KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





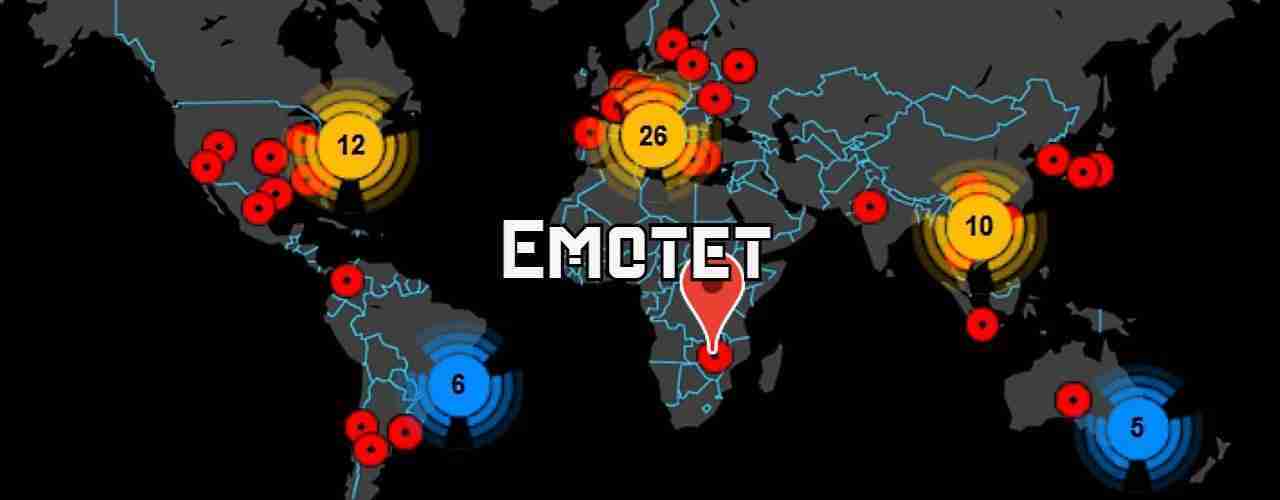
A new service has been launched that allows you to check if an email domain or address was in an Emotet spam campaign.
Emotet is a malware infection that spreads through spam emails containing malicious Word or Excel documents. When opened and macros are enabled, it will install the Emotet trojan on a victim’s computer.
When infected, Emotet will steal a victim’s email and transmit it back to servers under the attacker’s control. These emails will then be used as part of future spamming campaigns to make the malicious spam look legitimate.
Over time, the Emotet trojan will download and install other malware such as TrickBot and QakBot on an infected user’s computer. These trojans are known to lead to ransomware attacks by the operators of Ryuk, Conti, and ProLock.
Also Read: How To Send Mass Email Without Showing Addresses: 2 Great Workarounds
Today, Italian cybersecurity company TG Soft launched a new service launched called Have I Been Emotet that allows you to check if a domain or email address was used as a sender or recipient in Emotet spam campaigns.
TG Soft has told BleepingComputer that their database consists of monitored outgoing emails generated by Emotet between August and September 23rd, 2020.
During this period, they have collected over 2.1 million email addresses from around 700,000 outgoing emails.
To use the service, you can enter a domain or email address, and it will let you know how many times it was used.
To use the service, you can just enter a domain or email address, and it will let you know how many times the email address or domain was used as the sender of an email or the recipient.
