KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







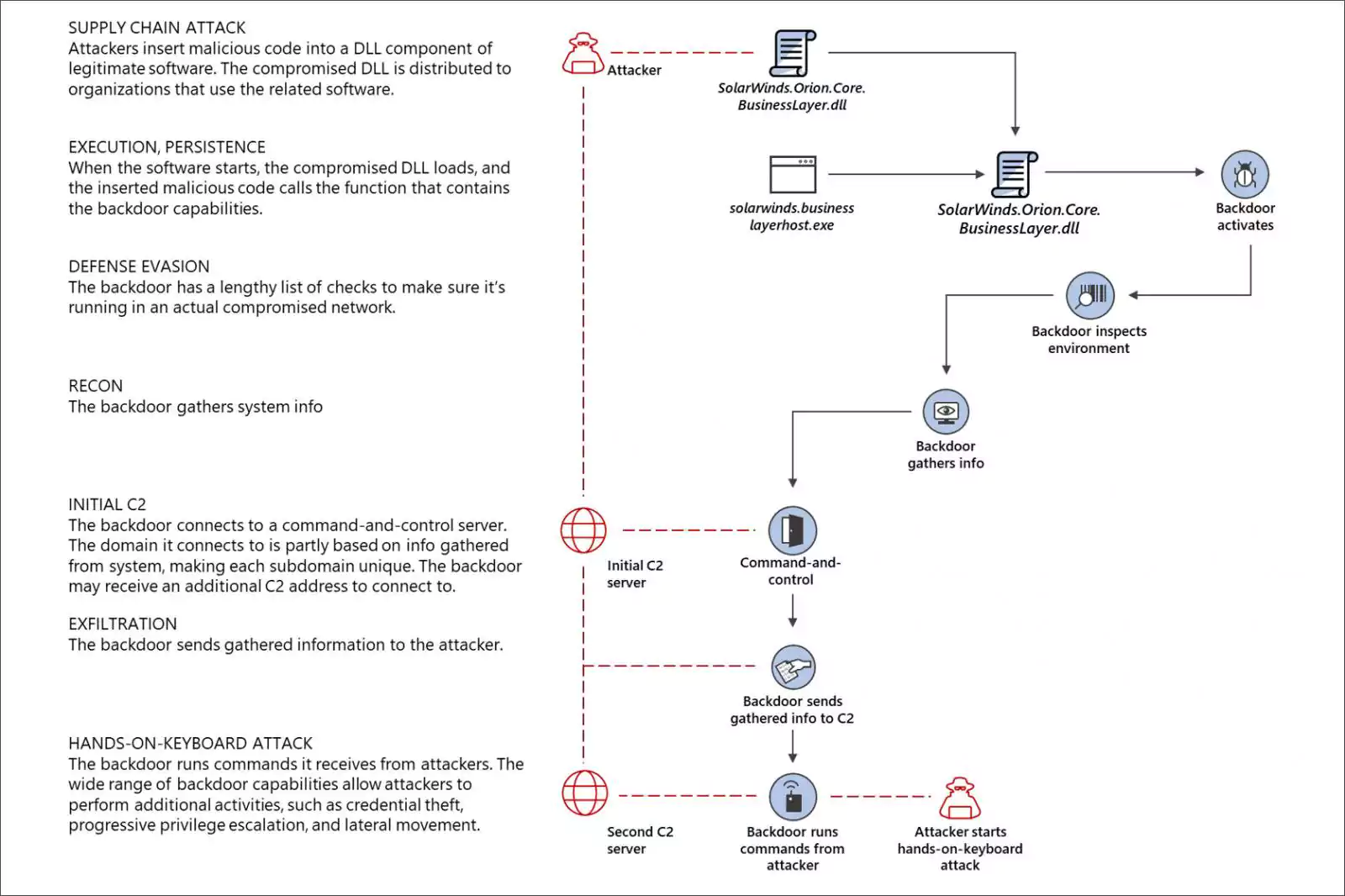
The threat actors behind the SolarWinds attack could breach internal Microsoft accounts to view the source code for Microsoft products.
Earlier this month, Microsoft confirmed that they detected malicious executables in their environment that were downloaded during the SolarWinds Orion platform supply chain attack.
Also Read: 10 Practical Benefits of Managed IT Services
In a blog post published today, Microsoft stated that they found no evidence that production services or customer data were breached, that forged SAML tokens were used against their domains, or that their systems were used to attack customers.
However, their investigations discovered that the attackers could compromise internal Microsoft accounts, with one being used to view the source code for their software. The attackers, though, did not have the required permissions to modify any source code or engineering systems.
“We detected unusual activity with a small number of internal accounts and upon review, we discovered one account had been used to view source code in a number of source code repositories. The account did not have permissions to modify any code or engineering systems and our investigation further confirmed no changes were made. These accounts were investigated and remediated,” Microsoft stated in a blog post.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
Microsoft further stated that they do not practice security through obscurity and do not consider the viewing of source code as a security risk.