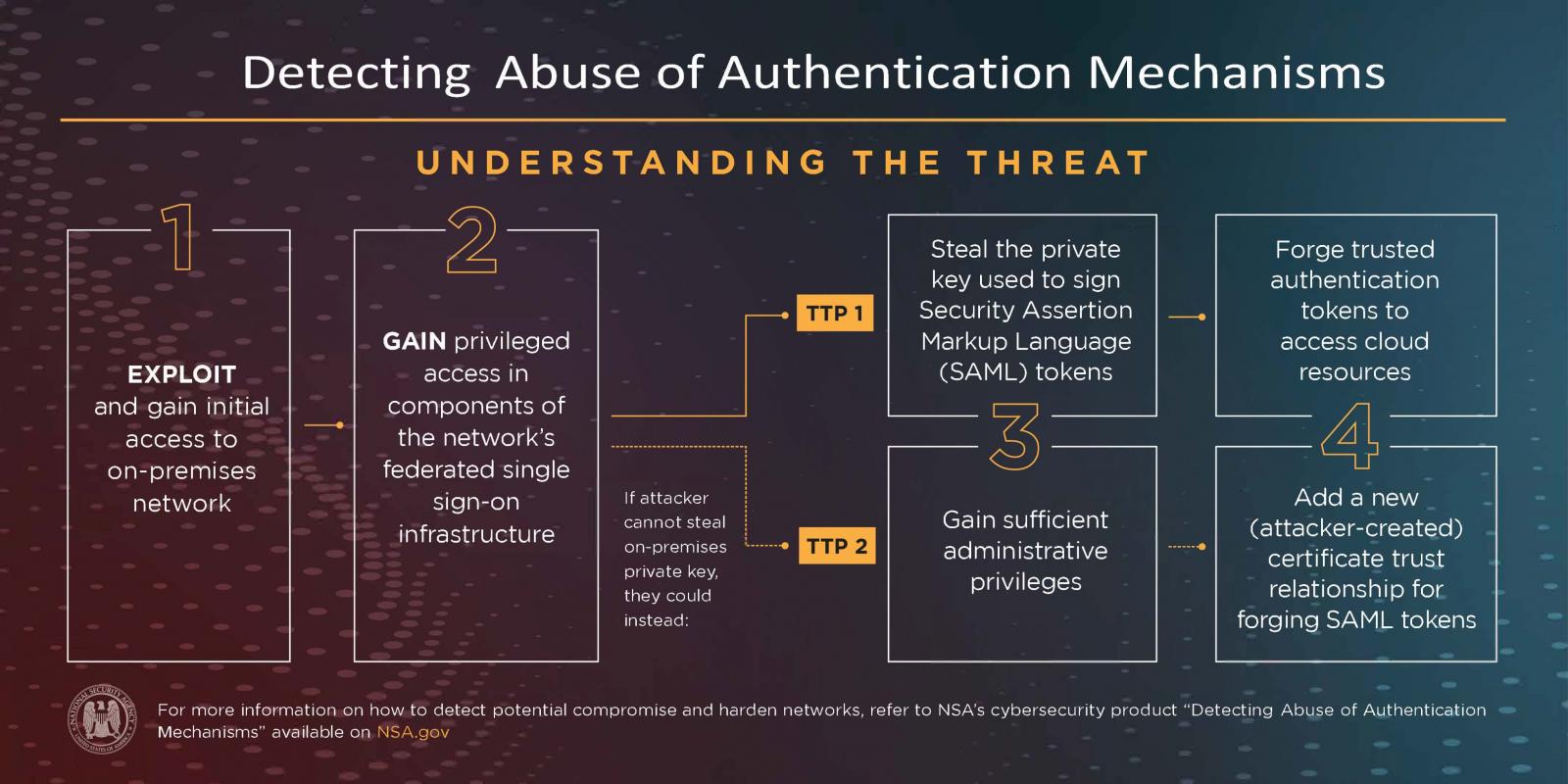
The two tactics, techniques, and procedures (TTPs) discussed in NSA’s advisory have been in use since at least 2017 and refer to forging Security Assertion Markup Language (SAML) tokens for single sign-on (SSO) authentication to other service providers.
“In the first TTP, the actors compromise on-premises components of a federated SSO infrastructure and steal the credential or private key that is used to sign Security Assertion Markup Language (SAML) tokens. Using the private keys, the actors then forge trusted authentication tokens to access cloud resources”
– the U.S. National Security Agency
A variation of the above is when the adversary can’t get an on-premise access key and try to obtain admin privileges on the victim network to add a malicious certificate that enables forging the SAML tokens.
Also Read: Limiting Location Data Exposure: 8 Best Practices
In the second case, the threat actor uses a compromised global administrator account to assign credentials to identities for cloud apps that can be invoked to access other cloud resources.
The agency explains that the actor can then invoke the application’s credentials to access cloud resources, the email service being typically the goal.
These TTPs are not vulnerabilities in the design of federated identity management, the SAML protocol, or identity services available locally or in the cloud.
On-premise components responsible for authentication, assigning privileges, and signing SAML tokens are essential in the security of identity federation in any cloud environment. And compromising any of them can lead to breaking the trust in the authentication tokens.
“It is critical when running products that perform authentication that the server and all the services that depend on it are properly configured for secure operation and integration. Otherwise, SAML tokens could be forged, granting access to numerous resources”
– the U.S. National Security Agency
The agency provides a set of mitigation actions that administrators can use to defend against the above TTPs and to make it more difficult for threat actors to access on-premise identity and federation services.
The measures are aimed at the National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) network administrators and focus on Microsoft Azure federation. But many of them can be adapted to other environments.
Hardening the systems running local identity and federation services and monitoring the use of SSO tokens are the main lines that administrators can follow to protect against and detect a compromise of identity services.

For Microsoft Azure environments, the NSA recommends reviewing the authentication and authorization configuration in Active Directory and setting it up to reject authorization requests using tokens with attributes that are not in tune with the organizational policy.
Removing unnecessary applications with credentials, enforcing multi-factor authentication, and disabling legacy authentication are good defenses for the environment.
Also Read: 10 Practical Benefits of Managed IT Services
Additional measures to secure the private keys should be considered, such as using a FIPS-validate Hardware Security Module (HSM).
Detecting indicators of compromise is a task shared by the cloud service provider and the tenant organization. The former can use their position to look for sophisticated attacks.
Organizations can search local and cloud logs for signs of suspicious tokens. The NSA recommends paying attention to the following:
Examine logs for the suspicious use of service principals: