KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new malicious package has been spotted this week on the npm registry, which targets NodeJS developers using Linux and Apple macOS operating systems.
The malicious package is called “web-browserify,” and imitates the popular Browserify npm component downloaded over 160 million times over its lifetime.
web-browserify is itself built by combining hundreds of legitimate open-source components, and performs extensive reconnaissance activities on an infected system.
Moreover, as of today, the ELF malware contained with the component has a zero detection rate by all leading antivirus engines.
This week, a malicious component “web-browserify” was found on the npm registry.
The component was detected by Sonatype’s automated malware detection system, Release Integrity, and deemed malicious after analysis by the Sonatype security research team, that I’m a part of.
“web-browserify” is named after the legitimate Browserify component that scores over 1.3 million weekly downloads and used over by 356,000 GitHub repositories.
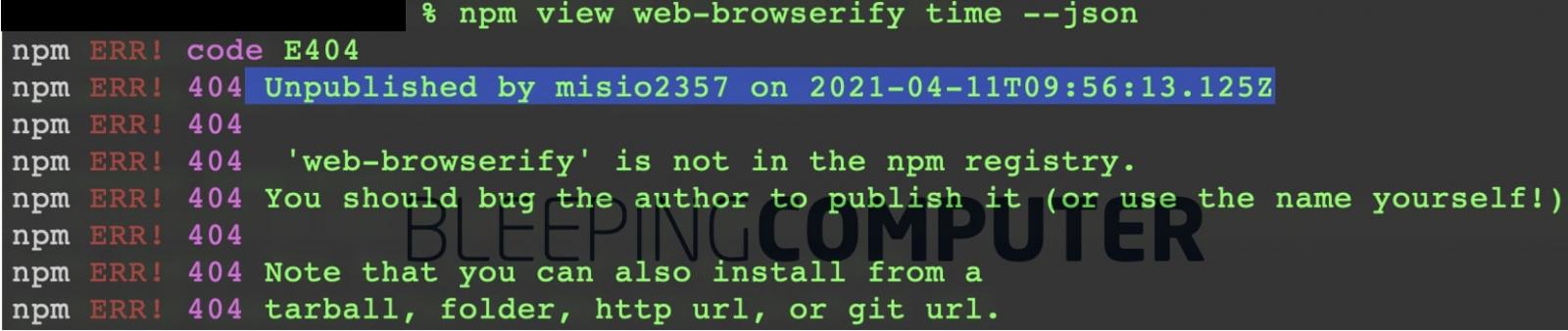
The malicious component, “web-browserify” in contrast is just shy of 50 downloads—before it was pulled from npm within two days of its publishing.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
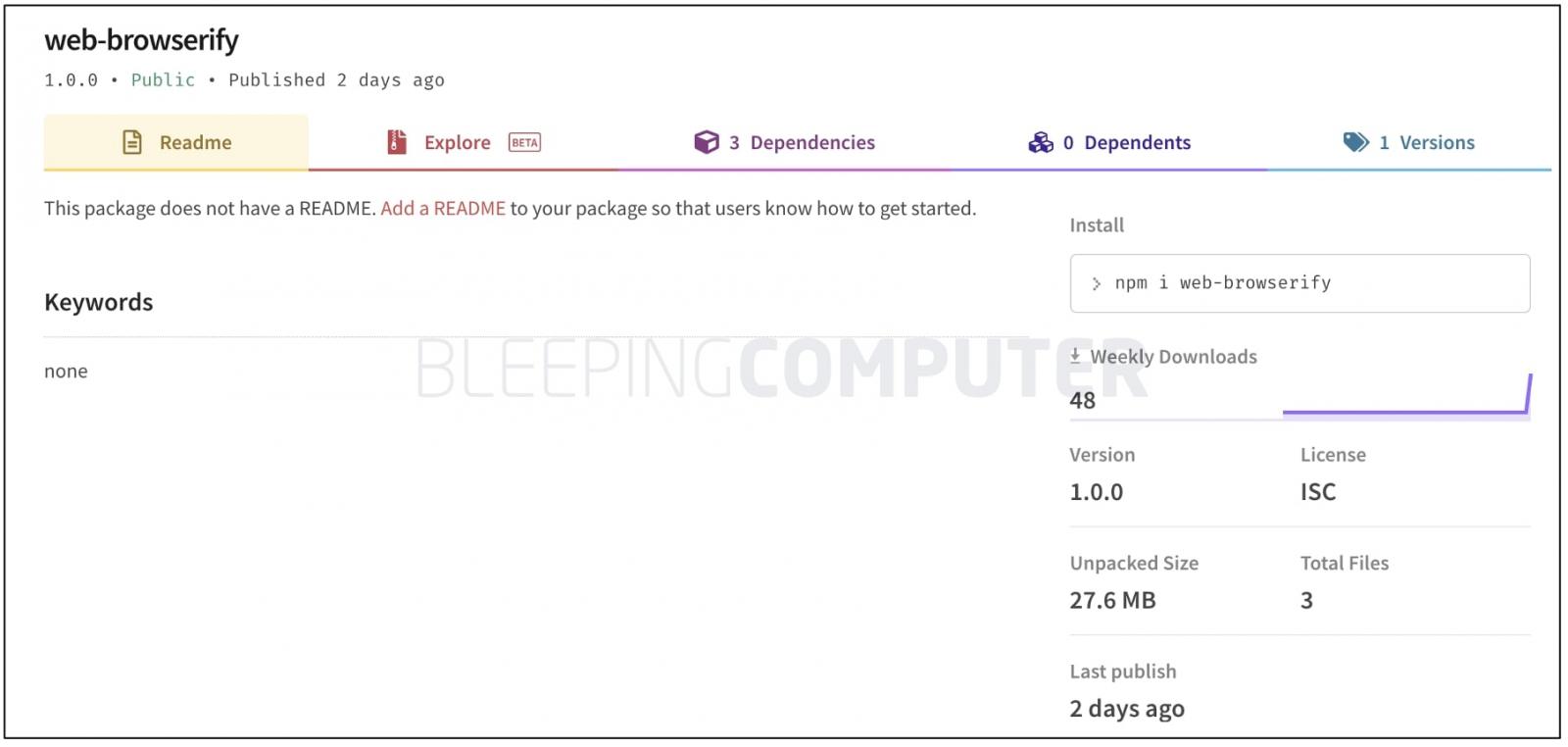
“web-browserify” is created by a pseudonymous author describing themselves to be Steve Jobs.
The package consists of a manifest file, package.json, a postinstall.js script, and an ELF executable called “run” present in a compressed archive, run.tar.xz within the npm component.
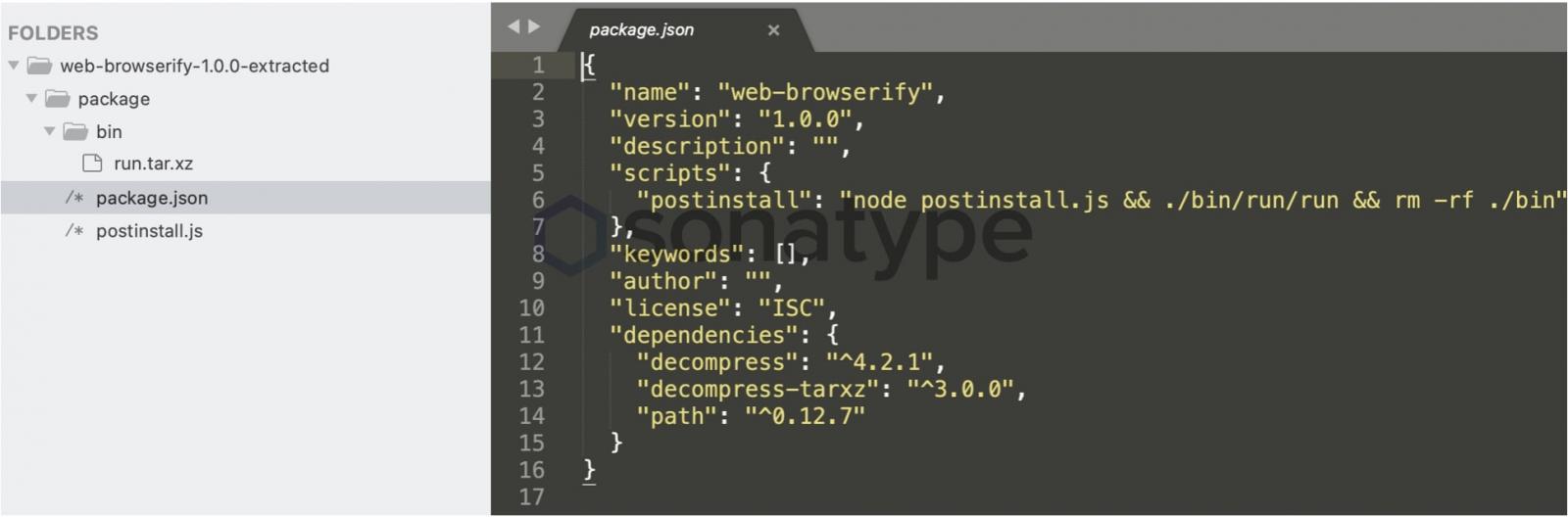
As soon as “web-browserify” is installed by a developer, the scripts extract and launch the “run” Linux binary from the archive, which requests elevated or root permissions from the user.
