KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A state-sponsored North Korean threat actor tracked as TA406 was recently observed deploying custom info-stealing malware in espionage campaigns.
The particular actor is attributed as one of several groups known as Kimsuky (aka Thallium). TA406has left traces of low-volume activity since 2018, primarily focusing on espionage, money-grabbing scams, and extortion.
However, in March and June 2021, TA406 launched two distinct malware distribution campaigns that targeted foreign policy experts, journalists, and members of NGOs (non-governmental organizations).
In a new report, researchers at Proofpoint tracked TA406, sampled their tools, and discovered the services they abuse and the phishing lures they employ.
Also Read: How To Check Data Breach And How Can We Prevent It
TA406 is engaging in malware distribution, phishing, intelligence collection, and cryptocurrency theft, resulting in a wide range of criminal activities.
According to Proofpoint’s report, the actors work roughly from 9 a.m. to 5 p.m. (KST), seven days a week, with hacking their full-time occupation.
The targeting scope is quite broad, including North America, Russia, China, South Korea, Japan, Germany, France, the UK, South Africa, India, and more.
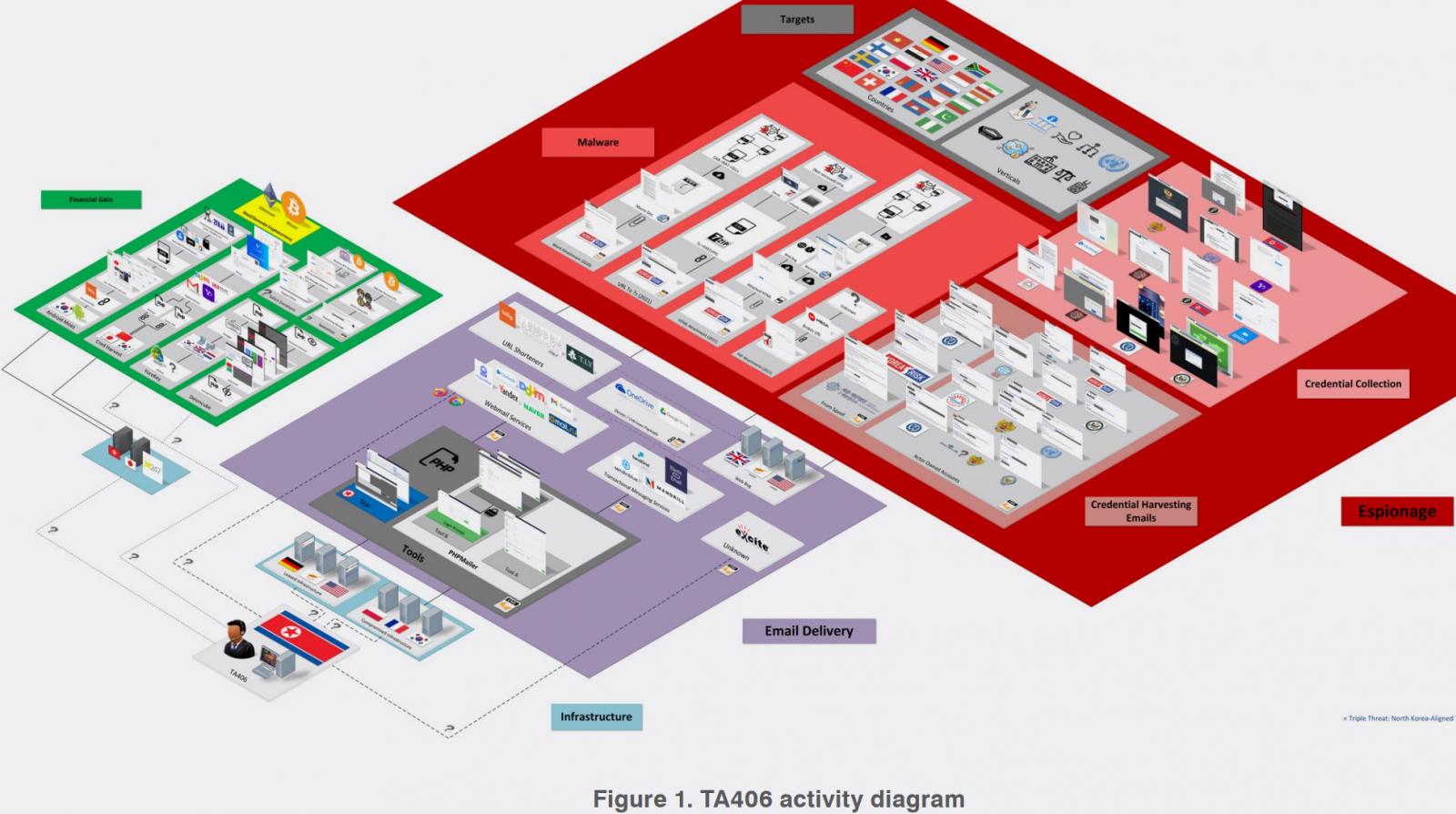
The phishing emails sent by TA406 commonly use lures about nuclear safety, politics, and Korean foreign policy, while targeting high-ranking elected officials.