When returning the search result, Have I Been Emotet will provide the following information:
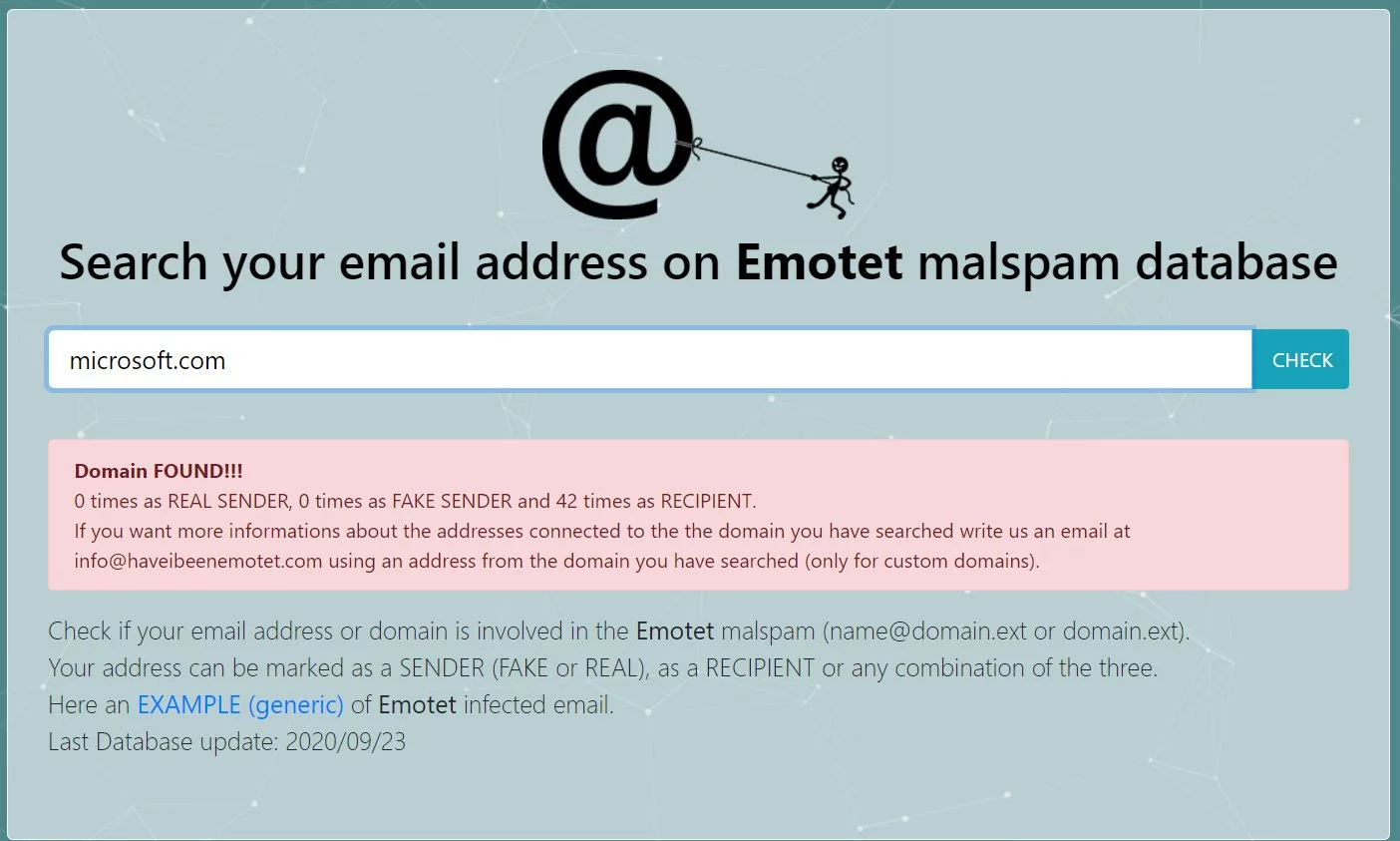
For example, in the image below, you can see that users in the microsoft.com domain were targeted 42 times in recent Emotet spam campaigns.
If a company has been affected by a cyberattack, you can check if they have been targeted in Emotet spam campaigns, leading to a ransomware attack.
