KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Previously undocumented account-stealing malware distributed via fake software crack sites targets the users of major service providers, including Google, Facebook, Amazon, and Apple.
The malware, dubbed CopperStealer by Proofpoint researchers, is an actively developed password and cookie stealer with a downloader feature that enables its operators to deliver additional malicious payloads to infected devices.
The threat actors behind this malware have used compromised accounts to run malicious ads and deliver additional malware in subsequent malvertising campaigns.
“While we analyzed a sample that targets Facebook and Instagram business and advertiser accounts, we also identified additional versions that target other major service providers, including Apple, Amazon, Bing, Google, PayPal, Tumblr and Twitter,” Proofpoint said in a report published today.
CopperStealers works by harvesting passwords saved in the Google Chrome, Edge, Firefox, Yandex, and Opera web browsers.
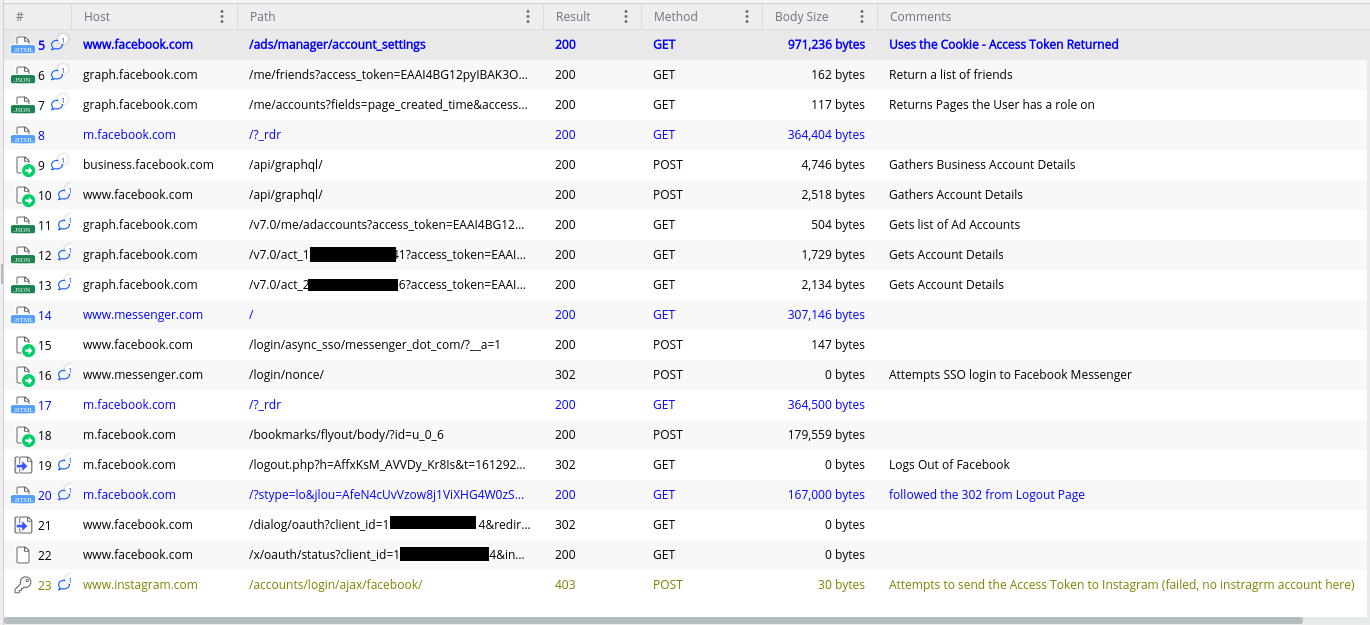
It will also retrieve the victims’ Facebook User Access Token using stolen cookies to collect additional context, including their list of friends, advertisement accounts info, and a list of Facebook pages they can access.
Malware dropped using CopperStealer’s downloader module includes the modular Smokeloader backdoor and a wide array of other malicious payloads downloaded from several URLs.
“While CopperStealer isn’t the most nefarious credential/account stealer in existence, it goes to show that even with basic capabilities, the overall impact can be large,” Proofpoint added.
Also Read: PDPA Singapore Guidelines: 16 Key Concepts For Your Business
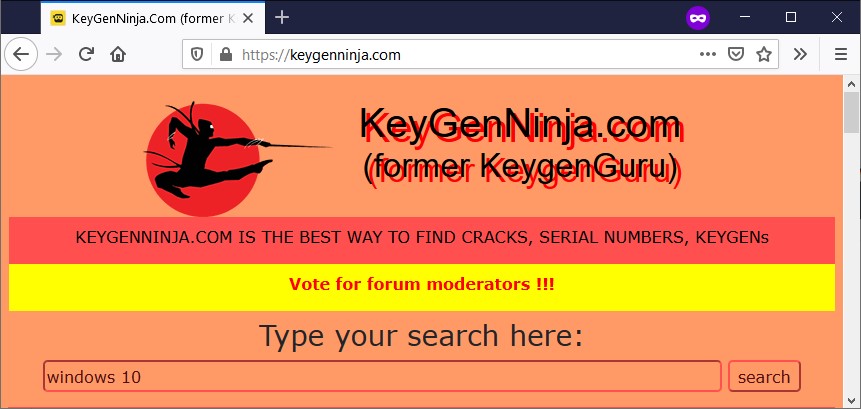
CopperStealer is being distributed via fake software crack sites and known malware distribution platforms such as including keygenninja[.]com, piratewares[.]com, startcrack[.]com, and crackheap[.]net.
Proofpoint worked with Cloudflare and other service providers to set up interstitials for these domains to warn visitors of their malicious nature (however, the interstitials didn’t show up in BleepingComputer’s tests).
Two of the sites were also sinkholed after discovering their connection to ongoing attempts to deliver malware and Potentially Unwanted Programs/Applications (PUP/PUA) software.
“In the first 24 hours of operation, the sinkhole logged 69,992 HTTP Requests from 5,046 unique IP addresses originating from 159 countries representing 4,655 unique infections,” Proofpoint said.
CopperStealer shows similar targeting and delivery methods with the SilentFade malware used to steal browser cookies and promote malicious ads via compromised Facebook accounts, leading to over $4 million in damages.
“Credentials make the world go round when it comes to the current threat landscape and this shows the lengths that threat actors will take to steal valuable credential data,” said Sherrod DeGrippo, Proofpoint senior director of Threat Research.
“CopperStealer is going after big service provider logins like social media and search engine accounts to spread additional malware or other attacks. These are commodities that can be sold or leveraged.”
Also Read: Data Protection Officer Singapore | 10 FAQs
Since account stealing malware like this one provide scammers behind impersonation attacks and identity theft fraud, users are advised to turn on two-factor authentication whenever possible as an added layer of protection against such attempts.