KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft 365 Defender researchers have disrupted the cloud-based infrastructure used by scammers behind a recent large-scale business email compromise (BEC) campaign.
The attackers compromised their targets’ mailboxes using phishing and exfiltrated sensitive info in emails matching forwarding rules, allowing them to gain access to messages relating to financial transactions.
“The use of attacker infrastructure hosted in multiple web services allowed the attackers to operate stealthily, characteristic of BEC campaigns,” Microsoft 365 Defender Research Team’s Stefan Sellmer and Microsoft Threat Intelligence Center (MSTIC) security researcher Nick Carr explained.
“The attackers performed discrete activities for different IPs and timeframes, making it harder for researchers to correlate seemingly disparate activities as a single operation.”
Microsoft researchers revealed the entire attack flow behind a recent BEC incident, from the initial access to the victim’s mailboxes to gaining persistence and stealing data using email forwarding rules.
The login info was stolen using phishing messages that redirected the targets to landing pages closely mimicking Microsoft sign-in pages asking them to enter their passwords under a pre-populated username field.
Also Read: The DNC Singapore: Looking At 2 Sides Better
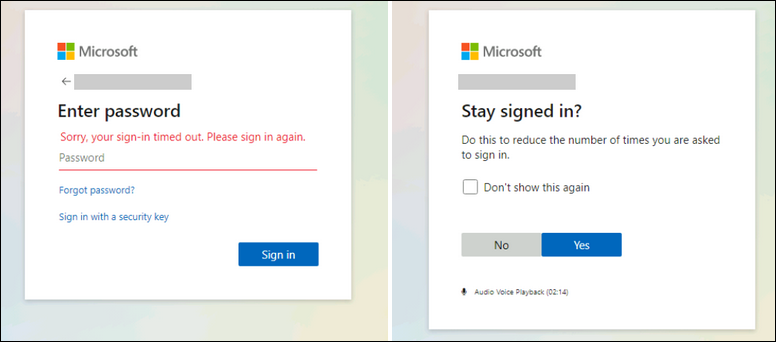
While the use of stolen credentials for compromising inboxes is blocked by enabling multi-factor authentication (MFA), Microsoft also found that the attackers used legacy protocols like IMAP/POP3 to exfil emails and circumvent MFA on Exchange Online accounts when the targets failed to toggle off legacy auth.
“Credentials checks with user agent “BAV2ROPC”, which is likely a code base using legacy protocols like IMAP/POP3, against Exchange Online,” the researchers said.
“This results in an ROPC OAuth flow, which returns an “invalid_grant” in case MFA is enabled, so no MFA notification is sent.”
The attackers also used the cloud-based infrastructure disrupted by Microsoft to automate operations at scale, “including adding the rules, watching and monitoring compromised mailboxes, finding the most valuable victims, and dealing with the forwarded emails.”
Microsoft also discovered that the scammers used BEC activity originated from multiple IP address ranges belonging to several cloud providers.
They also set up DNS records that almost matched those of their victims so that their malicious activity would blend into pre-existing email conversations and evade detection.
Even though, in some cases, BEC scammers’ methods might seem to lack sophistication and their phishing emails malicious in nature to some, BEC attacks have been behind record-breaking financial losses every year since 2018.
The FBI 2020 annual report on cybercrime for 2020 listed a record number of more than $1.8 billion adjusted losses reported last year.
Last month, Microsoft detected another large-scale BEC campaign that targeted over 120 companies using typo-squatted domains registered just a few days before the attacks began.
Also Read: 4 Best Practices on How to Use SkillsFuture Credit
In March, the FBI also warned of BEC attacks increasingly targeting US state, local, tribal, and territorial (SLTT) government entities, with reported losses ranging from $10,000 up to $4 million from November 2018 to September 2020.
In other alerts sent last year, the FBI warned of BEC scammers abusing email auto-forwarding and cloud email services like Microsoft Office 365 and Google G Suite in their attacks.