KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







While investigating a misconfiguration flaw in Apache Airflow, researchers discovered many exposed instances over the web leaking sensitive information, including credentials, from well-known tech companies.
Apache Airflow is a popular open-source workflow management platform for organizing and managing tasks.
This week, researchers Nicole Fishbein and Ryan Robinson from security firm Intezer have disclosed details on how they identified misconfiguration errors across Apache Airflow servers run by major tech companies.
The misconfiguration flaws resulted in sensitive data leakage including thousands of credentials from popular platforms and services such as Slack, PayPal, and Amazon Web Services (AWS), among others, claim the researchers:

“These unsecured instances expose sensitive information of companies across the media, finance, manufacturing, information technology (IT), biotech, e-commerce, health, energy, cybersecurity, and transportation industries,” says Intezer’s researchers.
Also Read: The Importance of Penetration Testing for Businesses
In various scenarios that researchers have analyzed, the most common reason for credential leak seen on Airflow servers was insecure coding practices.
For example, Intezer’s team discovered various production instances with hard-coded passwords inside the Python DAG code:
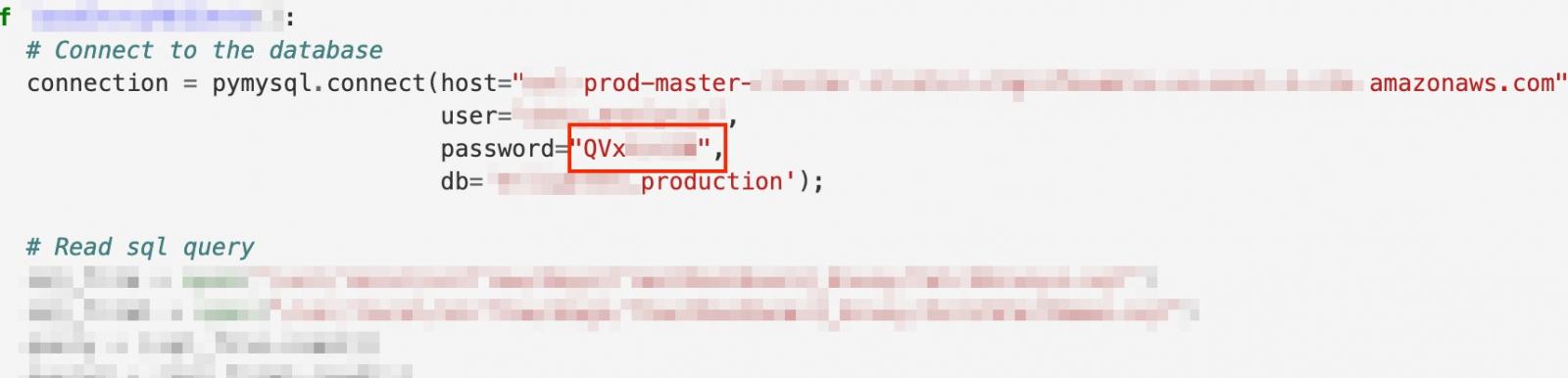
“Passwords should not be hardcoded and the long names of images and dependencies should be utilized. You will not be protected when using poor coding practices even if you believe the application is firewalled off to the internet,” warn Fishbein and Robinson.
