KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Multiple malware campaigns have been spotted using Pastebin-style services to facilitate their nefarious activities.
Instead of delivering payload from a dedicated Command-and-Control (C&C) server, paste sites enable attackers to hide their malicious code in plain sight.
This week Juniper Threat Labs have identified malware campaigns relying on legitimate paste services like paste.nrecom.net to host the malicious payload.
This service is based on an open-source Pastebin implementation called Strikked and has been operating since 2014.
While the paste site only supports plaintext files and not binary, any data – including binary can be encoded and represented as ASCII.
That is what malware spotted by Juniper Threat Labs was doing in this case.
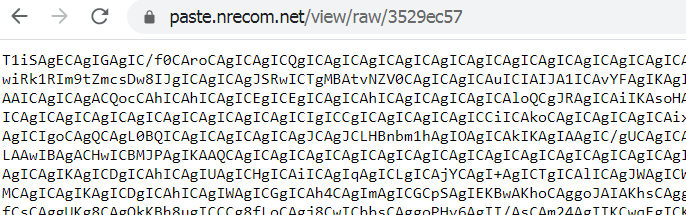
“Because it is a text-only service, one would think that it cannot host an executable file (binary data) into it,” stated Paul Kimayong, a security researcher at Juniper Threat Labs.
“However, binary data can be represented as a text file by simply encoding it. The common encoding method is using base64. That is exactly what the threat actors did in this case,” he continued.
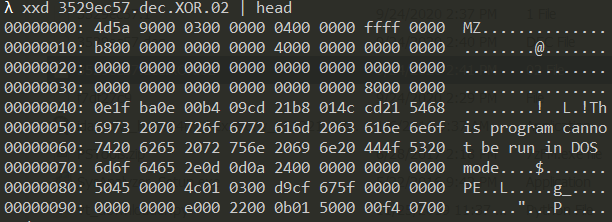
Before being base64-encoded, as shown above, the binary payload underwent an XOR encryption, to add a layer of obfuscation.
Obfuscation using XOR operations is a technique used to “scramble” the data to make it hard to decipher without knowing the correct “XOR key.”
Also Read: What is Pentest Report? Here’s A Walk-through
The malware campaigns leveraging the paste service to distribute encrypted payload include Agent Tesla, W3Cryptolocker Ransomware, Redline Stealer, and LimeRAT.
“The attack usually starts with a phishing email that includes an attachment, such as a document, archive or an executable,” explains Kimayong.
An example phishing email sent to lure victims of Agent Tesla campaign into downloading the malicious file is shown below:
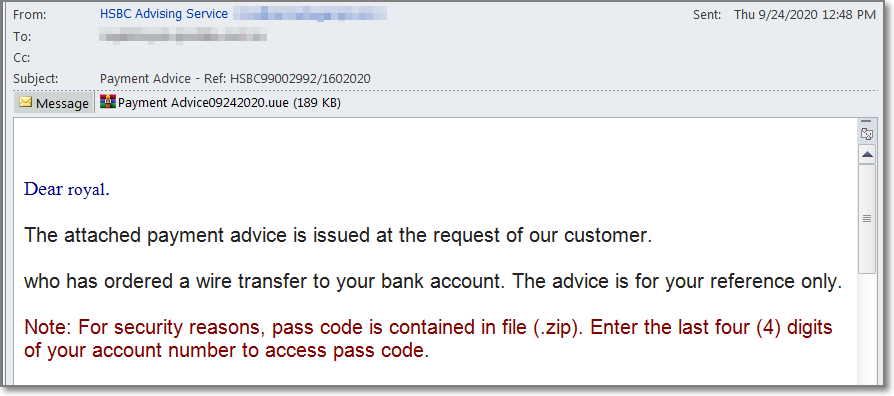
“When a user is tricked into installing the malicious attachment (first stage), it downloads the next stages from paste.nrecom.net. We have also seen malware hosting their configuration data in the same service.”
Using Pastebin-style services to host encrypted malicious code in plain sight works in the attacker’s favor as these sites cannot be easily blocked by policy due to their legitimate use-cases.
Juniper Threat Labs’ advice is to monitor traffic corresponding to the paste.nrecom website should it be malicious. Particularly, Security Operations Center (SOC) professionals should watch out for suspicious activity such as base64-encoded binary data in transit.
Juniper’s complete findings, Indicators of Compromise (IOCs), and list of malware campaigns are provided on their blog.