KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft warns that with the shift to remote working, customers are exposed to additional security threats such as consent phishing, besides conventional credential theft and email phishing attacks.
Consent phishing is a variant of application-based attack where the targets are tricked into providing malicious Office 365 OAuth applications (web apps registered by the attackers with an OAuth 2.0 provider) access to their Office 365 accounts.
Once the victims grant the malicious apps permissions to their account data, the threat actors get their hands on access and refresh tokens that allow them to take control of the targets’ Microsoft accounts and make API calls on their behalf through the attacker-controlled app.
After the victims’ Office 365 accounts get compromised, the attackers can obtain access to their mail, files, contacts, notes, profiles, as well as sensitive information and resources stored on their corporate SharePoint document management/storage system and OneDrive for Business cloud storage space.
“While application use has accelerated and enabled employees to be productive remotely, attackers are looking at leveraging application-based attacks to gain unwarranted access to valuable data in cloud services,” Microsoft Partner Group PM Manager Agnieszka Girling said.
“While you may be familiar with attacks focused on users, such as email phishing or credential compromise, application-based attacks, such as consent phishing, is another threat vector you must be aware of.”
BleepingComputer previously reported on the inner-workings of a consent phishing attack in December 2019, explaining how this made it possible for the attackers to hijack their victims’ Office 365 accounts.
Recently, Microsoft observed multiple phishing campaigns launching consent phishing application-based attacks against its customers with the end goal of taking control of the Microsoft accounts, stealing sensitive data, and later using it to defraud organizations as part of Business Email Compromise (BEC) fraud schemes.
“Once victims clicked on the deceptive links, they were ultimately prompted to grant access permissions to a malicious web application (web app),” Microsoft Corporate Vice President for Customer Security & Trust Tom Burt said.
 Phishing email sample Phishing email sample | 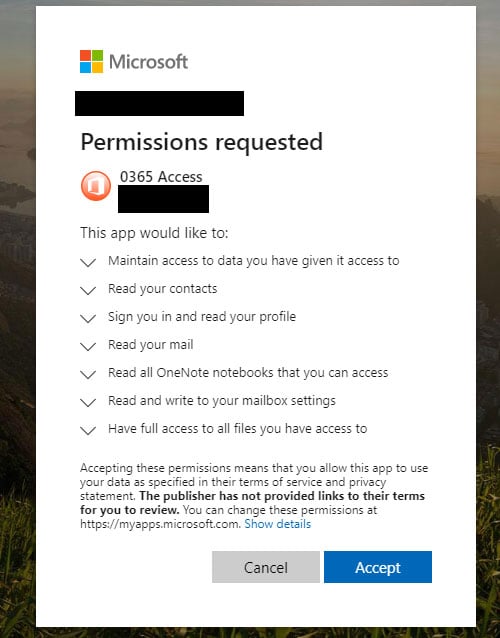 Office 365 OAuth app Office 365 OAuth app |
“Unknown to the victim, these malicious web apps were controlled by the criminals, who, with fraudulently obtained permission, could access the victim’s Microsoft Office 365 account.”
Microsoft took legal action against the threat actors that were orchestrating these attacks from the shadows, announcing the takedown of six domains (officeinvetorys[.]com, officehnoc[.]com, officesuited[.]com, officemtr[.]com, officesuitesoft[.]com, and mailitdaemon[.]com) used to host malicious Office 365 OAuth apps.
Also read: Privacy policy template important tips for your business
Besides taking legal action to take down domains used in consent phishing attacks, Microsoft also identified — by evaluating and monitoring trillions of signals — and disabled malicious Office 365 OAuth apps to block users from accessing them.
“We’re also continuing to invest in ways to ensure our application ecosystem is secure by enabling customers to set policies on the types of apps users can consent to as well as highlighting apps that come from trusted publishers,” Girling added.
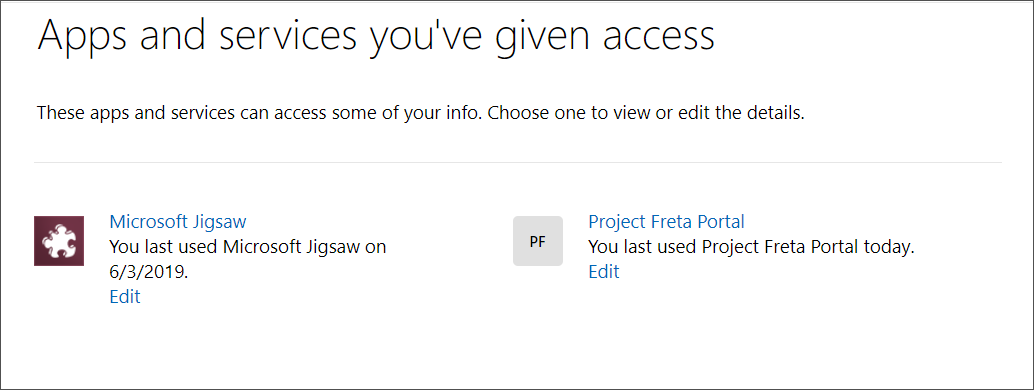
Individual users can easily check if they have any user consent apps or services tied to their accounts by going here.
To remove a listed consent, click on its entry, and on the page that opens, click on the ‘Remove these permissions’ button to remove it.
Organizations can also take severeal measures that should help them further protect their remote workforce from such attacks by educating them to spot consent phishing tactics, requiring the use of publisher verified apps, and only allow employees to OAuth apps trusted by the organization or provided by verified publishers.
Other best practices to follow when trying to protect organizations is to educate employees on how Microsoft permissions and consent framework work:• Understand the data and permissions an application is asking for and understand how permissions and consent work within our platform.
• Ensure administrators know how to manage and evaluate consent requests.
• Audit apps and consented permissions in your organization to ensure applications being used are accessing only the data they need and adhering to the principles of least privilege.
For more tips on how to defend against security threats, organizations are recommended to review the Detect and Remediate Illicit Consent Grants in Office 365 and Five steps to securing your identity infrastructure support docs.
Also read: 12 brief explanation about the benefits of data protection for business success