KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new phishing campaign uses a trio of enterprise cloud services, Microsoft Azure, Microsoft Dynamics, and IBM Cloud, as part of an attempt to steal your login credentials.
BleepingComputer recently analyzed a new phishing campaign that pretends to from a help desk named “servicedesk.com” that mimics similar wording used by real IT helpdesk domains in corporate environments.
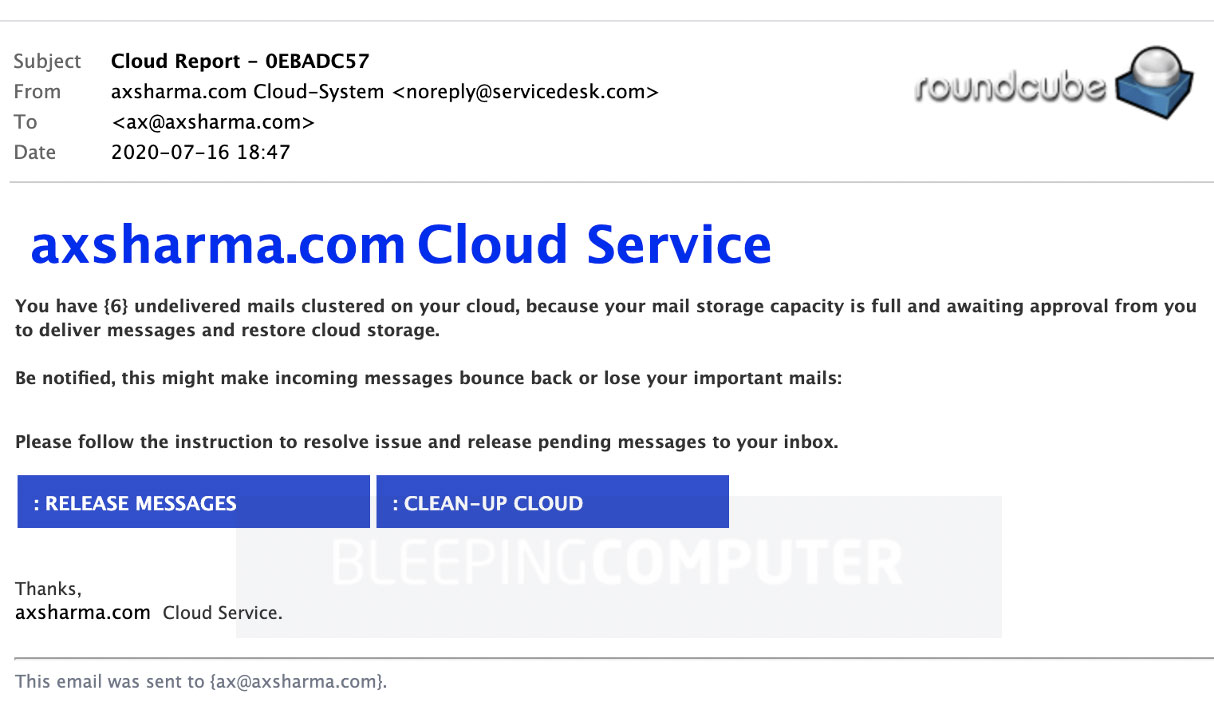
The email imitates a “quarantined mail” notification frequently sent out in workplaces by email security products and spam filters, asking the user to “release” messages stuck in the queue.
