





Microsoft says the Russian-backed Nobelium threat group behind last year’s SolarWinds hack is still targeting the global IT supply chain, with 140 managed service providers (MSPs) and cloud service providers attacked and at least 14 breached since May 2021.
This campaign shares all the signs of Nobelium’s approach to compromising a significant list of targets by breaching their service provider.
Also Read: Free 8 Steps Checklist for Companies to Prevent Data Breach
Just as in previous attacks, the Russian state hackers used a diverse and ever-changing toolkit, including a long list of tools and tactics ranging from malware, password sprays, and token theft to API abuse and spear phishing.
The main targets of these new attacks are resellers and technology service providers that deploy and manage cloud services and similar tech for their customers.
Microsoft notified impacted targets of the attacks after spotting them and also added detections to their threat protection products enabling those targeted in the future to spot intrusion attempts.
“Since May, we have notified more than 140 resellers and technology service providers that have been targeted by Nobelium,” said Tom Burt, Corporate Vice President at Microsoft.
“We continue to investigate, but to date we believe as many as 14 of these resellers and service providers have been compromised.”
As Burt added, in all, more than 600 Microsoft customers were attacked thousands of times, although with a very low rate of success between July and October.
“These attacks have been a part of a larger wave of Nobelium activities this summer. In fact, between July 1 and October 19 this year, we informed 609 customers that they had been attacked 22,868 times by Nobelium, with a success rate in the low single digits,” Burt said.
Also Read: Digital Transformation – Do Or Die in 2020
“By comparison, prior to July 1, 2021, we had notified customers about attacks from all nation-state actors 20,500 times over the past three years.”
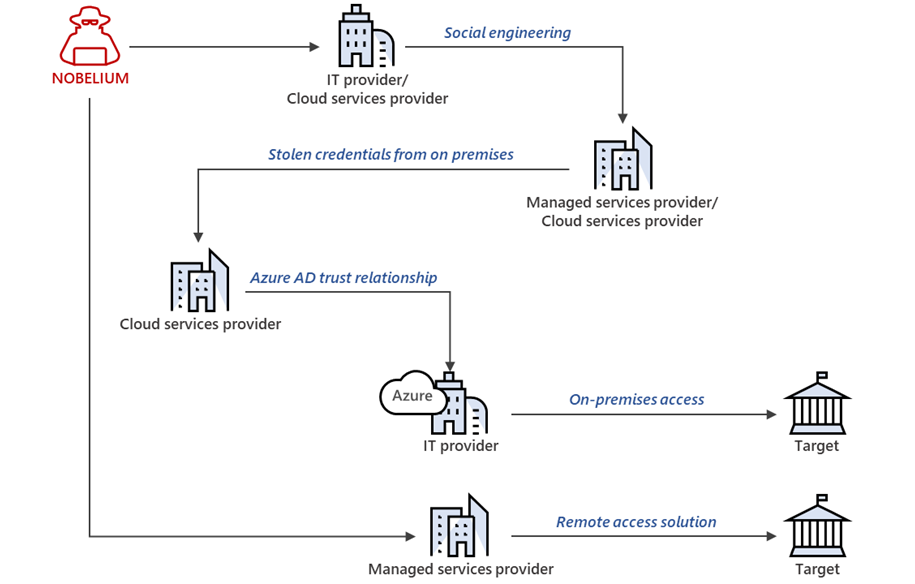
This shows that Nobelium is still attempting to launch attacks similar to the one they pulled off after breaching SolarWinds’ systems to gain long-term access to the systems of targets of interest and establish espionage and exfiltration channels.
Microsoft also shared measures MSPs, cloud service providers, and other tech orgs can take to protect their networks and customers from these ongoing Nobelium attacks.
Nobelium is the hacking division of the Russian Foreign Intelligence Service (SVR), also tracked as APT29, Cozy Bear, and The Dukes.
In April 2021, the U.S. government formally blamed the SVR division for coordinating the SolarWinds “broad-scope cyber espionage campaign” that led to the compromise of multiple U.S. government agencies.
At the end of July, the US Department of Justice was the last US govt entity to disclose that 27 US Attorneys’ offices were breached during the SolarWinds global hacking spree.
In May, the Microsoft Threat Intelligence Center (MSTIC) also reported a phishing campaign targeting government agencies from 24 countries.
Earlier this year, Microsoft detailed three Nobelium malware strains used for maintaining persistence on compromised networks: a command-and-control backdoor dubbed ‘GoldMax,’ an HTTP tracer tool tracked as ‘GoldFinder,’ a persistence tool and malware dropper named ‘Sibot.’
Two months later, they revealed four more malware families Nobelium used in their attacks: a malware downloader known as ‘BoomBox,’ a shellcode downloader and launcher known as ‘VaporRage,’ a malicious HTML attachment dubbed ‘EnvyScout,’ and a loader named ‘NativeZone.’