KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







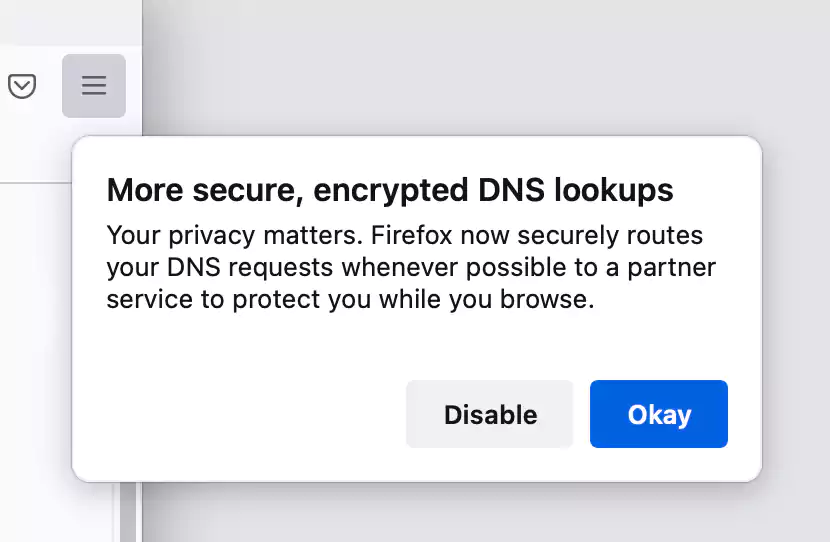
Mozilla has decided to roll out the DNS over HTTPS (DoH) feature by default for Canadian Firefox users later this month.
The move comes after DoH has already been offered to US-based Firefox users since 2020.
Mozilla Firefox users based in Canada will soon start noticing DNS over HTTPS (DoH) enabled by default, in a gradual rollout.
Starting July 20th, DoH will first be offered to 1% of Canadian Firefox users, and eventually, reach all Firefox users in Canada by September 2021.
DoH encrypts regular DNS traffic over HTTPS with both DNS requests and responses being transmitted over port 443, making the traffic blend right in with regular traffic to HTTPS websites.
This not only provides end-to-end encryption to the user but also extended privacy, as now their DNS traffic cannot easily be intercepted by a network administrator.
By contrast, standard DNS protocol functioning over UDP has no encryption, integrity assurance, or privacy protections:
“Because there is no encryption, other devices along the way might collect (or even block or change) this data too.”
“DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information,” Mozilla’s Principal Engineer, Patrick McManus had previously said.
Therefore, this initiative by Mozilla is aimed at strengthening the online security and privacy of its Canadian users.
Also Read: How Does Ransomware Work? Examples and Defense Tips
Mozilla has announced partnering with Canadian Internet Registration Authority (CIRA) as the choice of its DoH provider for Firefox Canada users, as a part of this rollout.
CIRA is the latest DoH provider, which also happens to be an internet registration authority, to join Firefox’s Trusted Recursive Resolver (TRR) program.
Previously, Cloudflare, NextDNS, and Comcast have been enrolled as Mozilla Firefox’s TRRs.
“Unencrypted DNS is a major privacy issue and part of the legacy of the old, insecure, Internet.”
We’re very excited to be able to partner with CIRA to help fix that for our Canadian users and protect more of their browsing history by default,” said Eric Rescorla, Firefox CTO.
Although DoH offers security and privacy benefits to the end-user, it is worth noting, merely being end-to-end encrypted does not alone make DoH service providers immune to abuse by adversaries.
As previously reported by BleepingComputer, attackers have very much abused Google’s own DNS-over-HTTPS service to facilitate their malware’s command-and-control (C2) activities.
Also, using DoH in corporate environments would provide network administrators with little to no visibility into DNS traffic, unless a Man-in-the-Middle (MitM) proxy was in use, at which point, the potential privacy benefits offered by DoH to the users would be stripped off.
Later this month, Firefox users in Canada will begin seeing the pop-up (shown above) starting July 20th, asking them to approve or “disable” DoH protections.