“The recipients of that campaign included some of the highest ranking elected officials of several different governmental institutions, an employee at a consulting firm, government institutions related to defense, law enforcement, and economy and finance, and generic mailboxes for board and customer relations of a large financial institution,” explains Proofpoint’s report.
The mails are sent from compromised websites, and the sender usually impersonates real people instead of creating fake personas.
Examples include an editor at Global Asia, a professor at Yonsei University, and an adviser to President Moon Jae-in.
Of particular interest, when conducting phishing campaigns to harvest credentials, TA406 does not usually create elaborate landing pages to impersonate a well-known server. Instead, they use basic HTTP authentication, which displays a browser dialog requesting the user’s credentials.
Also Read: Top 8 Main PDPA Obligations To Boost And Secure Your Business
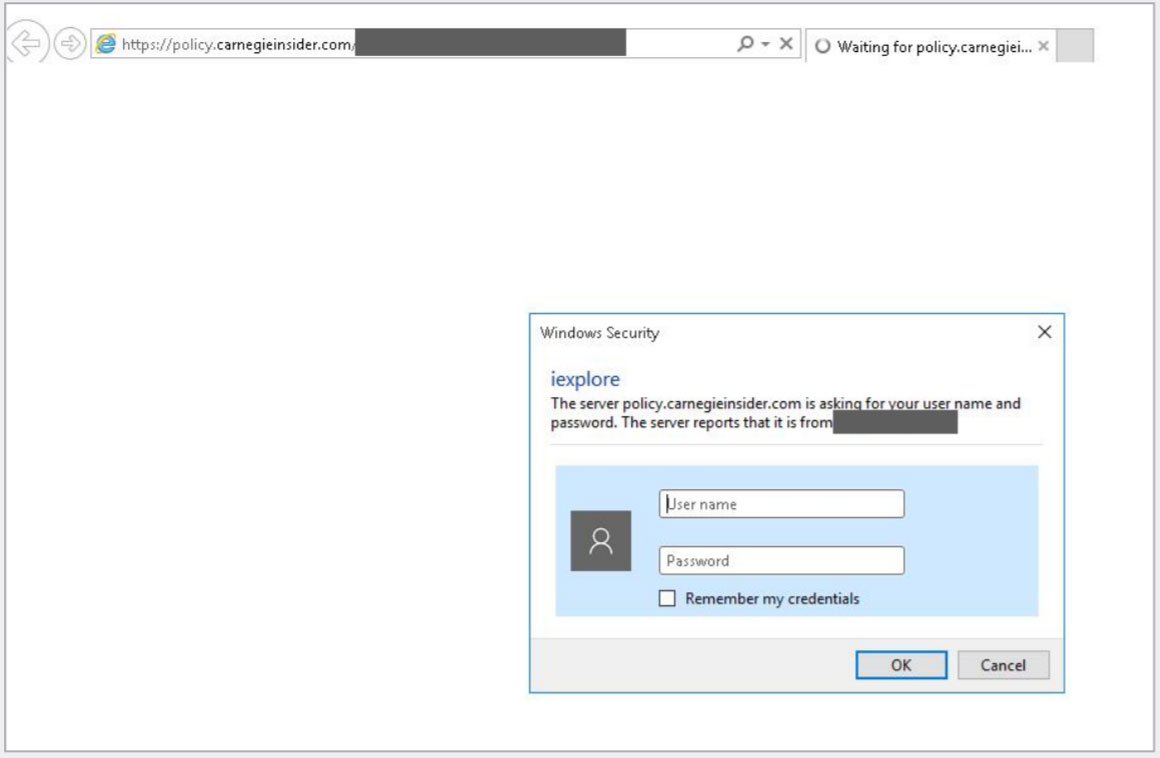
The lures are typically PDF files that require the recipient to log in to the hosting platform using their personal or corporate credentials to view them.
Starting in January 2021, TA406 began dropping malware payloads via phishing emails leading to 7z archives. These archives contained an EXE file with a double extension to appear as an .HTML file.
If opened, the file would create a scheduled task named “Twitter Alarm,” which enables the actors to drop additional payloads every 15 minutes.
Upon execution, the EXE also opens a web browser to a PDF file of a legitimate NK News article hosted on the actor’s infrastructure, attempting to trick the victim into thinking they’re reading a post on a news site.
In June 2021, TA406 began deploying a custom malware named ‘FatBoy,’ which dropped as an HTML attachment on the victim’s disk.
