





A new and still under development ransomware strain is being used in highly targeted attacks against enterprise entities as Broadcom’s Symantec Threat Hunter Team discovered.
The malware, dubbed Yanluowang ransomware (after a Chinese deity Yanluo Wang, one of the ten kings of hell) based on the extension it adds to encrypted files on compromised systems.
It was recently spotted while investigating an incident involving a high-profile organization after detecting suspicious activity involving the legitimate AdFind command line Active Directory query tool.
AdFind is commonly used by ransomware operators for reconnaisance tasks including gaining access to information needed for lateral movement through their victims’ networks.
Also Read: 6 ways to recognize a potential phishing scam and what to do if you receive one
Within days of the researchers spotting the suspicious AdFind use, the attackers also attempted to deploy their Yanluowang ransomware payloads across the breached organization’s systems.
Before being deployed on compromised devices, the ransomware operators launch a malicious tool designed to carry out the following actions:
Once deployed, Yanluowang will stop hypervisor virtual machines, end all processes harvested by the precursor tool (including SQL and Veeam), encrypts files and appends the .yanluowang extension.
On encrypted systems, Yanluowang also drops a ransom note named README.txt that warns its victims not to reach out to law enforcement or ask ransomware negotiation firms for help.
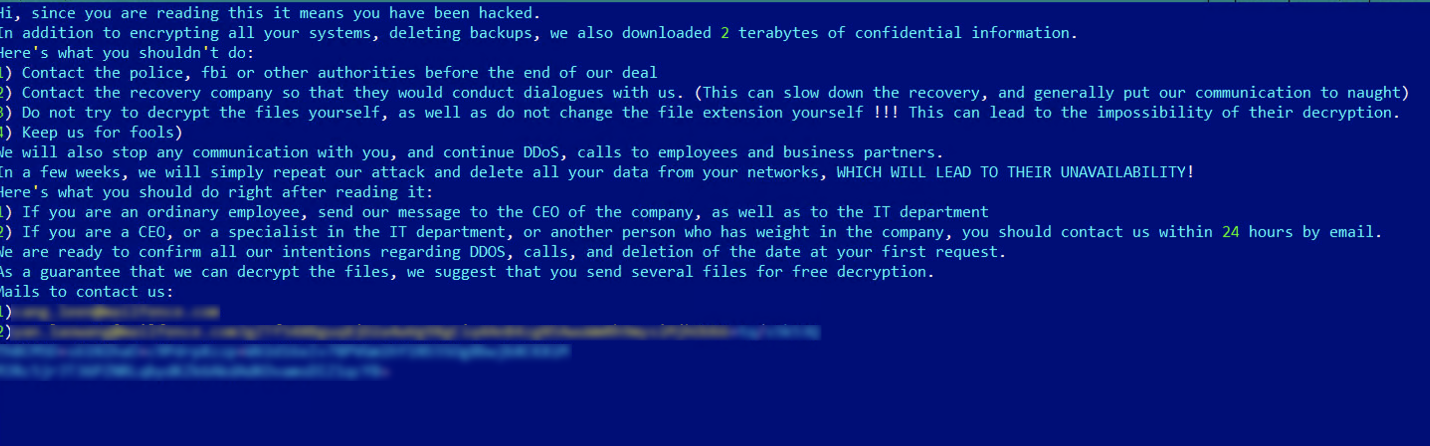
“If the attackers’ rules are broken the ransomware operators say they will conduct distributed denial of service (DDoS) attacks against the victim, as well as make ‘calls to employees and business partners’,” the Broadcom researchers added.
“The criminals also threaten to repeat the attack “in a few weeks” and delete the victim’s data,” a common tactic used by most ransomware gangs to pressure their victims into paying the ransom.
Indicators of compromise including malware hashes can be found at the end of Symantec Threat Hunter Team’s report.
Also Read: How does ransomware happen? Here are 7 ways to prevent them
Even though under development, the Yanluowang is still dangerous malware given that ransomware is one of the biggest threats organizations are facing worldwide.
The White House National Security Council facilitates this week a series of meetings between senior officials from over 30 countries in a virtual international counter-ransomware event to join US efforts to crack down on ransomware cybercrime groups.
After the ransomware attacks on Colonial Pipeline and JBS this summer, Deputy National Security Advisor Anne Neuberger also told U.S. businesses to take ransomware seriously.