KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Electronics retail giant MediaMarkt has suffered a Hive ransomware with an initial ransom demand of $240 million, causing IT systems to shut down and store operations to be disrupted in Netherlands and Germany.
MediaMarkt is Europe’s largest consumer electronics retailer, with over 1,000 stores in 13 countries. MediaMarkt employs approximately 53,000 employees and has a total sales of €20.8 billion.
Also Read: Ways to protect HR data and avoid penalties for data breaches
MediaMarkt suffered a ransomware attack late Sunday evening into Monday morning that encrypted servers and workstations and led to the shutdown of IT systems to prevent the attack’s spread.
BleepingComputer has learned that the attack affected numerous retail stores throughout Europe, primarily those in the Netherlands.
While online sales continue to function as expected, cash registers cannot accept credit cards or print receipts at affected stores. The systems outage is also preventing returns due to the inability to look up previous purchases.
Local media reports that internal MediaMarkt communications tell employees to avoid encrypted systems and disconnect cash registers from the network.
Screenshots posted on Twitter of alleged internal communications state that 3,100 servers were affected in this attack. However, BleepingComputer has not been able to corroborate those statements at this time.
Also Read: Data Protection Act of Singapore: Validity in the Post-pandemic World
BleepingComputer has confirmed that the Hive Ransomware operation is behind the attack and initially demanded a huge, but unrealistic, $240 million ransom demand to receive a decryptor for encrypted files.
Ransomware gangs commonly demand large ransoms at the beginning to allow room for negotiation and usually receive a fraction of the initial demand. However, in the attack on MediaMarkt, BleepingComputer has been told it was almost automatically reduced to a much lower amount.
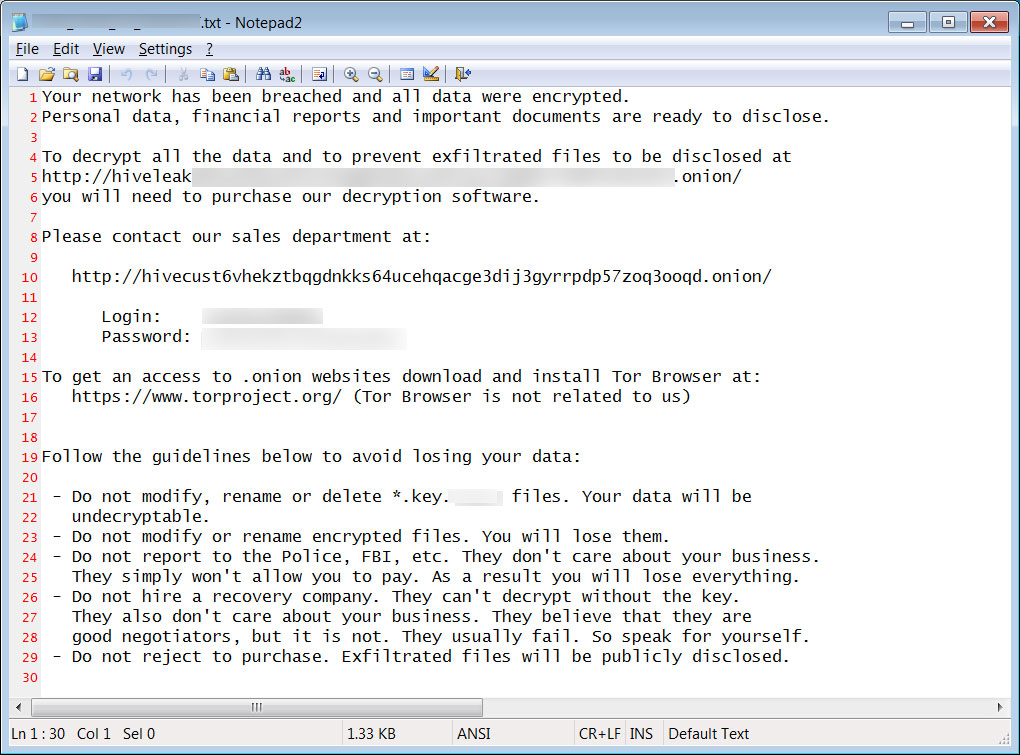
While it is not clear if unencrypted data has been stolen as part of the attack, Hive ransomware is known to steal files and publish them on their ‘HiveLeaks’ data leak site if a ransom is not paid.
When we reached out to MediaMarkt earlier today about the attack we received the following statement:
The MediaMarktSaturn Retail Group and its national organizations became the target of a cyberattack. The company immediately informed the relevant authorities and is working at full speed to identify the affected systems and repair any damage caused as quickly as possible. In the stationary stores, there may currently be limited access to some services.
MediaMarktSaturn continues to be available to its customers via all sales channels and is working intensively to ensure that all services will be available again without restriction as soon as possible.
The company will provide information on further developments on the topic. – MediaMarkt.
Hive ransomware is a relatively new operation launched in June 2021 that is known to breach organizations through malware-laced phishing campaigns.
Once they gain access to a network, the threat actors will spread laterally through a network while stealing unencrypted files to be used in extortion demands.
When they gain admin access on a Windows domain controller, they deploy their ransomware throughout the network to encrypt all devices.
The ransomware gang is known to seek out and delete any backups to prevent them from being used by the victim to recover their data.
Hive has also created variants used to encrypt Linux and FreeBSD servers, commonly used to host virtual machines.
Unlike some ransomware operations that will not encrypt healthcare institutions, nursing homes, government agencies, and other essential services, Hive ransomware does not seem to care who they target.
In August, this was shown when Hive ransomware attacked the non-profit Memorial Health System, which forced staff to work with paper charts and disrupted scheduled surgeries.
Update 11/8/21 12:01 PM EST: Added statement from MediaMarkt.
Update 11/8/21 01:53 PM EST: Added information about Hive Ransomware.