KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft says that Russian-sponsored hacking groups are increasingly targeting US government agencies, with roughly 58% of all nation-state attacks observed by Microsoft between July 2020 and June 2021 coming from Russia.
“Russian nation-state actors are increasingly targeting government agencies for intelligence gathering, which jumped from 3% of their targets a year ago to 53% – largely agencies involved in foreign policy, national security or defense,” said Tom Burt, Microsoft’s Corporate Vice President for Customer Security & Trust.
“And attacks from Russian nation-state actors are increasingly effective, jumping from a 21% successful compromise rate last year to a 32% rate this year.”
Also Read: 5 Common Sections in an Agreement Form Example
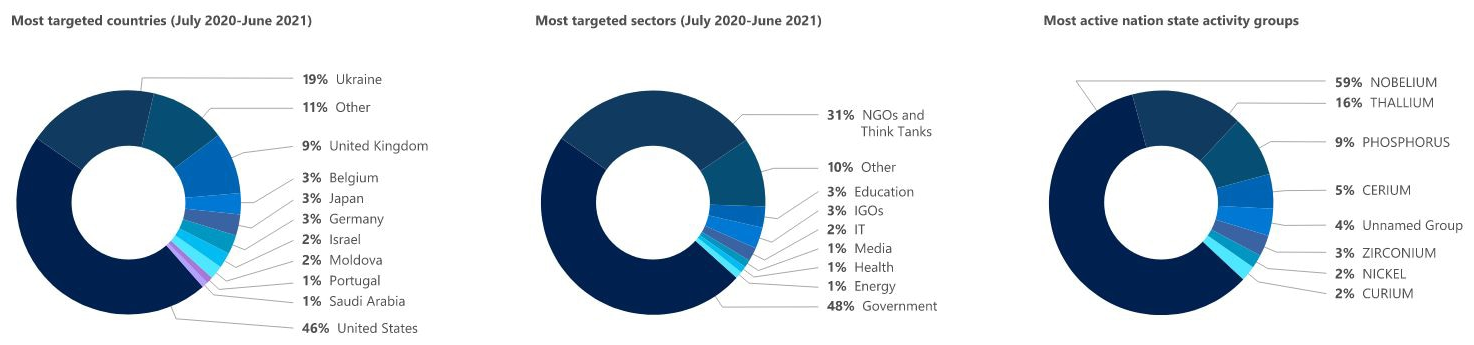
The most active Russian-backed threat actor is an activity group tracked by Microsoft as Nobelium. This group pushed Russia to the top of the countries behind cyberattacks through its aggressive targeting of Western government entities and IT service providers starting with July 2020.
In all, Nobelium has coordinated the attacks behind 92% of notifications Microsoft sent to its customers about Russia-based threat activity from July 2020 to June 2021.
This hacking group’s activity is representative of Russia’s interest in gaining access to and harvesting intelligence over running disruption operations via critical infrastructure attacks.
As Microsoft further explained, this is only a partial overview of nation-state actors’ breach attempts — Microsoft customers received 20,500 notifications about such attacks. The company still has limited insight into attacks targeting on-premises systems or systems managed by other tech vendors.
“Over the past year, Russia-based activity groups have solidified their position as acute threats to the global digital ecosystem by demonstrating adaptability, persistence, a willingness to exploit trusted technical relationships, and a facility with anonymization and open-source tools that make them increasingly difficult to detect and attribute,” Burt added.
“They have also shown a high tolerance for collateral damage, which leaves anyone with connections to targets of interest vulnerable to opportunistic targeting.”
According to Microsoft’s report, Russian-state backed hacking groups have targeted a wide range of entities worldwide:
This Thursday, Google’s Threat Analysis Group (TAG) Director of Software Engineering Shane Huntley also revealed that Google warned 14,000 of its users this month of being targeted by a state-sponsored phishing campaign from APT28 (STRONTIUM).
Also Read: Limiting Location Data Exposure: 8 Best Practices
In a statement sent to BleepingComputer, Huntley added that this APT28 phishing campaign accounted for roughly 86% of all batch warnings delivered by Google in October.
