KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Bugs in the implementation of Microsoft Exchange’s Autodiscover feature have leaked approximately 100,000 login names and passwords for Windows domains worldwide.
In a new report by Amit Serper, Guardicore’s AVP of Security Research, the researcher reveals how the incorrect implementation of the Autodiscover protocol, rather than a bug in Microsoft Exchange, is causing Windows credentials to be sent to third-party untrusted websites.
Before we get to the meat of the issue, it is important to take a quick look at Microsoft Exchange’s Autodiscover protocol and how it’s implemented.
Microsoft Exchange uses an Autodiscover feature to automatically configure a user’s mail client, such as Microsoft Outlook, with their organization’s predefined mail settings.
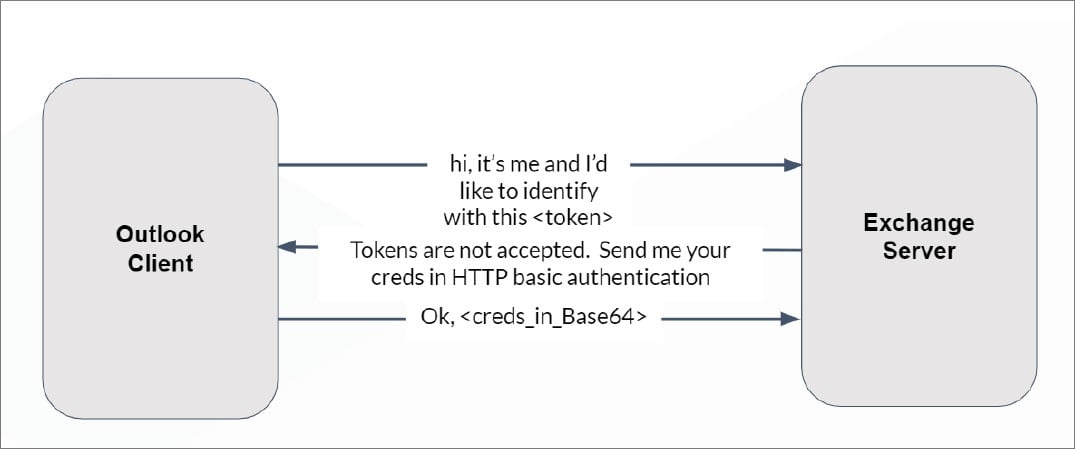
When an Exchange user enters their email address and password into an email client, such as Microsoft Outlook, the mail client then attempts to authenticate to various Exchange Autodiscover URLs.
During this authentication process, the login name and password are sent automatically to the Autodiscover URL.
The Autodiscover URLs that will be connected to are derived from the email address configured in the client.
Also Read: How Formidable is Singapore Cybersecurity Masterplan 2020?
For example, when Serper tested the Autodiscover feature using the email ‘[email protected]’, he found that the mail client tried to authenticate to the following Autodiscover URLs:
The mail client would try each URL until it was successfully authenticated to the Microsoft Exchange server and configuration information was sent back to the client.
If the client could not authenticate to the above URLs, Serper found that some mail clients, including Microsoft Outlook, would perform a “back-off” procedure. This procedure attempts to create additional URLs to authenticate to, such as the autodiscover.[tld] domain, where the TLD is derived from the user’s email address.
In this particular case, the URL generated is http://Autodiscover.com/Autodiscover/Autodiscover.xml.
This incorrect implementation of the Autodiscover protocol is causing mail clients to authenticate to untrusted domains, such as autodiscover.com, which is where the trouble begins.
As the email user’s organization does not own this domain, and credentials are automatically sent to the URL, it would allow the domain owner to collect any credentials sent to them.
To test this, Guardicore registered the following domains and set up web servers on each to see how many credentials would be leaked by the Microsoft Exchange Autodiscover feature.
After these domains were registered and used, Serper found that email clients, including Microsoft Outlook, sent many account credentials using Basic authentications, making them easily viewable.
Also Read: Going Beyond DPO Meaning: Ever Heard of Outsourced DPO?