Users can also follow the below steps to switch between DoH providers, or opt-out of DoH altogether:
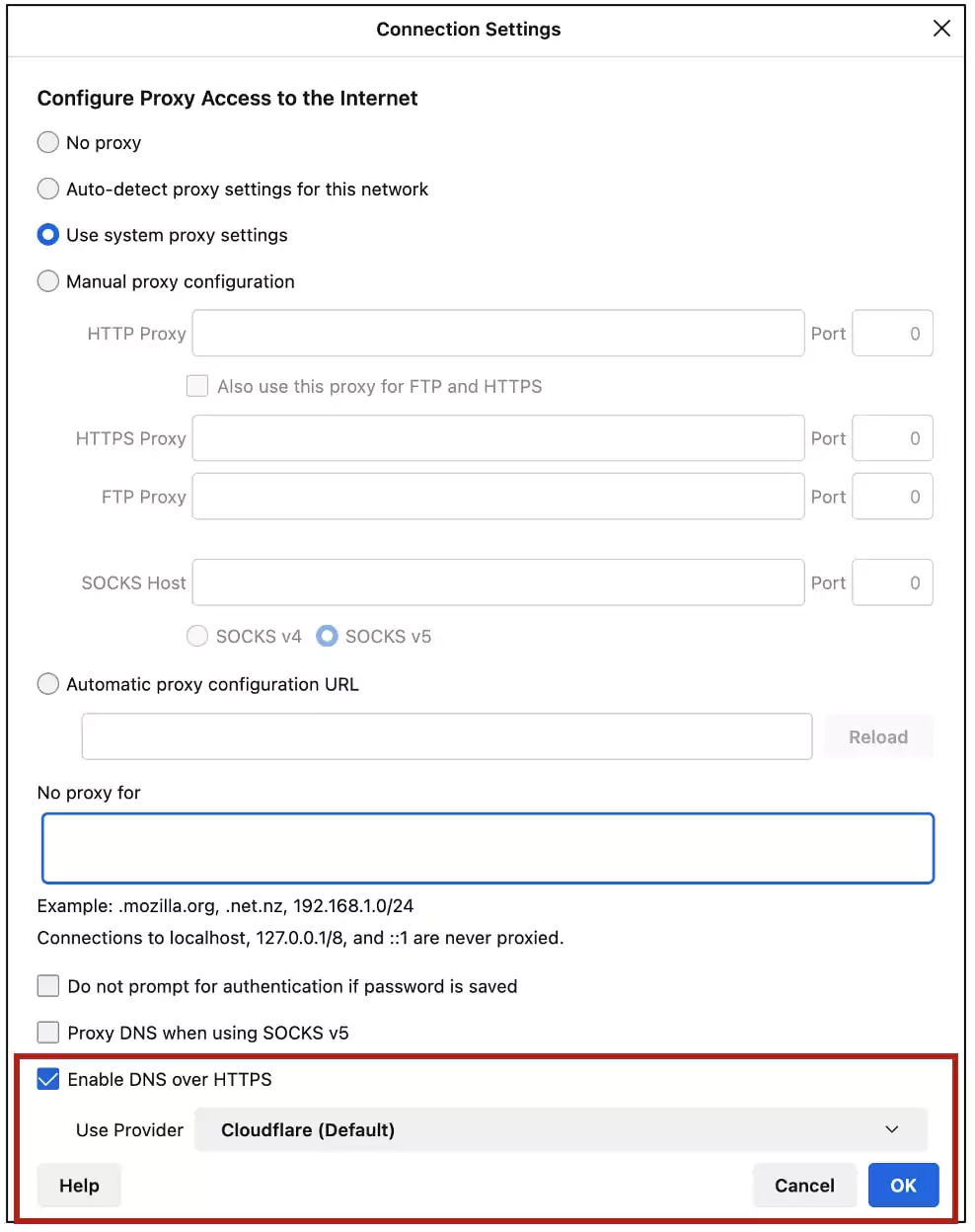
Canadian users should start seeing “CIRA Canadian Shield” listed as their default provider soon.
Users can also uncheck the box to disable DoH, or select a different DoH provider (e.g. Cloudflare or NextDNS) enrolled in Firefox’s Trusted Recursive Resolver program, from the dropdown menu.
According to Mozilla, encrypting DNS queries and responses with DoH is just a first step.
“A necessary second step is to require that the companies handling this data have appropriate rules in place – like the ones outlined in Mozilla’s TRR Program.”
“This program aims to standardize requirements in three areas: limiting data collection and retention from the resolver, ensuring transparency for any data retention that does occur, and limiting any potential use of the resolver to block access or modify content,” explains Mozilla in a blog post.
Also Read: How to Choose a Penetration Testing Vendor
By providing DoH enabled by default to users and setting out strict operational requirements for parties implementing it, Mozilla and its partners aim to enhance online user privacy.