KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







More state-sponsored hacking groups have joined the ongoing attacks targeting tens of thousands of on-premises Exchange servers impacted by severe vulnerabilities tracked as ProxyLogon.
After Microsoft’s initial report that the vulnerabilities were actively exploited by a Chinese APT group named Hafnium, Slovak internet security firm ESET shared info on at least three other Chinese-backed hacking groups abusing the ProxyLogon flaws in ongoing attacks.
Besides those three (APT27, Bronze Butler aka Tick, and Calypso), ESET also said that it also identified several “additional yet-unclassified clusters.”
In a Friday update to their announcement, Microsoft said that several other threat actors “beyond HAFNIUM” are also exploiting the four critical Exchange flaws.
Based on ESET’s (incomplete) telemetry, web shells have already been deployed on over 5,000 unique Exchange servers from over 115 countries.
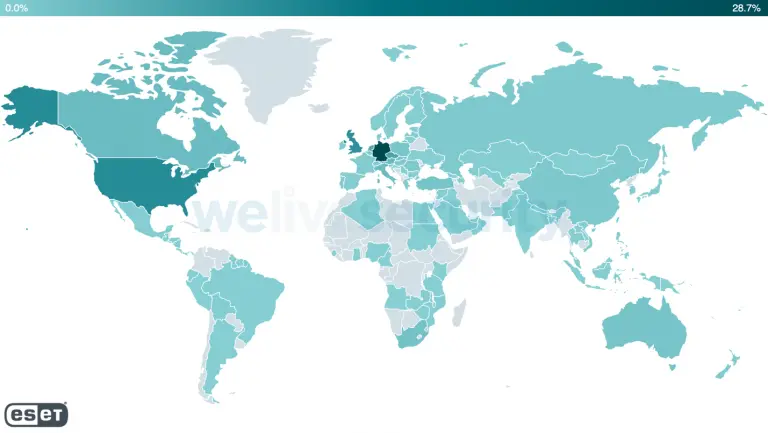
ESET has now published a new report saying that unpatched Exchange servers are currently hunted down by “at least 10 APT groups.”
On top of the previously mentioned APTs (APT27, Tick, and Calypso), ESET’s new list also includes Winnti Group (APT41), Tonto Team, Mikroceen, and a newly detected threat actor dubbed Websiic.
While analyzing telemetry data, the company has also spotted ShadowPad, “Opera” Cobalt Strike, IIS backdoor, and DLTMiner activity by unknown APT groups.
ESET also provided a short rundown of these threat groups and behavior clusters’ malicious activity:
Also Read: The DNC Registry Singapore: 5 Things You Must Know
“It is now clearly beyond prime time to patch all Exchange servers as soon as possible,” ESET concluded.
“Even those not directly exposed to the internet should be patched because an attacker with low, or unprivileged, access to your LAN can trivially exploit these vulnerabilities to raise their privileges while compromising an internal (and probably more sensitive) Exchange server, and then move laterally from it.”
Detailed info on the servers compromised by these hacking groups and the threat actors behind the not yet attributed malicious activity, including indicators of compromise, can be found in ESET’s report.
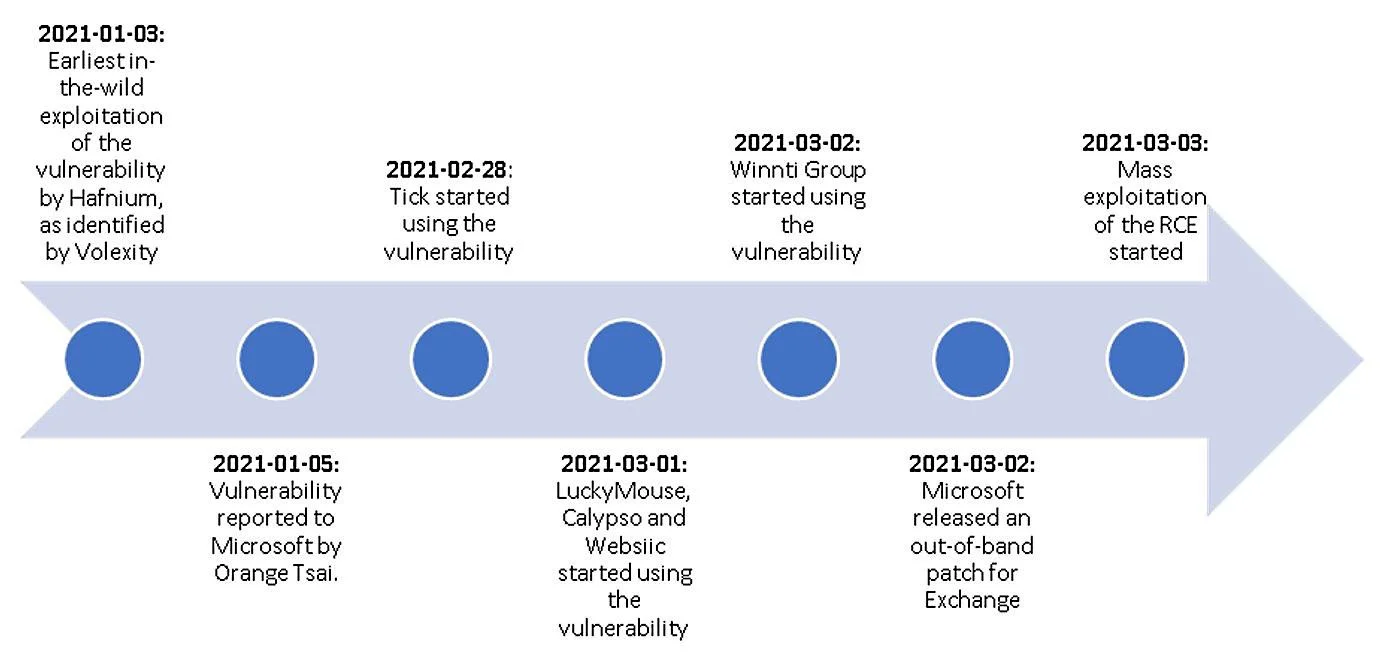
After scanning 250,000 Exchange servers worldwide, the Dutch Institute for Vulnerability Disclosure (DIVD) reported Tuesday that it found 46,000 servers unpatched against the heavily exploited ProxyLogon vulnerabilities.
The critical vulnerabilities were patched by Microsoft on March 2nd, with additional security updates issued by the company this week for multiple unsupported Exchange versions.
Redmond has also updated the Microsoft Safety Scanner (MSERT) tool to help customers detect web shells deployed in the ongoing Exchange Server attacks.
You can find additional info on installing the security updates in this article published by the Microsoft Exchange Team.
Also Read: How To Comply With PDPA: A Checklist For Businesses
If you haven’t yet patched and detect signs of compromise, you have to remove the web shells deployed by the attackers, change all credentials, and investigate additional malicious activity on your servers.