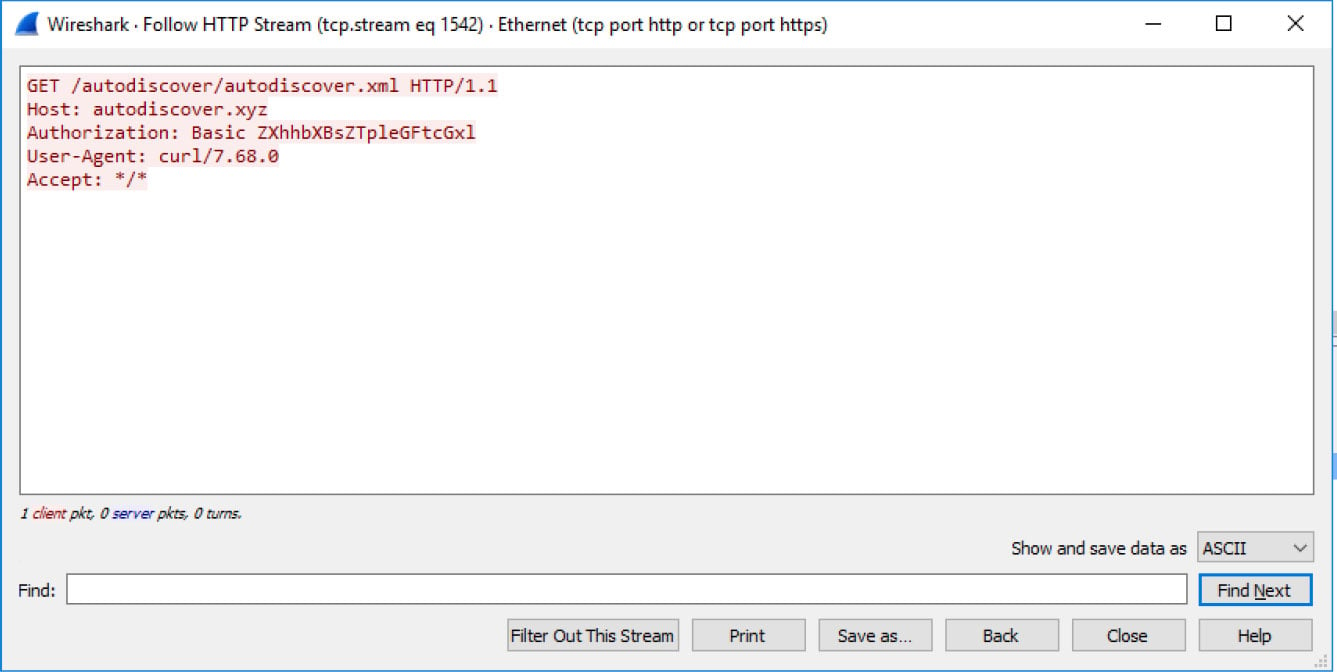
For Microsoft Outlook clients that sent credentials using NTLM and Oauth, Serper created an attack dubbed “The ol’ switcheroo” that would force the client to downgrade the request to a Basic authentication request.
This would once again allow the researcher to access the cleartext passwords for the user.
When conducting these tests between April 20th, 2021, and August 25th, 2021, Guardicore servers received a:
Guardicore says the domains that sent their credentials include:
Serper has provided a few suggestions that organizations and developers can use to mitigate these Microsoft Exchange Autodiscover leaks.
For organizations using Microsoft Exchange, you should block all Autodiscover.[tld] domains at your firewall or DNS server so that your devices cannot connect to them. Guardicore has created a text file containing all Autodiscover domains that can be used to create access rules.
Organizations are also recommended to disable Basic authentication, as it essentially sends credentials in cleartext.
For software developers, Serper recommends users prevent their mail clients from failing upwards when constructing Autodiscover URLs so that they never connect to Autodiscover.[tld] domains.
Why developers, including Microsoft, are falling back to untrusted autodiscover.[tld] domains remain a mystery, as Microsoft’s documentation on the Autodiscover protocol makes no mention of these domains.
“Many developers are just using third party libraries that all have the same problem. I’m willing to bet that the vast majority of developerss aren’t even aware of it,” Serper told BleepingComputer.
Update 9/22/21: After reaching out to Microsoft about the bug, we were provided the following statement:
“We are actively investigating and will take appropriate steps to protect customers. We are committed to coordinated vulnerability disclosure, an industry standard, collaborative approach that reduces unnecessary risk for customers before issues are made public. Unfortunately, this issue was not reported to us before the researcher marketing team presented it to the media, so we learned of the claims today.” Jeff Jones, Sr. Director, Microsoft.