The extracted run binary is approximately 120 MB in size and has hundreds of legitimate open-source npm components bundled within it, that are being abused for malicious activities.
For example, one such component is the cross-platform “sudo-prompt” module that is used by run to prompt the user for granting the malware root privileges on both macOS and Linux distributions.
Because elevated privileges would be requested almost at the same time “web-browserify” was being installed, the developer may be misled into believing that it is the legitimate installer activities requiring elevated permissions.
As seen by BleepingComputer, once the ELF acquires elevated permissions, it gains persistence on the Linux system and copies itself to /etc/rot1 from where it subsequently runs on every boot:
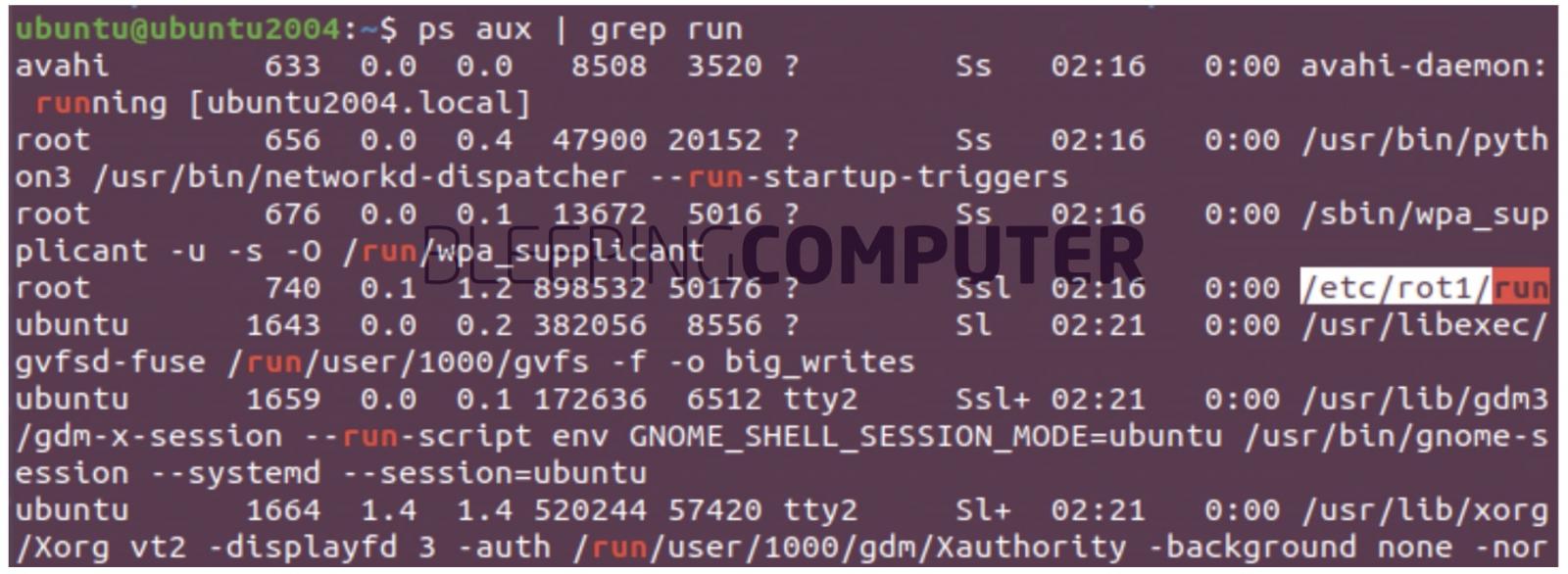
The malware has advanced reconnaissance and fingerprinting capabilities.