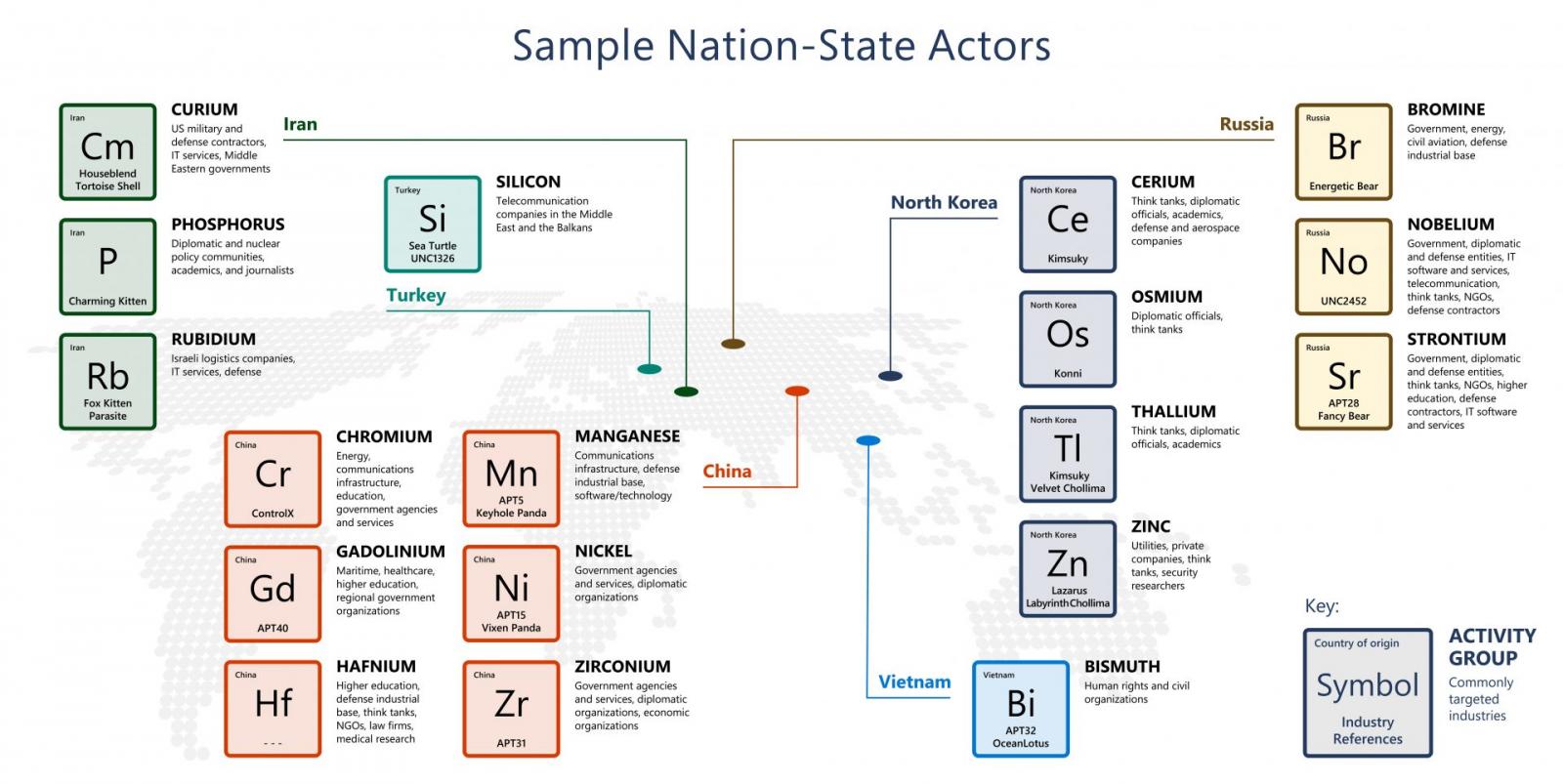
Nobelium, believed to be the hacking division of the Russian Foreign Intelligence Service (SVR), is also tracked as APT29, The Dukes, or Cozy Bear.
In April 2021, the US government formally accused this SVR division of coordinating the SolarWinds “broad-scope cyber espionage campaign” that led to the compromise of multiple US federal agencies.
Cybersecurity firm Volexity also linked the same hacking group’s operators to the SolarWinds attacks after noticing them reusing tactics from previous incidents going back to 2018.
In March, Microsoft researchers revealed three Nobelium malware strains used for maintaining persistence on compromised systems: the GoldMax command-and-control backdoor, the GoldFinder HTTP tracer tool, and the Sibot persistence tool and malware dropper.
Two months later, they detailed four more Nobelium malware families: the BoomBox malware downloader, the VaporRage shellcode downloader and launcher, the EnvyScout malicious HTML attachment, and a loader they dubbed NativeZone.