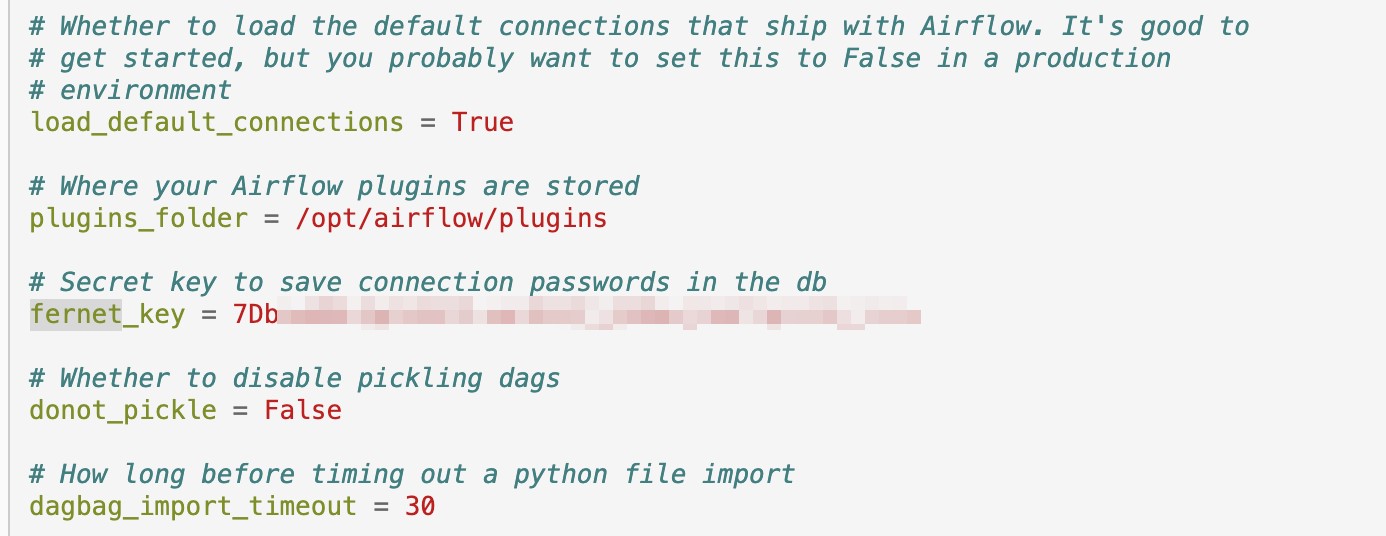
In another case of misconfiguration, researchers saw Airflow servers with a publicly accessible configuration file:
“The configuration file (airflow.cfg) is created when Airflow is first started. It contains Airflow’s configuration and it is able to be changed,” state the researchers. The file contains secrets such as passwords and keys.
But, if the `expose_config` option in the file is mistakenly set to ‘True,’ the configuration becomes accessible to anyone via the web server, who can now view these secrets.
Other examples caught in the wild included sensitive data stored in Airflow “Variables” that could be edited by an unauthorized user to inject malicious code, and the improper use of “Connections” feature—credentials stored in the unencrypted “Extra” field as JSON blobs visible to everyone.
Also Read: Free Privacy Policy Compliance Review
In addition to identifying improperly configured Airflow assets, the focus of this research was to draw attention to risks that come from delaying software updates.
Intezer states the vast majority of these flaws were identified in servers running Airflow v1.x from 2015, still in use by organizations from different sections.
In version 2 of Airflow, many new security features were introduced including a REST API that requires authentication for all operations. The newer version also doesn’t store sensitive information in logs and forces the administrator to explicitly confirm configuration options, rather than go with default ones.
Exposing customer records and sensitive data due to security flaws resulting from procrastinated patching could be in violation of data protection laws like the GDPR.
“Disruption of clients’ operations through poor cybersecurity practices can also result in legal action such as class action lawsuits,” advises the security firm.
This discovery comes just months after a misconfiguration in Argo Workflows, also discovered by Intezer, was abused by attackers to deploy cryptominers on Kubernetes clusters.
In August this year, BleepingComputer reported on cases of misconfigured buckets exposing millions of sensitive records from a secret terrorist watchlist.
Intezer states that prior to making its findings public it has notified the identified organizations and entities leaking sensitive data via vulnerable Airflow instances.
“In light of the major changes made in version 2, it is strongly recommended to update the version of all Airflow instances to the latest version. Make sure that only authorized users can connect,” advise Intezer’s researchers in their report.