KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says they have discovered new attacks conducted by the Russian state-sponsored Nobelium hacking group, including a hacked Microsoft support agent’s computer that exposed customer’s subscription information.
Nobelium is Microsoft’s name for a state-sponsored hacking group believed to be operating out of Russia responsible for the SolarWinds supply-chain attacks.
In a new blog post published Friday night, Microsoft states that the hacking group has been conducting password spray and brute-force attacks to gain access to corporate networks.
Password spray and brute force attacks are similar in that they both attempt to gain unauthorized accounts to an online account by guessing a password. However, password spray attacks will attempt to use the same passwords across multiple accounts simultaneously to evade defenses. In contrast, brute force attacks repeatedly target a single account with different password attempts.
Microsoft says that Nobelium’s recent attacks have been mostly unsuccessful. However, they know of three entities that were breached by Nobelium in these attacks.
“This activity was targeted at specific customers, primarily IT companies (57%), followed by government (20%), and smaller percentages for non-governmental organizations and think tanks, as well as financial services,” Microsoft said in a blog post about the attacks.
“The activity was largely focused on US interests, about 45%, followed by 10% in the UK, and smaller numbers from Germany and Canada. In all, 36 countries were targeted.”
Also Read: 3 Reasons Why You Must Take a PDPA Singapore Course
During the investigation into the attacks, Microsoft also detected an information-stealing trojan on a Microsoft customer support agent’s computer that provided access to “basic account information” for a limited number of customers.
Nobelium used this customer information in targeted phishing attacks against Microsoft customers.
Microsoft reported these attacks after Reuters obtained an email sent to affected customers warning them that the threat actors gained access to information about their Microsoft Services subscriptions.
“A sophisticated Nation-State associated actor that Microsoft identifies as NOBELLIUM accessed Microsoft customer support tools to review information regarding your Microsoft Services subscriptions,” read the Microsoft email obtained by Reuters.
The Nobelium hacking group, also known as APT29, Cozy Bear, and The Dukes, has been attributed to the recent SolarWinds supply chain attack that compromised numerous US companies, including Microsoft, FireEye, Cisco, Malwarebytes, Mimecast, and various US government agencies.
As part of these attacks, the threat actors replaced legitimate modules in the SolarWinds Orion IT monitoring platform that were distributed to customers via the software’s normal auto-update process. These malicious modules allowed the threat actors to gain remote access to compromised devices, where further internal attacks could be launched.
In April, the US government formally accused the Russian government and hackers from the Russian Foreign Intelligence Service, the SVR, of the attacks on Solarwinds and US interests.
More recently, Microsoft revealed that the hacking group compromised the Constant Contact account for USAID, a US agency responsible for providing foreign aid and development assistance.
Using this marketing account, Nobelium conducted targeted phishing attacks to distribute malware and access internal networks.
Also Read: The Difference Between GDPR and PDPA under 10 Key Issues
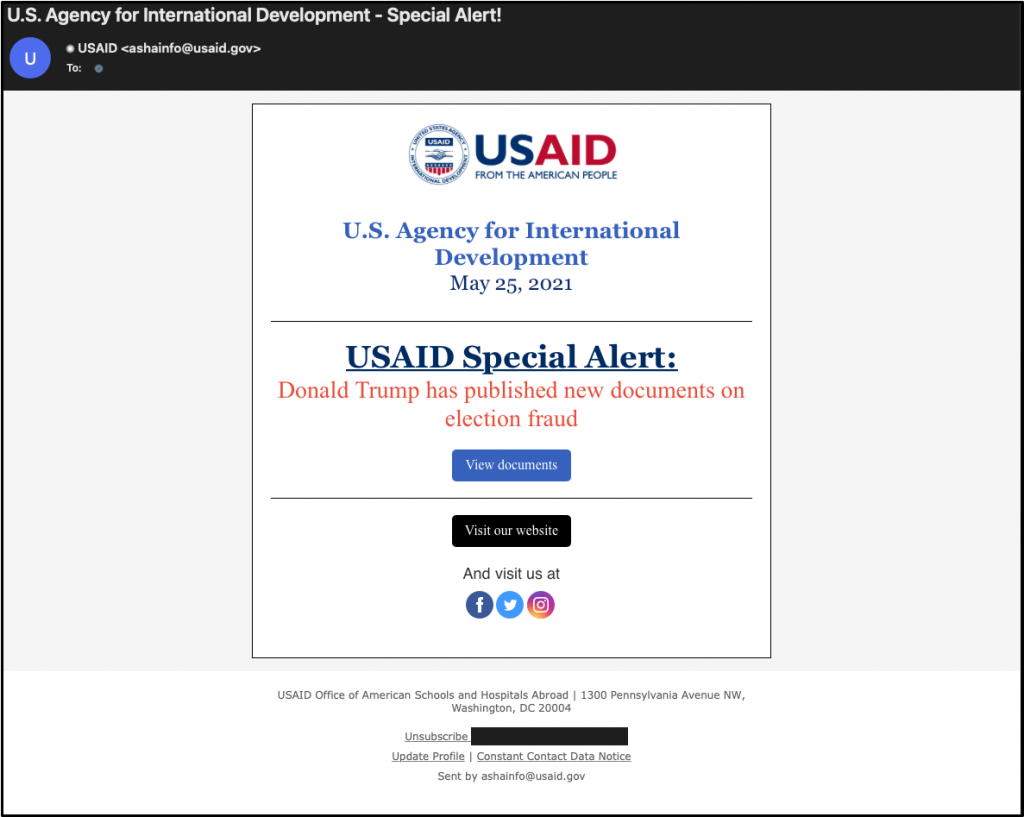
The US Department of Justice later seized two domains used in the phishing attacks to distribute malware.