KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft warns of an ongoing spear-phishing campaign targeting aerospace and travel organizations with multiple remote access trojans (RATs) deployed using a new and stealthy malware loader.
“In the past few months, Microsoft has been tracking a dynamic campaign targeting the aerospace and travel sectors with spear-phishing emails that distribute an actively developed loader, which then delivers RevengeRAT or AsyncRAT,” Microsoft said.
Attackers’ phishing emails spoof legitimate organizations and use image lures posing as PDF documents containing info relevant to several industry sectors, including aviation, travel, and cargo.
As Microsoft observed while tracking this campaign, the threat actors’ end goal is to harvest and exfiltrate data from infected devices using the RATs’ remote control, keylogging, and password-stealing capabilities.
Once deployed, the malware allows them to “steal credentials, screenshots and webcam data, browser and clipboard data, system and network into, and exfiltrates data often via SMTP Port 587.”
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
The newly discovered loader monetized under a Crypter-as-a-Service model, named Snip3 by Morphisec malware analysts, is used to drop Revenge RAT, AsyncRAT, Agent Tesla, and NetWire RAT payloads on compromised systems.
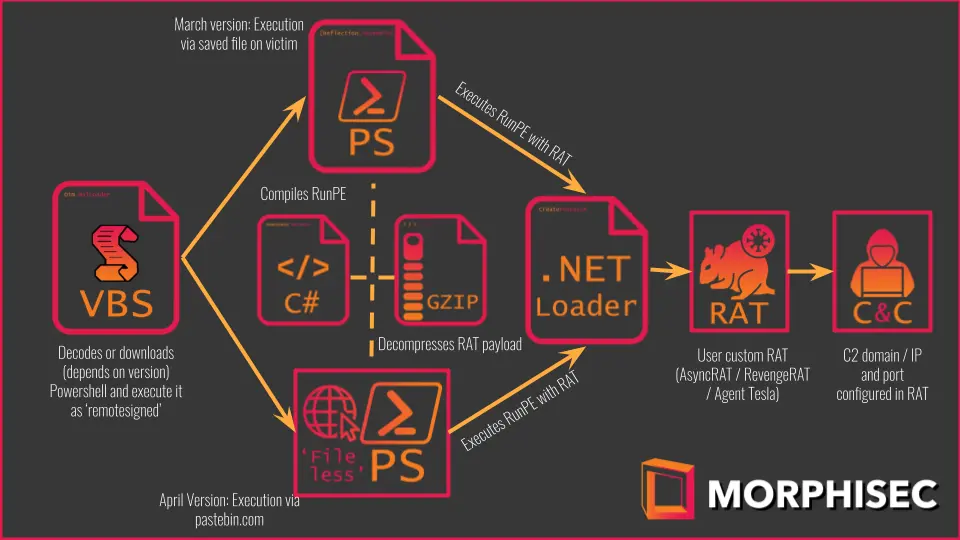
Links abusing legitimate web services and embedded within the phishing messages download the first-stage VBScript VBS files that execute a second-stage PowerShell script which in turn executes the final RAT payload using Process Hollowing.
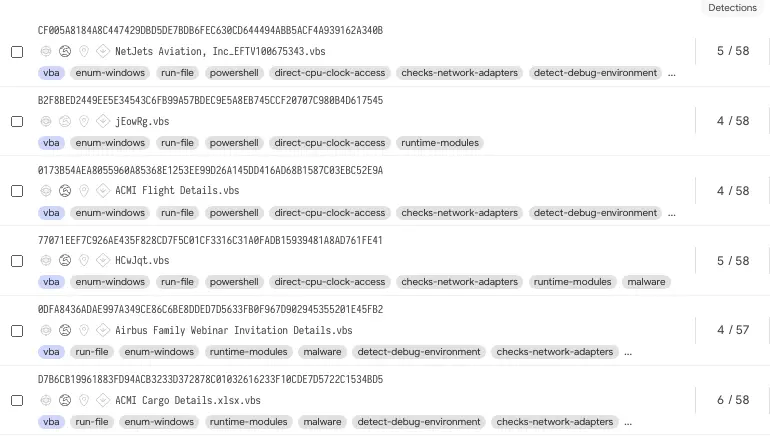
Snip3 also comes with the ability to identify sandboxing and virtual environments according to Morphisec, which makes it particularly capable of circumventing detection-centric anti-malware solutions.
To evade detection, the malware loader uses additional techniques including the
Organizations can use sample queries shared by Microsoft for advanced hunting using Microsoft 365 Defender to help them locate and investigate similar suspicious behavior related to this ongoing phishing campaign.
Also Read: 3 Reasons Why You Must Take A PDPA Singapore Course
Among the potentially malicious activity advanced hunting queries can unearth, they can help detect:
Indicators of compromise associated with this spear-phishing campaign including malware sample hashes and RAT command and control domains can be found at the end of Morphisec’s Snip3 report.