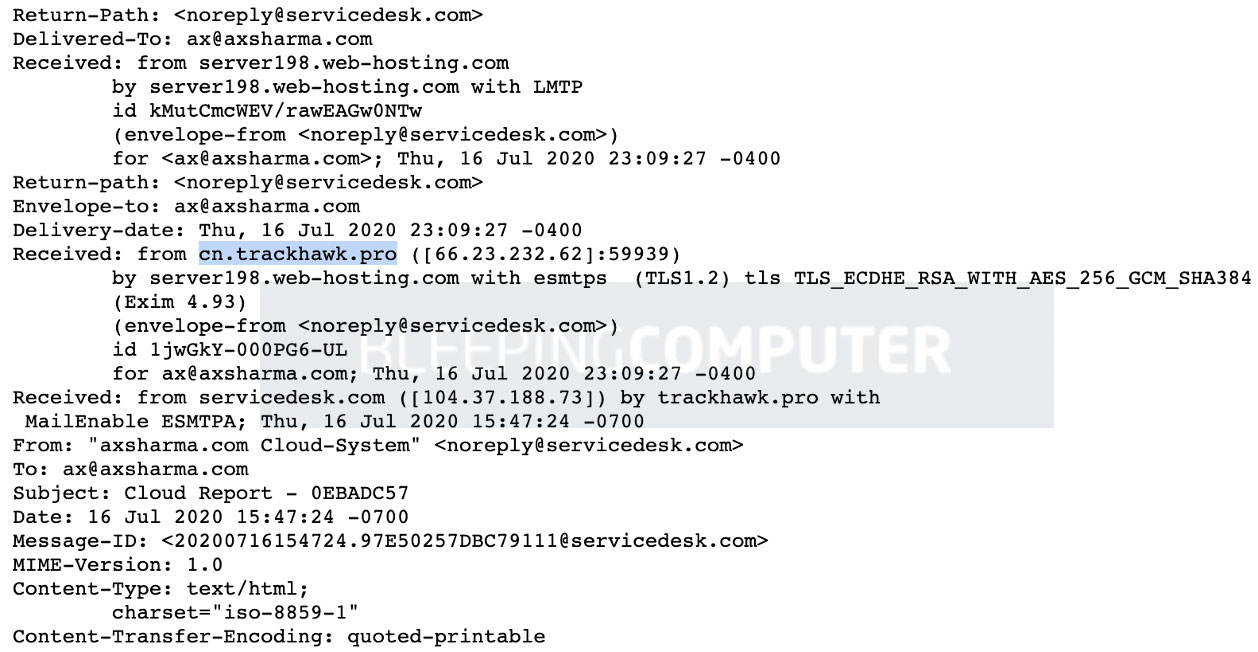
The “From:” (envelope) address in the email is listed as “[email protected],” and while sender domains can easily be spoofed, the mail headers for this phishing campaign show that the email was sent through this domain.
As you can see from the email headers below, the phishing email is sent through an intermediary “cn.trackhawk.pro” domain, but the originating domain is clearly “servicedesk.com.”
In most email spoofing scenarios, a mismatch between the “From:” email domain and the domain listed in the bottommost “Received:” header is a red flag.
In this campaign, the domain “servicedesk.com” is used in the “From:” (envelope) address matches the domain listed in the last “Received:” header, making it more easily bypass spam filters.
These headers indicate one of the two things:
Interestingly, pinging the IP listed in the “Received: from servicedesk.com ([104.37.188.73])” returned timeouts indicating it’s not live.
The “cn.trackhawk.pro” IP (66.23.232.62) however, responds correctly to pings, indicating that scenario #2 is more likely.
And more importantly, lack of DMARC, DKIM and SPF validations on the “servicedesk.com” domain enable spammers to take advantage of this domain as demonstrated in these attacks.
Also read: 9 Policies For Security Procedures Examples
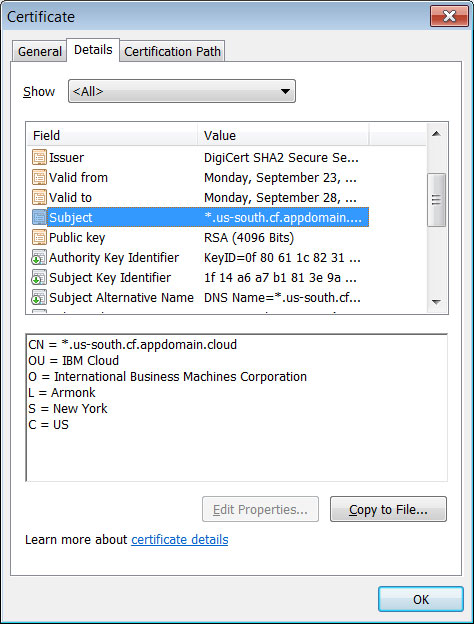
Using three well-known enterprise solutions like IBM Cloud hosting, Microsoft Azure, and Microsoft Dynamics to host the phishing landing pages adds legitimacy to the campaign.