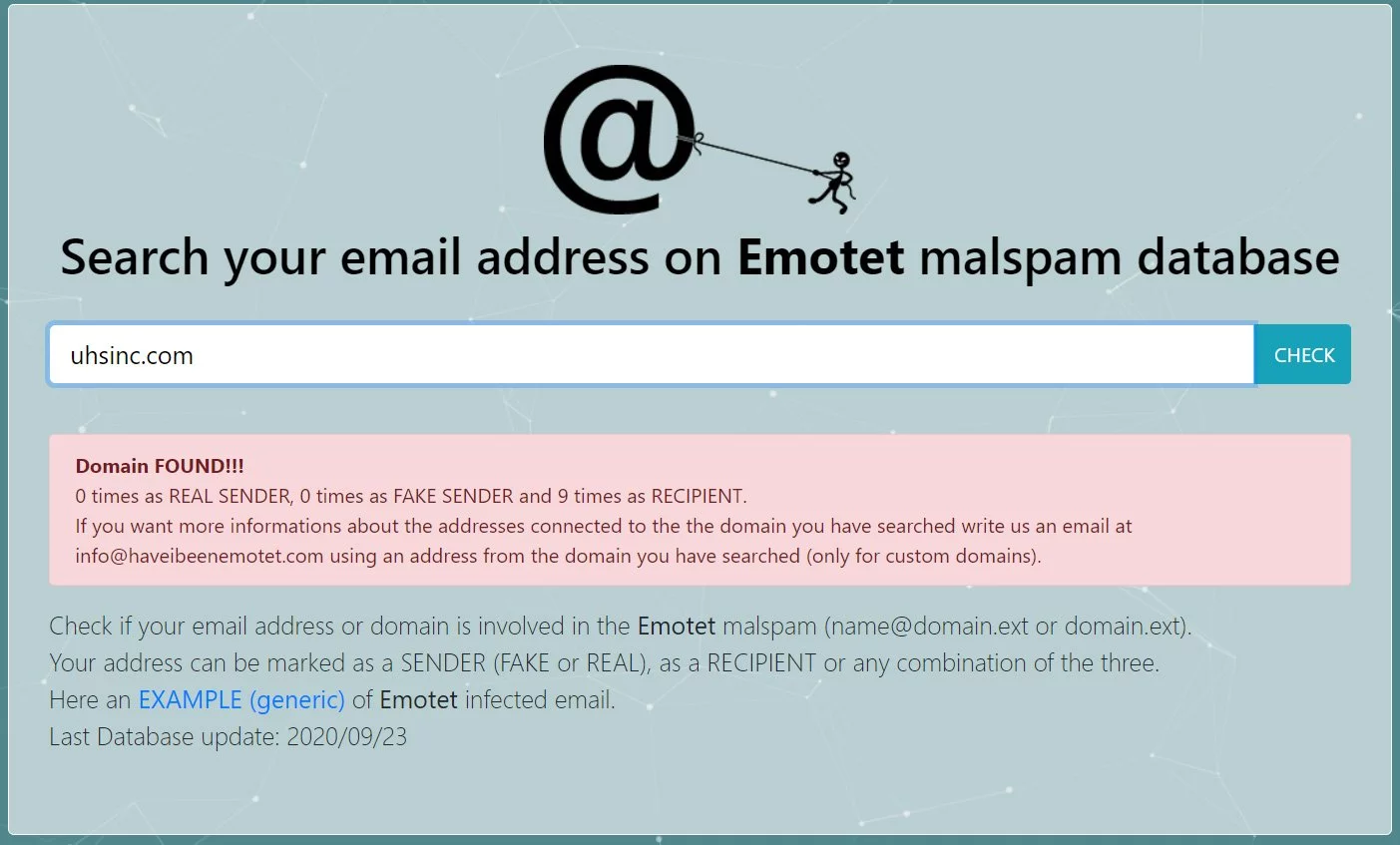
For example, Ryuk ransomware recently attacked the healthcare giant Universal Health Services (UHS).
Using this service, we can see that the UHS’ domain, uhsinc.com, was used in recent Emotet campaigns and that the company received Emotet spam nine times.
If you use this service and find that your email address or domain has been used as a recipient, it does not necessarily mean that you have been infected.
To become infected, a user would have had to open the email attachments and enabled macros before the malware would have been installed.
On the other hand, if your domain has users listed as a ‘REAL’ sender, then it is likely that one of your email domain’s users had been infected, and a thorough investigation of your computers should be done.
Also Read: 10 Government Data Leaks In Singapore: Prevent Cybersecurity