It uses another legitimate npm component, systeminformation, to collect the following bits of information from the infected system:
Also Read: What Does A Data Protection Officer Do? 5 Main Things
As confirmed by BleepingComputer at least some of this fingerprinting information is exfiltrated to an attacker-controlled domain over a plaintext (HTTP) connection, as GET parameters:
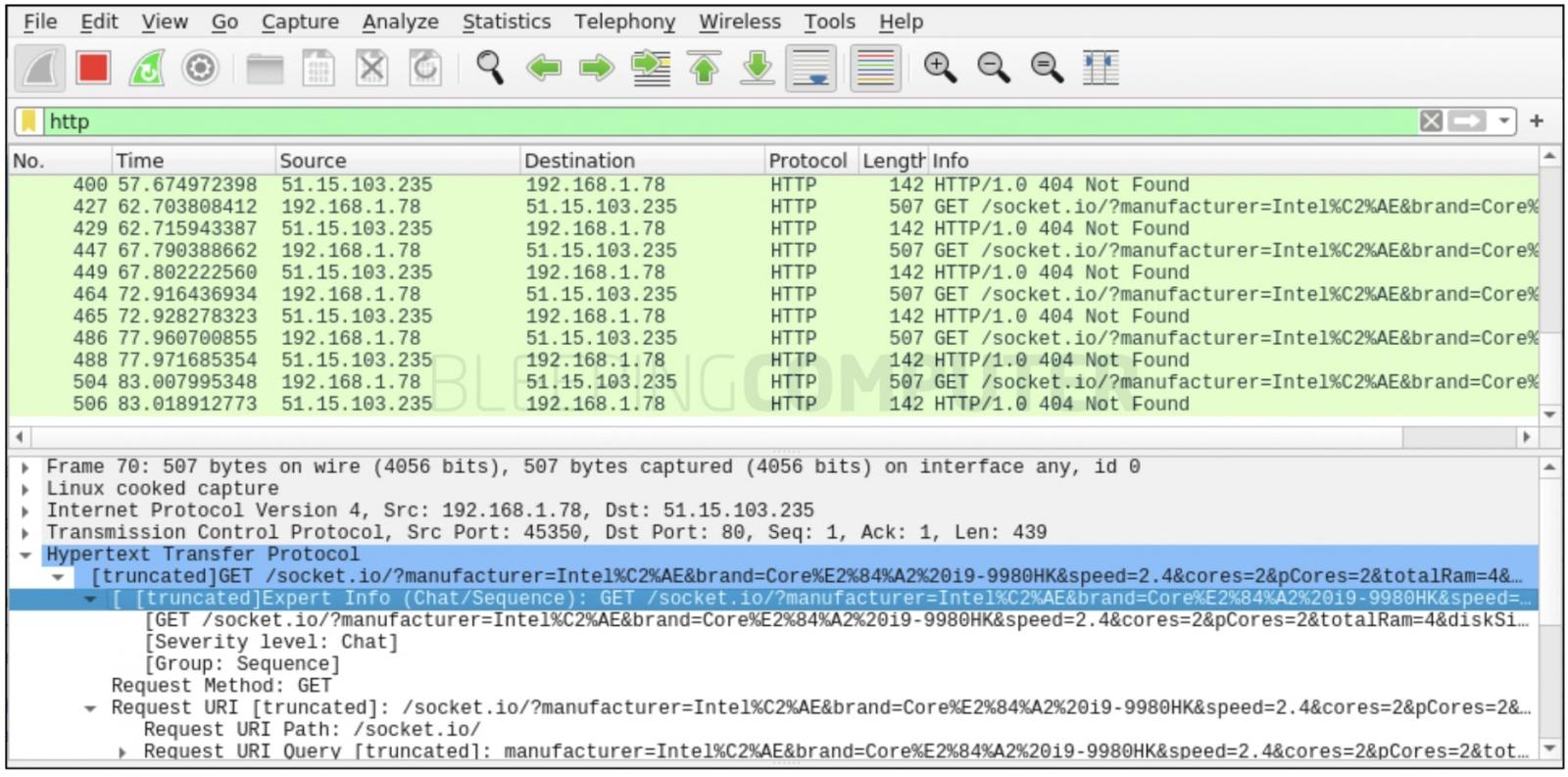
Of particular note is the domain used by the attacker for carrying out these activities: http://me.ejemplo[.]me
Although at the time of our analysis, BleepingComputer observed the server where the domain points to is responding with a 404 (not found), the word ejemplo means “example” in Spanish.
A domain such as ejemplo.me can therefore easily be mistakenly conflated with legitimate test domains, such as example.com cited by applications and their documentation.
Additionally, under certain circumstances, the malware attempts to remove the contents of the /etc/ directory and disable critical Unix services by tampering with the systemctl utilityand the systemd directory.