This is especially true as domains hosted on Azure (windows.net) or IBM Cloud automatically get free SSL certificates that contain these companies’ names, adding even more legitimacy.
In the phishing email are buttons labeled “RELEASE MESSAGES” or “CLEAN-UP CLOUD” that, when clicked on, bring the user to a legitimate Microsoft Dynamics 365 URL.
This URL then redirects the user to an IBM Cloud domain, cf.appdomain.cloud used for IBM’s Cloud Foundry deployments, to host the phishing landing page.
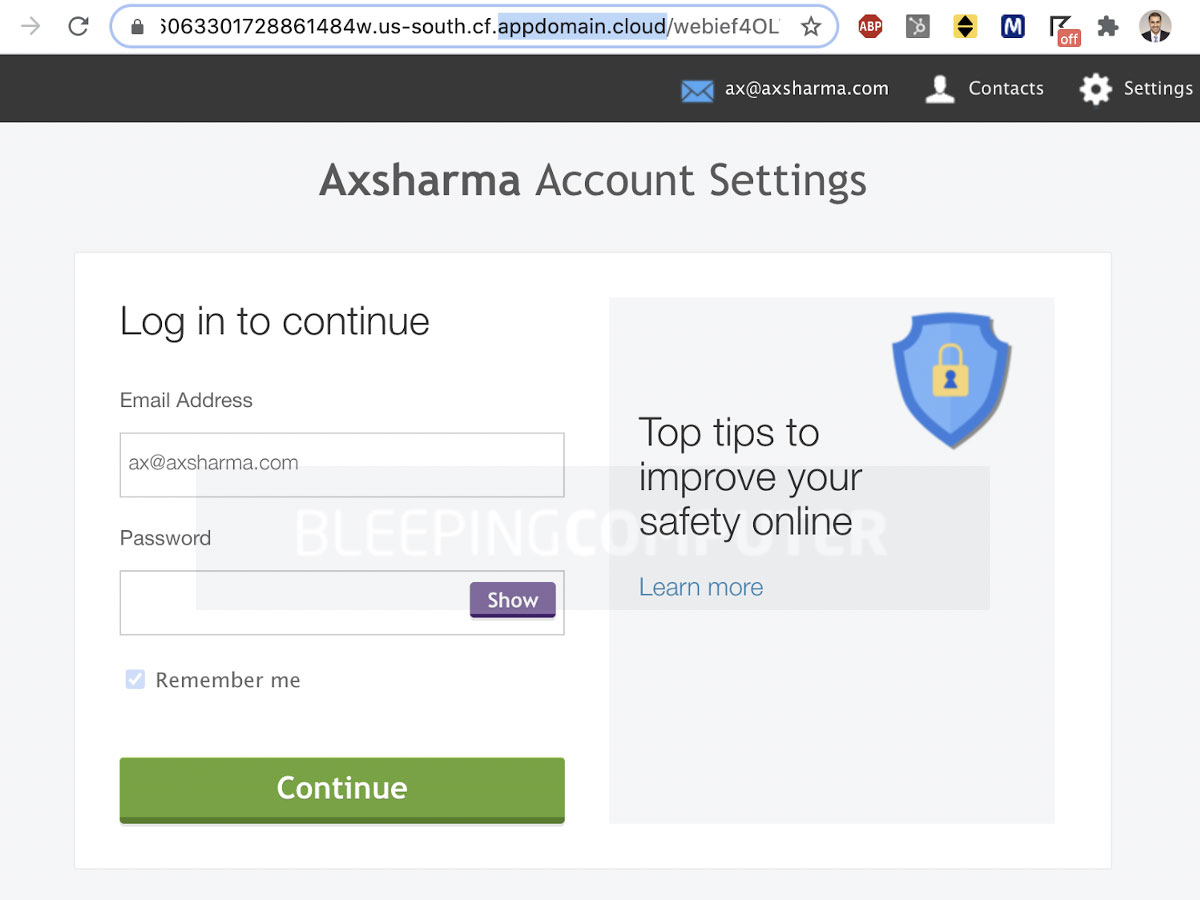
This landing page is designed with some degree of awareness on the attacker’s part as entering a “test” password that is too weak will throw a “wrong password!!” error.
