KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







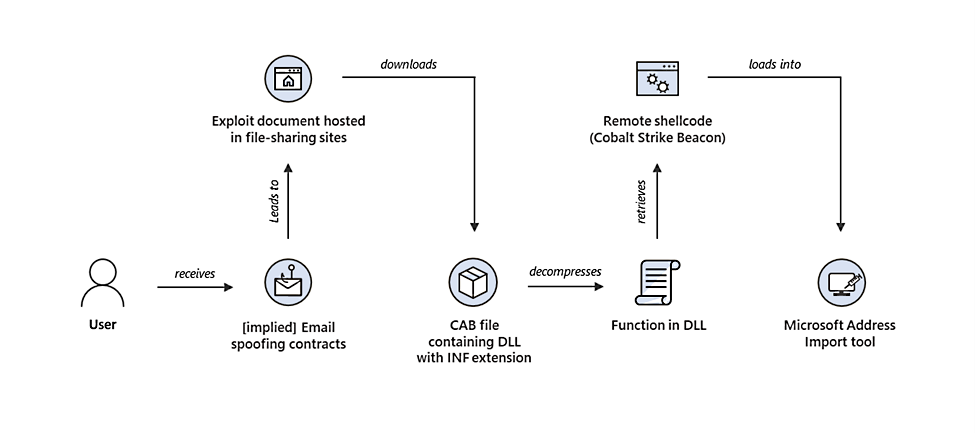
Microsoft says multiple threat actors, including ransomware affiliates, are targeting the recently patched Windows MSHTML remote code execution security flaw.
In the wild exploitation of this vulnerability (tracked as CVE-2021-40444) began on August 18 according to the company, more than two weeks before Microsoft published a security advisory with a partial workaround.
According to telemetry data analyzed by security analysts at the Microsoft 365 Defender Threat Intelligence Team and the Microsoft Threat Intelligence Center (MSTIC), the small number of initial attacks (less than 10) used maliciously crafted Office documents.
These attacks targeted the CVE-2021-40444 bug “as part of an initial access campaign that distributed custom Cobalt Strike Beacon loaders.
Also Read: The DNC Singapore: Looking At 2 Sides Better
Beacons deployed on the network of at least one victim communicated with malicious infrastructure connected with several cybercrime campaigns, including human-operated ransomware.
Some of the Cobalt Strike infrastructure used in the August CVE-2021-40444 attacks was also used in the past to deliver BazaLoader and Trickbot payloads — activity overlapping with associated with the DEV-0193 activity cluster, tracked by Mandiant as UNC1878, aka WIZARD SPIDER / RYUK according to RiskIQ.
Payloads delivered also overlapped with DEV-0365, an activity cluster associated with infrastructure possibly used as Cobalt Strike command-and-control (C2) service (CS-C2aaS) for other groups.
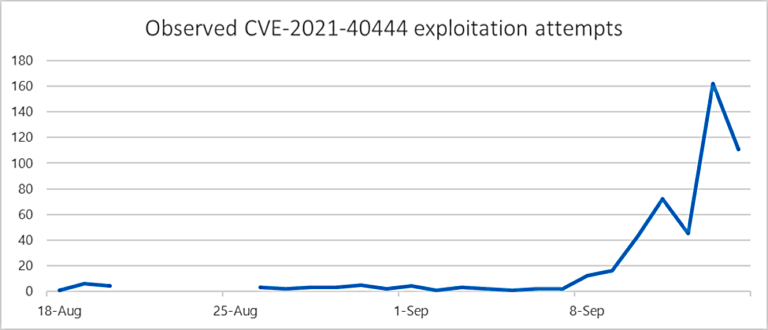
Microsoft also observed a massive increase in exploitation attempts within 24 hours after the CVE-2021-40444 advisory was published.
“Since the public disclosure, Microsoft has observed multiple threat actors, including ransomware-as-a-service affiliates, adopting publicly disclosed proof-of-concept code into their toolkits,” the researchers added.
“Microsoft continues to monitor the situation and work to deconflict testing from actual exploitation.”
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
MSTIC Threat Intelligence analyst Justin Warner added that other threat groups and actors will likely continue adding CVE-2021-40444 exploits to their arsenal in the coming days and weeks.
Microsoft recommends immediately applying the CVE-2021-40444 security updates released during the September 2021 Patch Tuesday to block incoming attacks.
CVE-2021-40444 impacts systems running Windows Server 2008 through 2019 and Windows 8.1 or later, and it has a severity level of 8.8 out of the maximum 10.
The security updates released by Microsoft address the vulnerability for all affected Windows versions and include a Monthly Rollup, a Security Only update, and an Internet Explorer cumulative update.
BleepingComputer has independently confirmed that known CVE-2021-40444 exploits no longer work after applying the September 2021 security patches.
To reduce the attack surface, customers who cannot apply the security updates should implement Microsoft’s workarounds (disabling ActiveX controls via Group Policy and preview in Windows Explorer).