KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Another zero day vulnerability in Windows Print Spooler can give a threat actor administrative privileges on a Windows machine through a remote server under the attacker’s control and the ‘Queue-Specific Files’ feature.
Last month, a security researcher accidentally revealed a zero-day Windows print spooler vulnerability known as PrintNightmare that Microsoft tracks as CVE-2021-34527.
Exploiting this vulnerability lets a threat actor increase privileges on a machine or execute code remotely.
Also Read: Vulnerability Assessment vs Penetration Testing: And Why You Need Both
Microsoft released a security update to fix the vulnerability but researchers determined that the patch could be bypassed under certain conditions.
Since the incomplete fix, security researchers have been heavily scrutinizing the Windows printing APIs and have found further vulnerabilities affecting the Windows print spooler.
Security researcher and Mimikatz creator Benjamin Delpy has publicly disclosed a new zero-day vulnerability that allows a threat actor to easily achieve SYSTEM privileges on a Windows machine through a remote print server under their control.
In a conversation with BleepingComputer, Delpy said that his exploit uses the ‘Queue-Specific Files‘ feature of the Windows Point and Print capability to automatically download and execute a malicious DLL when a client connects to a print server under an attacker’s control.
“At printer installation time, a vendor-supplied installation application can specify a set of files, of any type, to be associated with a particular print queue,” explains Microsoft’s documentation on the ‘Queue-Specific Files‘ feature.
“The files are downloaded to each client that connects to the print server.”
To exploit the vulnerability, the researcher created a print server accessible over the Internet with two shared printers that use the queue-specific files feature.
When executing the malicious DLL, it will run with SYSTEM privileges and could be used to run any command on the computer.
Will Dormann, a vulnerability analyst for CERT/CC, has released an advisory for this vulnerability that provides further information.
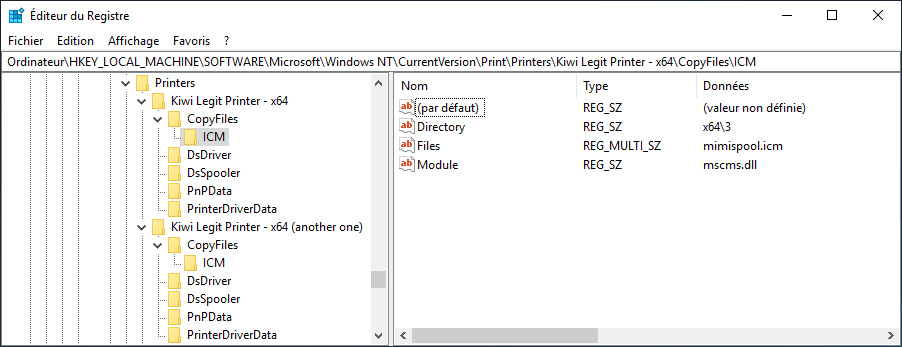
“While Windows enforces that driver packages themselves are signed by a trusted source, Windows printer drivers can specify queue-specific files that are associated with the use of the device. For example, a shared printer can specify a CopyFiles directive for arbitrary ICM files,” the new CERT advisory explains.
“These files, which are copied over with the digital-signature-enforced printer driver files are not covered by any signature requirement. That is, any file can be copied to a client system via Point and Print printer driver installation, where it can be used by another printer with SYSTEM privileges.”
“This allows for LPE on a vulnerable system.”
What makes this vulnerability so dangerous is that it affects all current versions of Windows and allows a threat actor to gain limited access to a network and instantly achieve SYSTEM privileges on the vulnerable device.
Using this access, threat actors can spread laterally through the network until they gain access to a domain controller.
Delpy has created a publicly accessible remote print server that can be used to test the vulnerability demonstrated above.
The good news is that Delpy and Dormann have shared two methods that can be used to mitigate this new ‘Queue-specific files’ vulnerability.
Both of these methods are outlined in the CERT advisory.
As Delpy’s public exploit uses a remote print server, you can block outbound SMB traffic to prevent access to the remote computer.
However, Dormann states that the MS-WPRN can also be used to install drivers without using SMB, and threat actors could still use this technique with a local printer server.
Therefore, this mitigation is not a fail-safe method of blocking the exploit.
A better way to prevent this exploit is to restrict Point and Print to a list of approved servers using the ‘Package Point and print – Approved servers’ group policy.
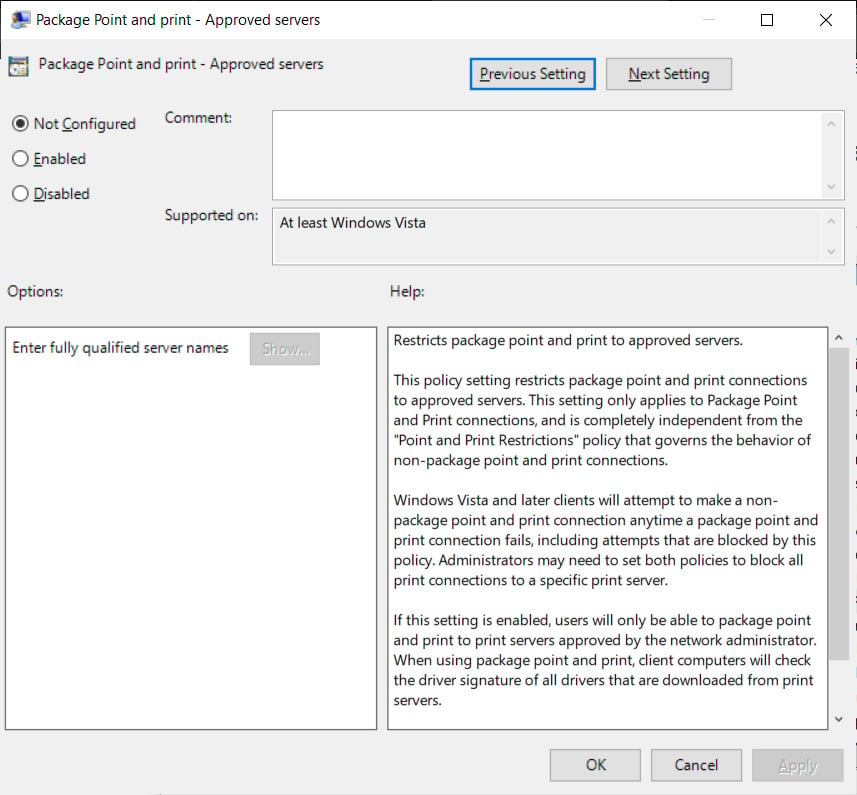
This policy prevents non-administrative users from installing print drivers using Point and Print unless the print server is on the approved list.
Using this group policy will provide the best protection against the known exploit.
Also Read: When to Appoint a Data Protection Officer