KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Cybersecurity firms have found a new data wiper used in destructive attacks today against Ukrainian networks just as Russia moves troops into regions of Ukraine.
A data wiper is malware that intentionally destroys data on a device to make the data unrecoverable and for the operating system to no longer work correctly.
Cybersecurity firms Symantec and ESET found the new data wiper, which both state that the malware was used in attacks today.
Also Read: How Being Data Protection Trained Can Help With Job Retention
While Symantec has only shared the hash of the new data-wiper, which is being detected by only 12/70 security engines on VirusTotal, ESET has tweeted a thread providing much greater detail.
According to ESET, the new data wiper is detected as Win32/KillDisk.NCV and was deployed on hundreds of devices on Ukrainian networks today.
While the attack occurred today, ESET notes that the malware was compiled on 12/28/21, indicating that the attacks may have been planned for some time.
“The PE compilation timestamp of one of the sample is 2021-12-28, suggesting that the attack might have been in preparation for almost two months,” tweeted ESET.
From an analysis of the malware by BleepingComputer, the wiper contains four embedded drivers named DRV_X64, DRV_X86, DRV_XP_X64, and DRV_XP_X86, as shown below.
Also Read: Top 25 Data Protection Statistics That You Must Be Informed
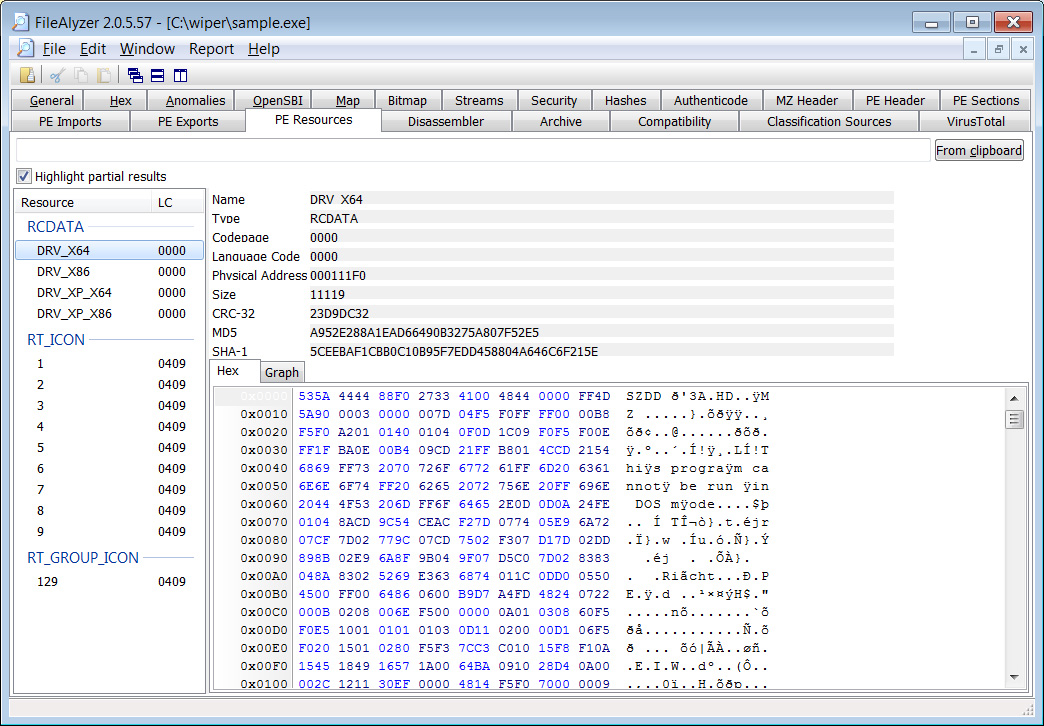
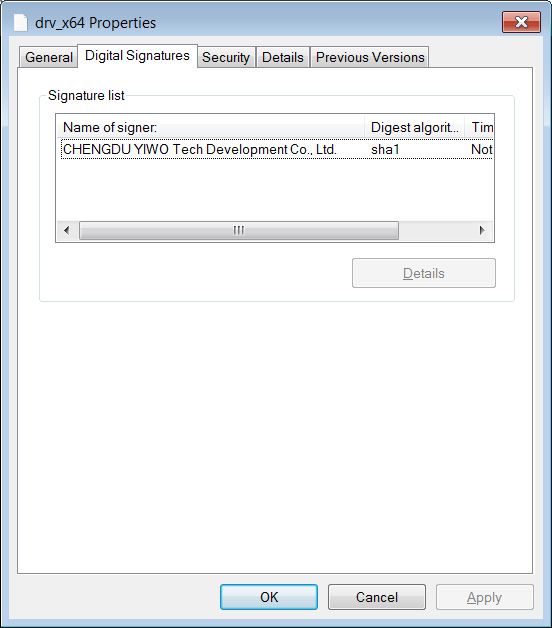
These drivers are compressed using the Windows ‘compress’ command but once expanded, they are signed by ‘CHENGDU YIWO Tech Development Co., Ltd.,’ the owners of the EASUS data recovery and disk management software developers.
When the malware is executed, the wiper will install one of these drivers as a new Windows service.
Strings inside the drivers indicate that they belong to the EASUS Partition Manager program.
Disk
\Device\Harddisk%u\Partition0
\Device\EPMNTDRV
\DosDevices\EPMNTDRVESET believes that these EASUS drivers have been coopted to corrupt the device’s files and then reboots the computer.
Security researcher Silas Cutler has confirmed that the data wiper will also trash the device’s Master Boot Record, making the device unbootable.
ESET warned that in at least one of these attacks, they were not targeted at individual computers and were deployed directly from the Windows domain controller.
This indicates that the threat actors had access to these networks for some time.
“In one of the targeted organizations, the wiper was dropped via the default (domain policy) GPO meaning that attackers had likely taken control of the Active Directory server,” explains ESET.
The details regarding this new data wiper are still developing, and we will update the story as more information becomes available.
For those interested in more technical details, you can follow SentinelOne researcher J. A. Guerrero-Saade’s analysis on Twitter.
This data-wiper is the second one used against Ukrainian networks in the last two months.
In January, Microsoft disclosed that a destructive data-wiping malware disguised as ransomware was used in attacks against multiple Ukrainian organizations.
The January data-wiper was dubbed ‘WhisperGate’ and impersonated a ransomware attack, even targeting specific file extensions and dropping a ransom note.
However, this malware was actually a destructive data wiper that corrupts files and wipes the device’s Master Boost Record, making it impossible to boot into Windows or access files.
While the attacks have not been attributed to Russia, data wipers have been a tool used by Russian state-sponsored threat actors in the past.
A data-wiping attack was conducted in 2017 when threat actors targeted thousands of Ukrainian businesses with the NotPetya ransomware.
In 2020, the USA formally indicted Russian GRU hackers believed to be part of the elite Russian hacking group known as “Sandworm” for the NotPetya attacks.