KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Digital threat researchers at Citizen Lab have uncovered a new zero-click iMessage exploit used to deploy NSO Group’s Pegasus spyware on devices belonging to Bahraini activists.
In total, nine Bahraini activists (including members of the Bahrain Center for Human Rights, Waad, Al Wefaq) had their iPhones hacked in a campaign partially orchestrated by a Pegasus operator linked with high confidence to the government of Bahrain by Citizen Lab.
The spyware was deployed on their devices after being compromised using two zero-click iMessage exploits (that do not require user interaction): the 2020 KISMET exploit and a new never-before-seen exploit dubbed FORCEDENTRY (previously tracked by Amnesty Tech as Megalodon).
While protecting against the iMessage exploits would only require disabling iMessage and FaceTime, NSO Group has also used exploits targeting other messaging apps, including WhatsApp.
Furthermore, disabling iMessage will lead to other issues, including sending unencrypted messages that a resourceful threat actor could easily intercept.
Unfortunately, until Apple issues security updates to address the flaws targeted by NSO Group’s FORCEDENTRY exploit, the only thing potential targets could do to protect themselves is to disable all apps the Israeli surveillance firm could potentially target.
Also Read: Top 3 Common Data Protection Mistakes, Revealed
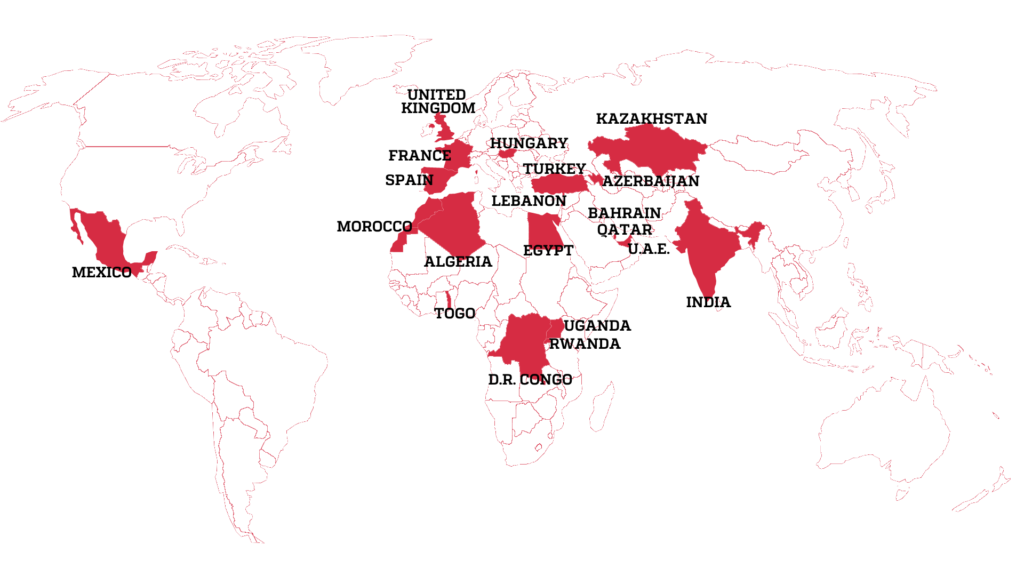
The attacks revealed by Citizen Lab in today’s report are part of just one of a long string of reports and papers documenting NSO Group’s Pegasus spyware used to spy on journalists and human rights defenders (HRDs) worldwide.
Pegasus, a spyware tool developed by Israeli surveillance firm NSO Group, is marketed as surveillance software “licensed to legitimate government agencies for the sole purpose of investigating crime and terror.”
Two years ago, Facebook sued Israeli cyber-surveillance firm NSO Group for creating and selling a WhatsApp zero-day exploit used to infect the devices of high-profile targets such as government officials, diplomats, and journalists with spyware.
Also Read: The Financial Cost of Ransomware Attack
Citizen Lab revealed in 2018 that they discovered some Pegasus licensees using it for cross-border surveillance in countries with state security services that had a history of abusive behavior.
Last but not least, Human rights non-governmental organization Amnesty International and non-profit project Forbidden Stories revealed in a separate July report that NSO Group-made spyware was deployed on iPhones running Apple’s latest iOS release using zero-click iMessage exploits targeting multiple iOS zero-days.
Citizen Lab independently observed Pegasus deployed on an iPhone 12 Pro Max running iOS 14.6 (the OS’s latest release), hacked using a zero-day zero-click iMessage exploit, which did not require interaction from the targets.
“The mechanics of the zero-click exploit for iOS 14.x appear to be substantially different than the KISMET exploit for iOS 13.5.1 and iOS 13.7, suggesting that it is in fact a different zero-click iMessage exploit,” Citizen Lab said at the time.
“These most recent discoveries indicate NSO Group’s customers are currently able to remotely compromise all recent iPhone models and versions of iOS,” Amnesty International and Forbidden Stories added.
An Apple spokesperson was not available for comment when contacted by BleepingComputer earlier today.