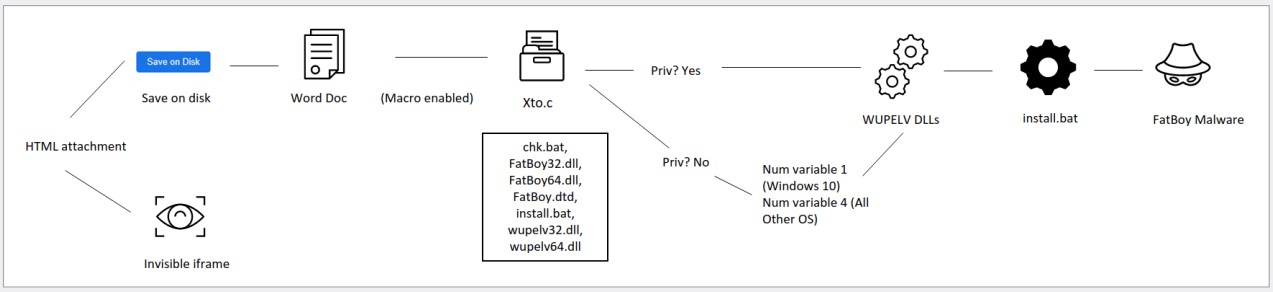
Each of these attachments has a unique hash and features an invisible iframe to communicate with the attackers and tell them which recipient (IP address) opened the file.
FatBoy is a small first-stage malware whose purpose is to download a CAB file from the C2 every 20 minutes.
The CAB file contains a batch script (ball.bat), which executes a VBS script designed to perform reconnaissance and exfiltrate information via HTTP POST requests.
A notable TA406 malware fetched by the downloaded malware is ‘YoreKey,’ a custom Windows keylogger masquerading as MetaTrader 4 Manager, a legitimate electronic trading platform.
YoreKey ensures persistence by creating a registry key and storing its logs in plain text on the infected system.
The keylogger allows the threat actors to steal other login credentials entered by the user as they use their device.
Parallel to the above, TA406 is also engaging in crypto-stealing operations, and according to Proofpoint’s findings, has received at least 3.77 Bitcoin, worth approximately $222,000.
This is done through various methods, including posing as NGOs for donations, offering (probably fake) file decoding/deobfuscation services through a website named ‘Deioncube,’ and sextortion scams.
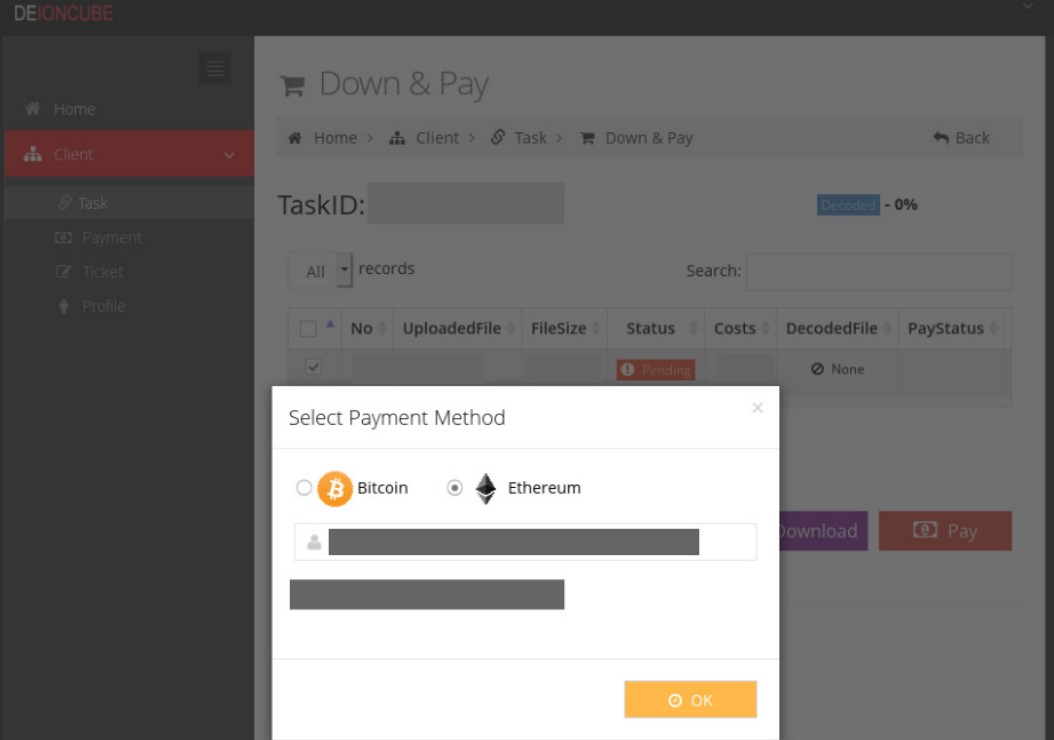
It is possible that the amount of stolen cryptocurrency is much larger as the threat actors are likely using additional wallets unknown to the Proofpoint researchers.
With the wide range of malicious activity conducted by the TA406 and Kimsuky hackers, we should continue to see them conducting further attacks on behalf of the North Korean government.
“Proofpoint anticipates this threat actor will continue to conduct corporate credential theft operations frequently, targeting entities of interest to the North Korean government,” says the Proofpoint researchers.
These attacks include further targeting of US defense contractors and nuclear research agencies to steal valuable intelligence that the North Korean government can use.