KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Cybersecurity firm CrowdStrike has discovered the malware used by the SolarWinds hackers to inject backdoors in Orion platform builds during the supply-chain attack that led to the compromise of several companies and government agencies.
Sunspot, as it was dubbed by CrowdStrike, was dropped by the attackers in the development environment of SolarWinds’ Orion IT management software.
After being executed, the malware would monitor and automatically injecting a Sunburst backdoor by replacing the company’s legitimate source code with malicious code.
“The design of SUNSPOT suggests StellarParticle developers invested a lot of effort to ensure the code was properly inserted and remained undetected, and prioritized operational security to avoid revealing their presence in the build environment to SolarWinds developers,” CrowdStrike found.
“This highly sophisticated and novel code was designed to inject the SUNBURST malicious code into the SolarWinds Orion platform without arousing the suspicion of our software development and build teams,” SolarWinds CEO Sudhakar Ramakrishna added.
Also Read: Key PDPA Amendments 2019/2020 You Should Know
This is the third malware strain found while investigating the SolarWinds supply-chain attack and associated with the threat actor tracked as StellarParticle(CrowdStrike), UNC2452(FireEye), and Dark Halo (Volexity).
A second one is the Sunburst (Solorigate) backdoor malware deployed by the SolarWinds hackers on the systems of organizations who installed trojanized Orion builds via the platform’s built-in automatic update mechanism.
After recovering several Sunburst samples that delivered different payloads, FireEye found a third malware named Teardrop, which is a previously unknown memory-only dropper and a post-exploitation tool used to deploy customized Cobalt Strike beacons.
A fourth malware, not linked to the StellarParticle hackers but also delivered using trojanized Orion builds, was also discovered by Palo Alto Networks Unit 42 and Microsoft while investigating the SolarWinds supply-chain attack
This additional malware, dubbed SuperNova, was deployed as a DLL file that allowed attackers to remotely send, compile, and execute C# code on compromised machines.
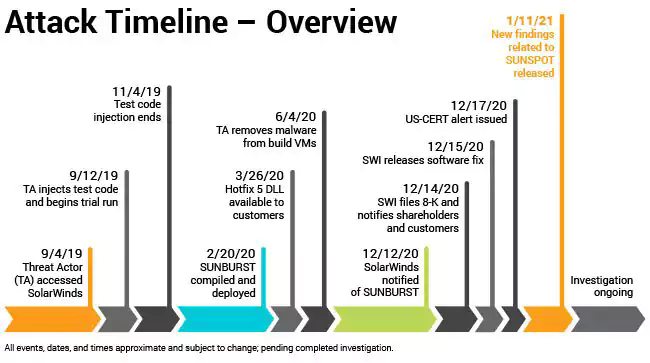
While we learned of the SolarWind hack on December 13th, the first disclosure of its consequences was made on December 8th by leading cybersecurity firm FireEye which revealed that it was hacked by a nation-state hacking group.
As part of the attack, the hackers gained access to the SolarWinds Orion build system and injected the sunburst backdoor into a legitimate DLL used by the SolarWinds Orion IT management software. This DLL was later automatically distributed to SolarWinds customers in a supply chain attack.
Even though the timeline of the SolarWinds attack starts in September 2019, the date when the earliest suspicious activity was found on SolarWinds internal network, the identity of the hacking group behind this supply-chain attack is still unknown.
However, Kaspersky was the first to make a connection between the SolarWinds hackers and a previously known cyber-espionage group after finding that the Sunburst backdoor has feature overlaps with Kazuar, a .NET backdoor tentatively linked to the Russian Turla hacking group.
“The identified connection does not give away who was behind the SolarWinds attack, however, it provides more insights that can help researchers move forward in this investigation,” Costin Raiu, director of Kaspersky’s Global Research and Analysis Team (GReAT), said.
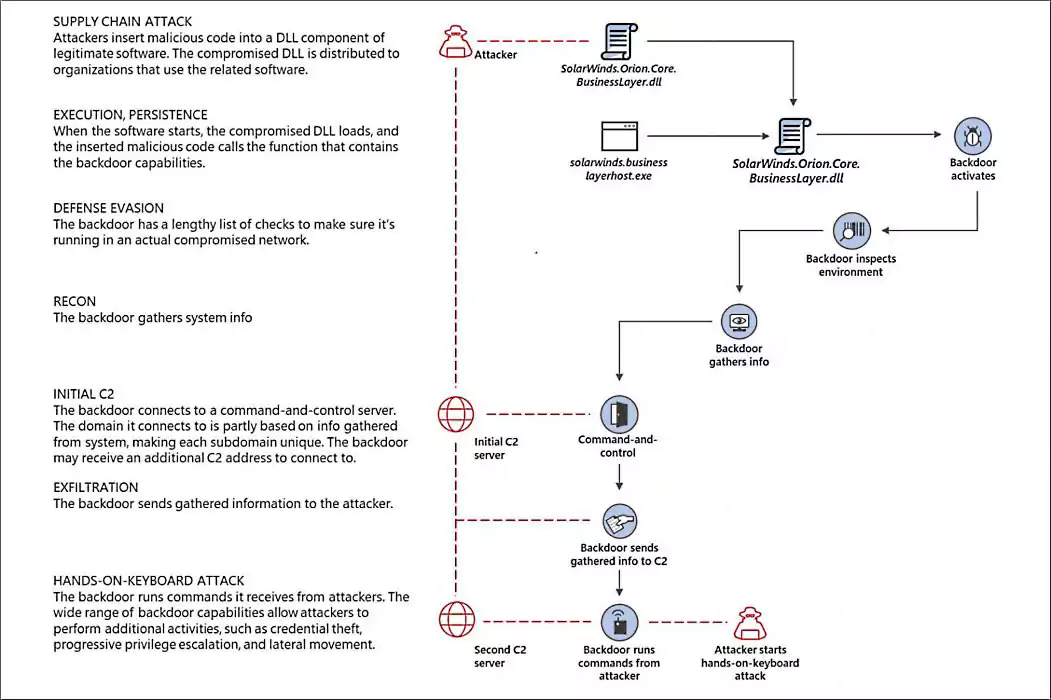
A week ago, the FBI, CISA, and the NSA also disclosed in a joint statement that a Russian-backed Advanced Persistent Threat (APT) group is likely behind the SolarWinds hack.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
“The U.S. government and many private-sector experts have stated the belief that a foreign nation-state conducted this intrusive operation as part of a widespread attack against America’s cyberinfrastructure,” SolarWinds CEO Sudhakar Ramakrishna said today.
“To date, our investigations have not independently verified the identity of the perpetrators.”