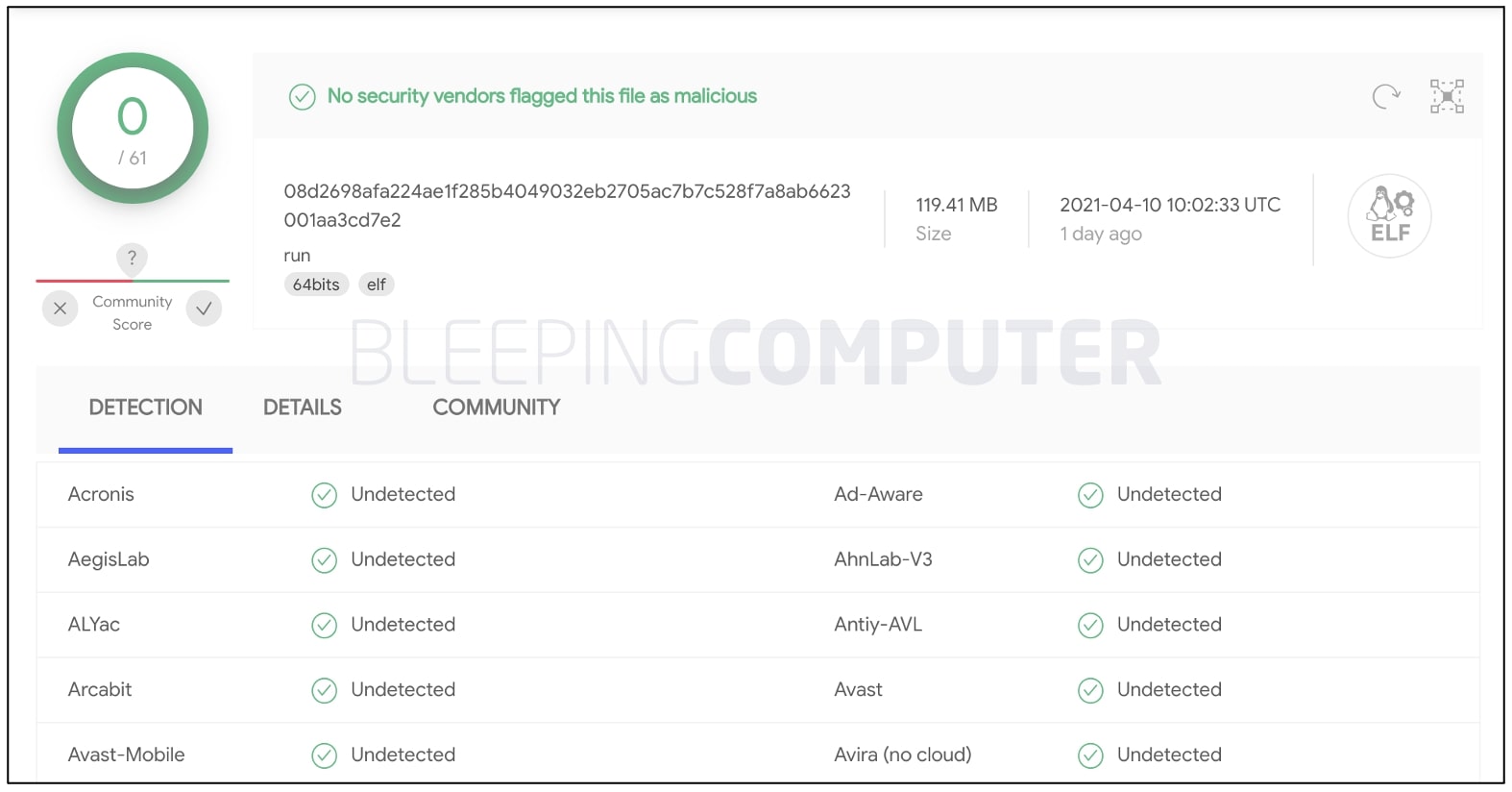
Despite the malware engaging in outright nefarious activities by abusing legitimate open-source components, it has a perfect zero score on VirusTotal, at the time of our analysis.
The fact that it uses genuine software applications to perform shady activities could be one of the reasons that no antivirus engine has been able to flag this sample yet (the sample itself was submitted to VirusTotal on April 10th, 2021).
It also remains a mystery as to why, the “web-browserify” component, although caught by Sonatype, was unpublished by its author almost two days later after its initial publishing.
The discovery of yet another npm malware comes after dependency confusion malware was seen targeting known tech companies.
The full extent of capabilities contained within this malware and its definite purpose are yet to be determined.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
But, the malware’s zero-detection rate and the fact it capitalizes on legitimate open-source components, including the popular Browserify, should raise everyone’s eyebrows for what the next iteration of such an attack might look like.