KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new browser extension called Behave! will warn you if a web site is using scripts to perform scans or attacks on local and private IP addresses on your network.
When browsing the web, scripts embedded on web pages can be used to not only port scan a visitor’s computer for open TCP ports, but also initiate attacks on other devices on your network.
In May, it was discovered that well-known sites such as eBay, Citibank, TD Bank, and more would port scan a visitor’s computer to identify Windows remote access programs running on it.
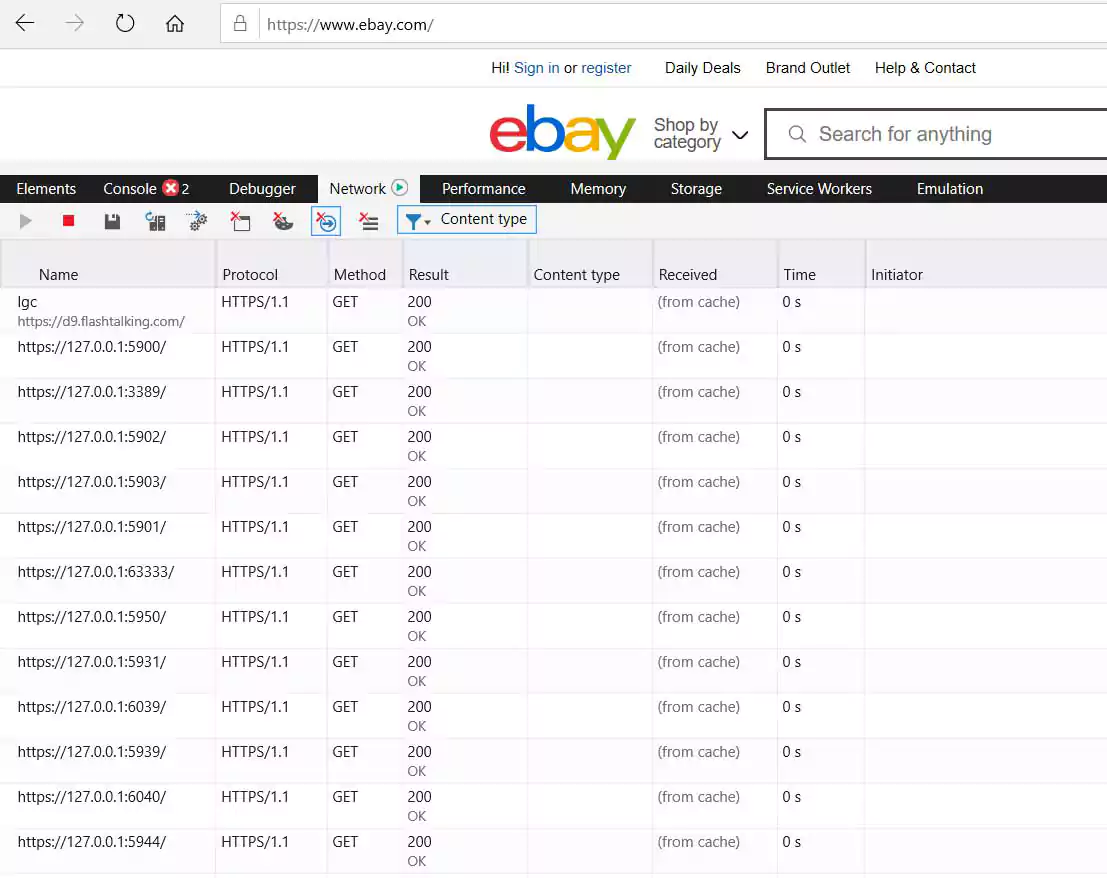
This port scanning was conducted by the LexisNexis’ ThreatMetrix fraud protection script used to detect potentially hacked computers trying to use the site.
While done for good reasons, users who are being port scanned rightfully find them intrusive and a privacy violation.
Even worse, malicious actors will also use JavaScript embedded on web sites to perform DNS Rebinding attacks.
DNS Rebinding attacks are where the DNS resolution is manipulated through short TTLs to use a victims’ computer to bypass Same Origin Policy (SOP) and launch attacks against other devices on an internal network.
These attacks are commonly used against routers, IoT devices, and even other internal computers known to run vulnerable software.
Also read: Privacy policy template important tips for your business
Created by Stefano Di Paola, co-founder, CTO, and Chief Scientist of MindedSecurity, the Behave! browser extension was born as an experiment to warn users of web sites that abuse browser features to perform local attacks or scans on a visitor’s computer
“Behave! was born as a conceptual experiment around the behavior of web pages that might abuse some of those features, and if the interest on Behave! keeps raising, it might hopefully be a long lasting project to help raising awareness.”
“For example local Port Scan, Cross Protocol attacks, DNS rebinding are very old attacks that are still possible and difficult to completely “fix” by browser vendors because they abuse core features of the Web ecosystem,” Di Paola told BleepingComputer via email.