Entering a password of decent length and complexity, perhaps once it matches the criteria set forth by IBM Cloud, will redirect the user to another fake page confirming the settings update host on Microsoft Azures hosting domain, windows.net.
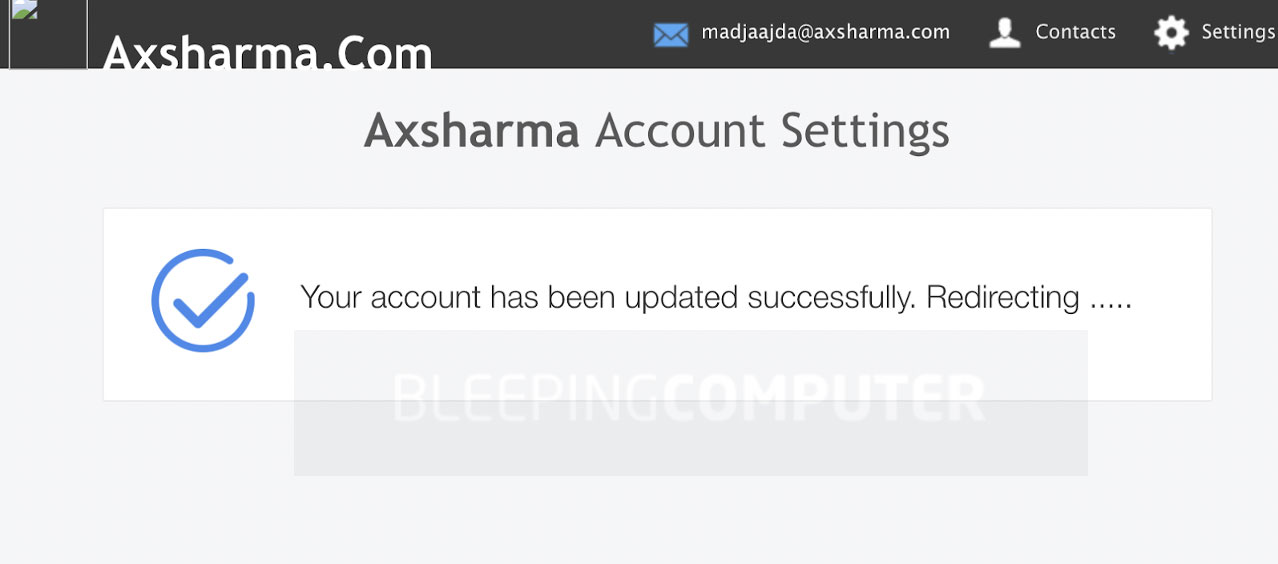
This malicious page eventually redirects the user to the website associated with their email address domain.
In this case, the final destination would be “axsharma.com.”
Phishing emails are an everyday nuisance for both business and personal email users but could lead to very dire consequences, including data theft and enterprise-wide ransomware attacks.
Increasing cases of phishing campaigns abusing legitimate cloud infrastructure are on the rise as they add legitimacy to the phishing attacks and provide free SSL certificates.
This increased complexity allows attackers to potentially bypass spam filters and security products, which leads to a greater need for sophisticated security systems in this never-ending game of cat and mouse.
Also read: 7 Client Data Protection Tips to Keep Customers Safe