When installed, Behave! will monitor for scripts that attempt to access IP addresses belonging to the following blocks:
If detected, the extension’s icon will show a red indicator, and when clicked on, will list the activity conducted by the site.
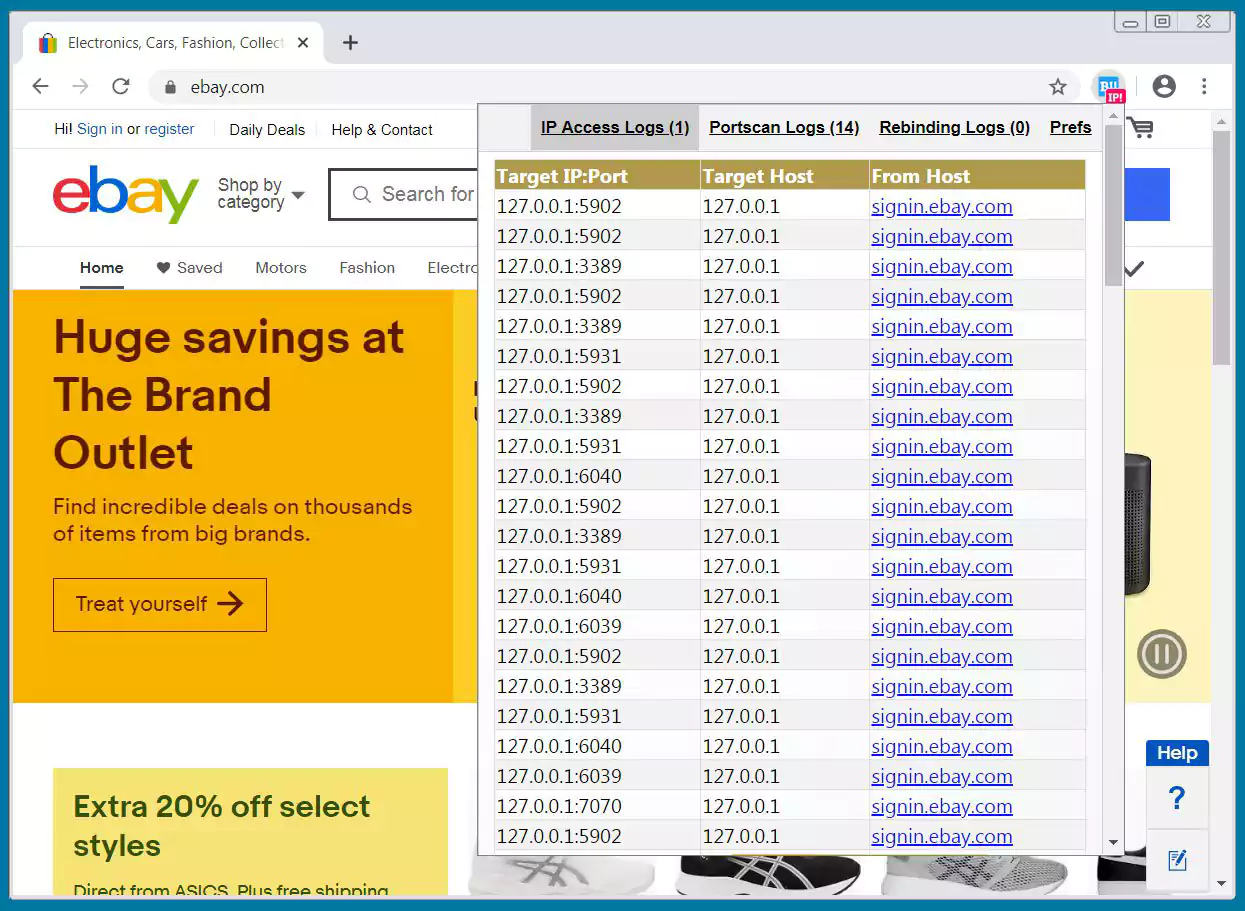
The extension can also be configured to show browser notifications when concerning behavior is detected.
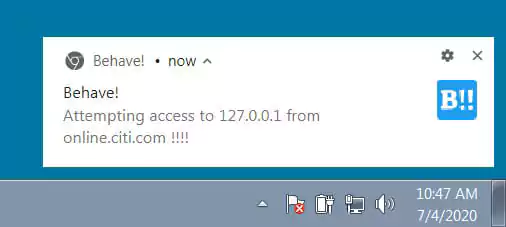
It should be noted that a bug in the extension may cause false positives on the DNS Rebinding alerts, and Di Paola has fixed the bug and waiting for Google’s approval on the new version.
The Behave! extension is available for both Chrome and Firefox, and Di Paola has told us that he hopes to release it for Edge and Safari.
Some features that Di Paola hopes to add in the future include “white listing web pages/hostnames that are expected to perform local connections” and the ability to “track back the code performing the suspicious actions.”
For those interested in being warned about potentially abusive behavior from web sites you visit, Behave! is an interesting extension to install.
Also read: 12 brief explanation about the benefits of data protection for business success